Scenario: Alex responds to a security incident in Splunk Mission Control
The following scenario features Buttercup Games, a fictitious game company.
Buttercup Games recently released the latest version of its sought-after artificial intelligence gaming software to complement one of its popular online games. Alex, a security operations center (SOC) analyst at Buttercup Games, uses Splunk Mission Control to triage, investigate, and respond to security incidents. In the first scenario, Scenario: Alex triages and investigates an improbable login in Splunk Mission Control, Alex triaged and investigated a security incident in which a user logged in from an IP address located in the United States and 10 minutes later the same user logged in from the United Kingdom. In this scenario, Alex responds to the security incident since it is highly improbable that the user traveled from the United States to the United Kingdom in 10 minutes.
Respond to a security incident
To respond to the security incident in Splunk Mission Control, Alex follows these steps:
- Alex selects the incident assigned to them and then selects Response to get started.
- To begin working on a response plan, Alex applies a response template to the incident. A response template is a set of operating procedures, or a guide with standardized tasks and phases. A response template, when applied to a specific incident, becomes a response plan. They select + Response and then choose a response template included with Splunk Mission Control.
- Alex starts a task in the response plan to validate that the same user logged in twice from two different locations. After selecting the active task, Alex expands the Respond section to browse the response options. They select the search icon (
 ) to open SPL related artifact query, the search that Wei, a SOC administrator, embedded in the response template task.
) to open SPL related artifact query, the search that Wei, a SOC administrator, embedded in the response template task. 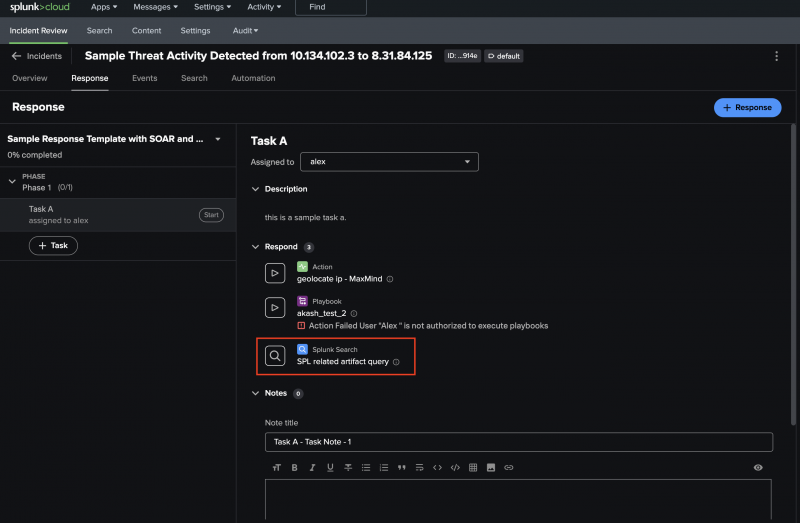
- In the Search tab, Alex locates the two events in the 10-minute time window with the same IP address but different locations. They add the two events to the incident by selecting Event actions and then Add to Mission Control incident. Saving the raw events to the incident itself helps other users understand how Alex came to the conclusion that this incident is a threat.
If Alex wants to add all of the events that the search produced to the incident, they can add the events to the incident in bulk by adding
`add_events(incident_id)`to the end of the search.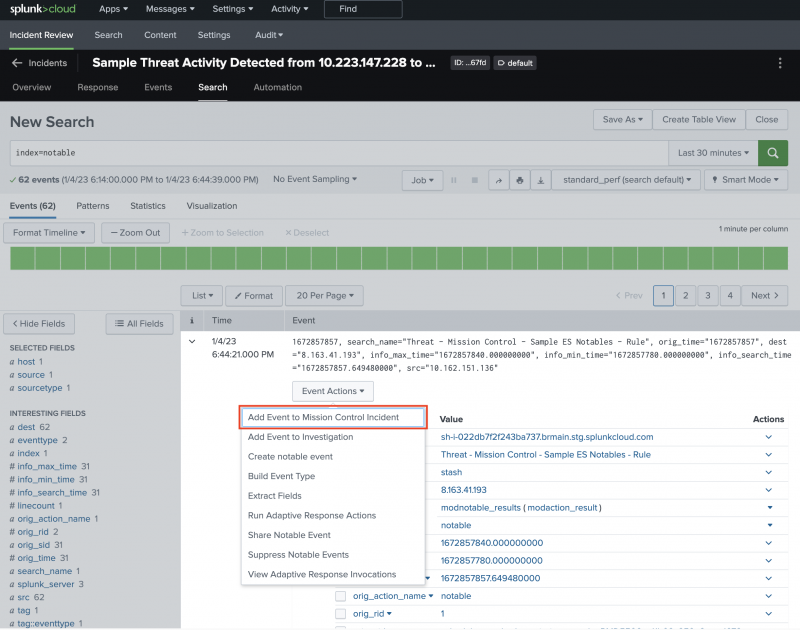
- After Alex adds the events to the incident, they return to the Response tab to end the task. They select End to complete the task.
Summary
In this scenario, Alex responded to a security incident using a response plan in Splunk Mission Control. They started a task, inspected a search added by a SOC administrator, and then added relevant events to the incident. Using a response plan allowed Alex to quickly respond to the incident in a way that is standardized by their management.
Learn more
To learn more about responding to incidents with Splunk Mission Control, see:
- Create response templates to establish guidelines for incident response in Splunk Mission Control.
- Apply response templates to standardize response to incidents in Splunk Mission Control.
- Associate an incident type with a response template in Splunk Mission Control.
- Set up actions and playbooks to run with response template tasks.
Next step
To learn how Alex automates a security workflow, see Scenario: Alex automates a security workflow in Splunk Mission Control.
| Scenario: Alex triages and investigates an incident in Splunk Mission Control | Scenario: Alex automates a security workflow in Splunk Mission Control |
This documentation applies to the following versions of Splunk® Mission Control: Current
 Download manual
Download manual
Feedback submitted, thanks!