Configure Alert Notifications using VictorOps in Splunk App for Infrastructure
VictorOps for Splunk (VictorOps) is an automated incident management software that aligns log management, monitoring, chat tools, and more to automate delivery of alert notifications. When VictorOps is integrated with Splunk App for Infrastructure, you can create and manage alerts to notify a designated person or on-call team with information about a triggered alert.
To use this feature, you must first have an installed instance of VictorOps, and configure integration with Splunk App for Infrastructure as described in this topic. To send alert notifications using VictorOps, see Send a VictorOps alert notification in Splunk App for Infrastructure.
Prerequisites
- VictorOps installed. VictorOps is available from Splunkbase at VictorOps For Splunk. Also see the Splunk App for Infrastructure VictorOps Integration Guide, which contains similar steps to what is in this section.
- VictorOps admin or user account created.
- Access to API key and Routing Key credentials from VictorOps
Configure VictorOps Integration with Splunk App for Infrastructure
1. In VictorOps, retrieve your API Key and Routing Key.
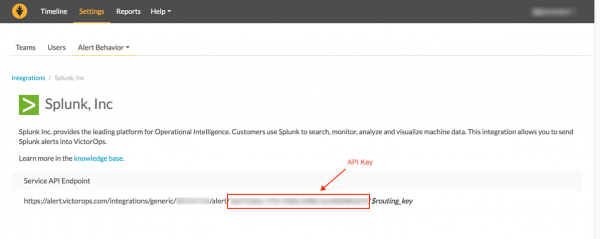
- 1a. Go to Settings > Alert Behavior > Integrations > All integrations.
- 1b. Scroll to Splunk, Inc and click the icon to enable the integration.
- 1c. After the integration is enabled, the Splunk, Inc page displays with the Service API Endpoint information and API key. The API Key is the 32 character key as shown between alert and $routing_key, as shown in the screen below. Copy and save this key.
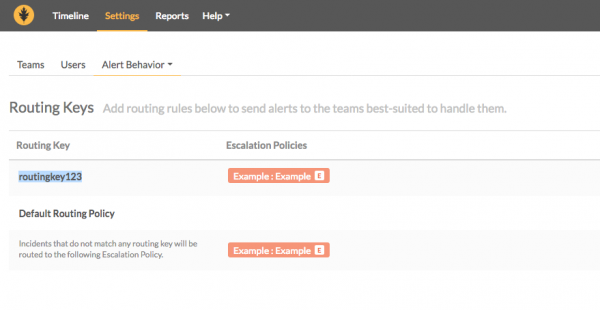
- 1d. Go to Settings > Alert Behavior > Routing Keys, and choose the routing key you want to use for this integration. Copy and save this key.
2. Store the Splunk VictorOps API Key and Routing Key in Splunk App for Infrastructure.
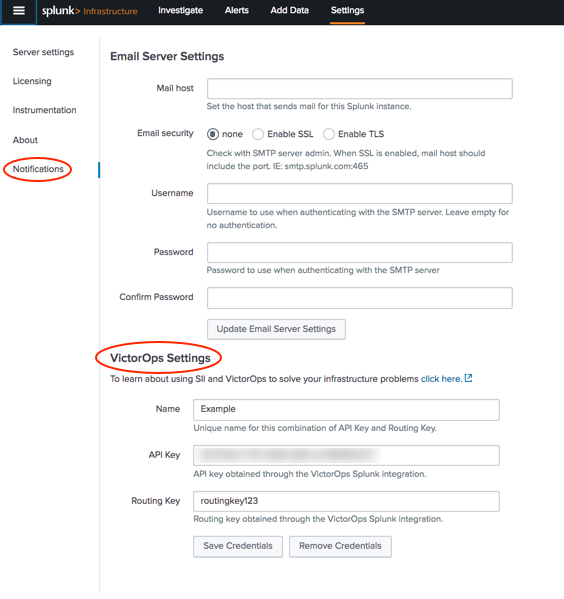
- 2a. In Splunk App for Infrastructure, go to Settings > Notifications > VictorOps Settings.
- 2b. Enter a unique Name to identify these credentials.
- 2c. Enter your Splunk VictorOps API Key.
- 2d. Enter your Splunk VictorOps Routing Key.
- 2e. Click Save Credentials. A message displays stating Success saving VictorOps settings, and a test notification is sent to your VictorOps timeline.
3. (Optional) Verify the authentication of Splunk App for Infrastructure in Splunk VictorOps.
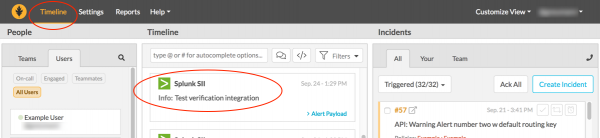
- 3a. Go to your Splunk VictorOps timeline and validate a notification from Splunk App fro Infrastructure is displaying, stating Splunk SII, Info: Test verification integration.
- 3b. If this notice is not validated, check your API Key and Routing Key and retry saving your credentials.
You are now integrated with VictorOps and can create notifications in Splunk App for Infrastructure when creating alerts.
Creating and sending a VictorOps alert notification
For information about creating and sending an alert using VictorOps, see the Send a VictorOps alert notification in Splunk App for Infrastructure in the Splunk App for Infrastructure User Guide.
Removing VictorOps credentials
You must have administrator privileges on VictorOps to remove credentials.
To remove saved VictorOps credentials from the Splunk App for Infrastructure instance, you must use the Remove Credentials button to fully remove them.
- In Splunk App for Infrastructure, go to Settings > Notifications > VictorOps Settings.
- Saved credentials display in the dialog. If you want to remove these credentials, click Remove Credentials.
- On the Remove Credentials dialog, click Remove. The VictorOps credentials are removed and you can add new credentials.
| Configure Email Notifications in Splunk App for Infrastructure | Manage Admin and User Accounts in Splunk App for Infrastructure |
This documentation applies to the following versions of Splunk® App for Infrastructure (EOL): 1.2.0
 Download manual
Download manual
Feedback submitted, thanks!