Sort notables by disposition
Ram now sorts the notables by disposition in the Incident Review page so that he can drill down on the risk notables that are tagged as True Positive - Suspicious Activity as shown in the following image.
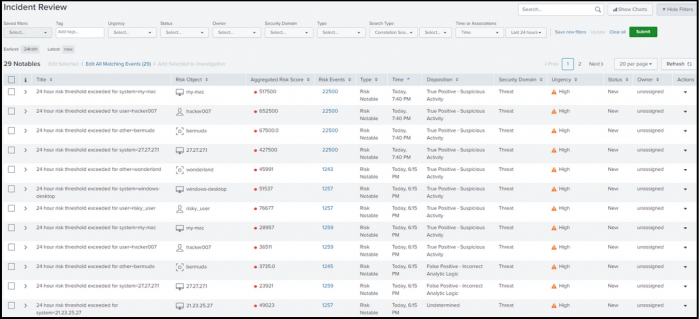
- From the Enterprise Security menu, Ram selects the Incident Review page that provides a list of notable events for the security domains.
- Ram clicks Disposition in the table to sort the notables tagged as True Positive - Suspicious Activity.
The table of notable events in the Incident Review page also lists the risk events associated with the notable.
Now Ram can focus on investigating risk notables that are grouped together as True Positive - Suspicious Activity.
| Add dispositions to risk notables | Investigate risk notables that represent a threat |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.0.0
 Download manual
Download manual
Feedback submitted, thanks!