Turn on the detection
After you have verified the results of a detection, you can turn on the detection using the correlation search editor in the Content Management page in Splunk Enterprise Security.
Follow these steps to turn on the detection:
- Use the correlation search editor to edit the search name, the app context settings, the description, and the Splunk SPL query.
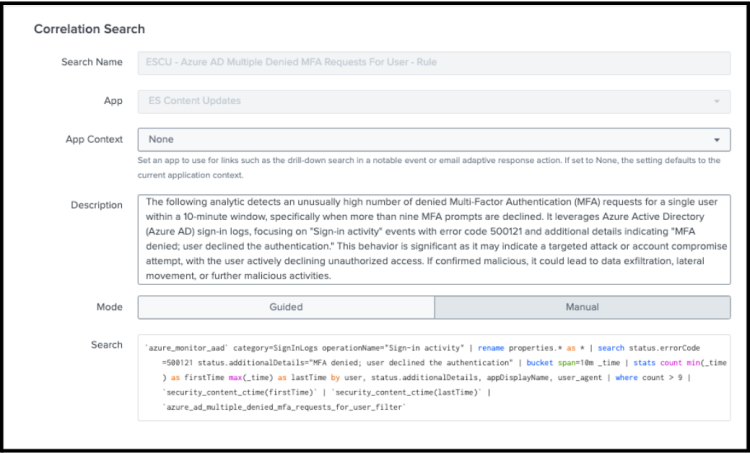
- Use the Time range section in the correlation search editor to schedule the detection. For more information, see Schedule correlation searches in Splunk Enterprise Security.
600px All ESCU detection searches include the following configurations:Timestamp Event time earliest -70m@m latest -10m@m Cron schedule 0 * * * * Scheduling Continuous Schedule window Auto Schedule priority Default - Configure the adaptive response actions that are triggered when the detection generates an alert. For example, sending email notifications, creating notables, or creating risk alerts.
- Risk alert action
- *Notable alert actions
- Annotations Relevant context to enrich your risk notables within Splunk Enterprise Security such as a specific cybersecurity framework (MITRE ATT&CK, CIS 20, or NIST Controls). You may also add your organization specific annotations in the Unmanaged Annotations section to enrich your risk notables.
| Enable detections from Analytic Stories | Use ESCU tuning and filter macros to optimize detections |
This documentation applies to the following versions of Splunk® Enterprise Security Content Update: 3.22.0, 3.23.0, 3.24.0, 3.25.0, 3.26.0, 3.27.0, 3.28.0, 3.29.0, 3.30.0, 3.31.0, 3.32.0, 3.33.0, 3.34.0, 3.35.0, 3.36.0, 3.37.0, 3.38.0, 3.39.0, 3.40.0, 3.41.0, 3.42.0, 3.43.0, 3.44.0, 3.45.0, 3.46.0, 3.47.0, 3.48.0, 3.49.0, 3.50.0, 3.51.0, 3.52.0, 3.53.0, 3.54.0, 3.55.0, 3.56.0, 3.57.0, 3.58.0, 3.59.0, 3.60.0, 3.61.0, 3.62.0, 3.63.0, 3.64.0, 4.0.0, 4.0.1, 4.1.0, 4.2.0, 4.3.0, 4.4.0, 4.5.0, 4.6.0, 4.7.0, 4.8.0, 4.9.0, 4.10.0, 4.11.1, 4.12.0, 4.13.0, 4.14.0, 4.15.0, 4.16.0, 4.17.0, 4.18.0, 4.19.0, 4.20.0, 4.21.0, 4.22.0, 4.23.0, 4.24.0, 4.25.0, 4.26.0, 4.27.0, 4.28.0, 4.29.0, 4.30.0, 4.31.0, 4.31.1, 4.32.0, 4.33.0, 4.34.0, 4.35.0, 4.36.0, 4.37.0, 4.38.0, 4.39.0, 4.40.0, 4.41.0, 4.42.0, 4.43.0, 4.44.0, 5.0.0, 5.1.0, 5.1.1, 5.2.0, 5.3.0, 5.4.0
 Download manual
Download manual
Feedback submitted, thanks!