Add annotations to enrich correlation search results
Ram adds annotations to enrich the results of his correlation search by adding context from industry standard cyber security mappings in Splunk Enterprise Security. Managed annotations might be based on cybersecurity frameworks such as CIS20, Kill 10, MITRE ATT&CK, and NIST. Unmanaged annotations are custom annotations that you can add to your specific use case.
- Ram decided to add MITRE ATT&CK annotations to the correlation search by scrolling down in the Edit Correlation Search window to the Annotations panel.
- Ram types T1078.004 in the MITRE ATT&CK field to align the security detection to a managed annotation based on a specific MITRE ATT&CK sub-technique.
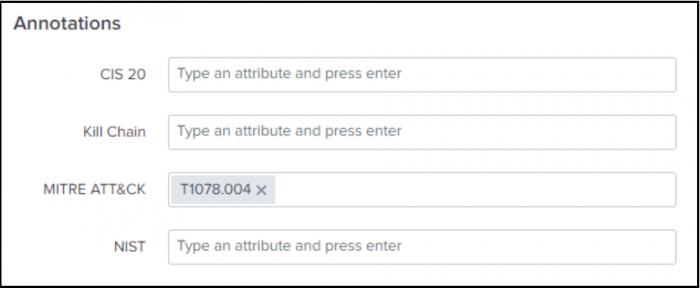
- Ram can also add custom annotations to his security detections in the SPL of the correlation search.
- Ram uses the correlation search "Risk Notable: Risk Threshold Exceeded For Risk Object Over 24 Hour Period" that he customized to identify the alerts that are generated when a user exceeds an aggregated score of 100 in a 24-hour period. Ram now has the context provided by the annotations to investigate all the factors that contributed to generating the alert.
Learn more
| Generate risk notables using correlation searches | Classify risk objects based on annotations |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.0.0
 Download manual
Download manual
Feedback submitted, thanks!