Import assets and identities data from Splunk ES on Splunk Cloud Platform into behavioral analytics service
Splunk Enterprise Security (ES) on Splunk Cloud Platform maintains a database of assets, such as devices, and identities, such as users, in an organization in order to enrich events during detection and investigation. For example, an event with just an IP address can be enriched to also include a host name, or an event with a just user name can be enriched to also include the user ID. See Add asset and identity data to Splunk Enterprise Security in the Administer Splunk Enterprise Security manual.
Why assets and identities data is important in behavioral analytics service
Asset and identity information from Splunk ES on Splunk Cloud Platform is important for high-quality identity resolution in behavioral analytics service. It acts as seed data to ensure that the maximum number of connections and relationships are built as quickly and as accurately as possible. Fully resolved identities make it easier to perform investigations because you do not need to spend extra time manually extracting user and device information for individual or groups of events.
Without assets and identities data from Splunk ES on Splunk Cloud Platform, user information might be missing data such as business_unit, location, managed_by, categories, start_date, end_date. Device information might be lacking information such as owner, priority, business_unit, location, and categories.
Use the Splunk Connect for Mission Control app to import assets and identities data from Splunk ES on Splunk Cloud Platform. Splunk Connect for Mission Control is an app on Splunkbase that forwards notables, artifacts, and content to Splunk Mission Control. Download the Splunk Connect for Mission Control app on Splunkbase.
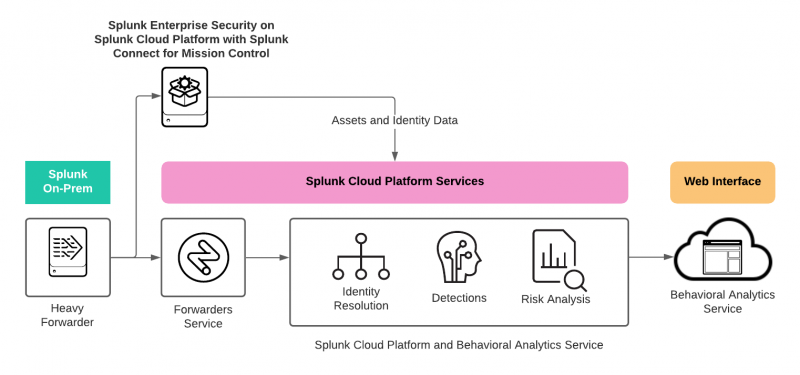
The following image summarizes how asset and identity data gets from Splunk ES on Splunk Cloud to behavioral analytics service using Splunk Connect for Mission Control.
Assets and identities data from Splunk ES on Splunk Cloud Platform gets applied only if there's a match on the IP address, MAC address, or DNS name.
Prepare to import assets and identities data from Splunk ES in Splunk Cloud Platform
Perform the following tasks before you import assets and identities data from Splunk ES into behavioral analytics service:
- Set up asset and identity data in Splunk Enterprise Security and make sure that the merge process is enabled. See Add asset and identity data to Splunk Enterprise Security in Administer Splunk Enterprise Security.
- Work with Splunk Support to install Splunk Connect for Mission Control on your Splunk Enterprise Security search head in Splunk Cloud Platform. See Install and configure Splunk Connect for Mission Control.
- Set up certificates to secure getting data into Splunk Mission Control from Splunk Enterprise Security. See Set up certificates to secure getting data into Splunk Mission Control from Splunk Enterprise Security in the Get Data into Splunk Mission Control manual.
Get asset and identity data from Splunk ES on Splunk Cloud Platform into behavioral analytics service
After you set up asset and identity data in Splunk ES on Splunk Cloud Platform and set up Splunk Connect for Mission Control, get asset and identity data into behavioral analytics service. The SA-Ingestion app in Splunk Connect for Mission Control includes scripts that run to export asset and identity data from Splunk ES on Splunk Cloud to behavioral analytics service.
You must have the proxy_admin role to perform these steps.
- On the search head with Splunk Connect for Mission Control installed, open Splunk Web. For a search head cluster, choose any search head in the cluster.
- Select Settings > Data Inputs.
- Click Asset Exporter and click Enable.
- Click Data inputs to return to the list of data inputs.
- Click Identity Exporter and click Enable.
When the scripts in the SA-Ingestion app in Splunk Connect for Mission Control run, they send data to behavioral analytics service and Splunk Mission Control. The more assets and identities that you have, the longer it takes for them to appear in behavioral analytics service.
The scripts run when they are enabled, and then once every 24 hours. If you want to send data immediately without waiting for the scripts to run on the schedule, disable and then enable the scripts again.
You can review the logs for the scripts with the following example search:
index=_internal (sourcetype="asset_exporter*" OR sourcetype="identity_exporter*")
Verify that data appears in behavioral analytics service
Perform the following tasks to verify that your data is appearing in behavioral analytics service:
- Open Splunk Mission Control.
- Click Investigations > Entities.
- Review the list of entities to verify that you see a list of assets and identities from Splunk ES on Splunk Cloud. Only entities with anomalous behavior appear in the list, so you might not see any.
- Click a specific entity to view the details and verify that enrichment details, such as the business unit for an identity, exist for that entity.
| Install and configure Splunk Connect for Mission Control | Get data into behavioral analytics service |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.0.0
 Download manual
Download manual
Feedback submitted, thanks!