Scenario: Alex triages and investigates an incident in Splunk Mission Control
The following scenario features Buttercup Games, a fictitious game company.
Alex is a security operations center (SOC) analyst at Buttercup Games. Buttercup Games recently released the latest version of its sought-after artificial intelligence gaming software to complement one of their popular online games. As this software is so in demand, Alex is concerned that potential bad actors might be trying to log into the Buttercup Games system to see if they can steal the technology.
While monitoring the Buttercup Games system, Alex notices that a user recently logged in from an IP address located in the United States but then 10 minutes later logged in from the United Kingdom. Since it is highly improbable that the user traveled from the United States to the United Kingdom in 10 minutes, Alex decides to do some investigating. In this example, Alex uses Splunk Mission Control to triage and investigate this improbable login.
Triage the incident
To triage the incident, Alex follows these steps:
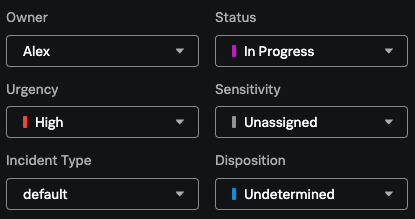
- Alex opens the Incident review page in Splunk Mission Control and filters for their assigned incidents by filtering for their name in the Owner column.
- Alex opens the most recent incident assigned to them and selects Preview.
- Alex sets the status of the incident to In Progress.
Investigate the incident
After opening the incident, Alex starts investigating.
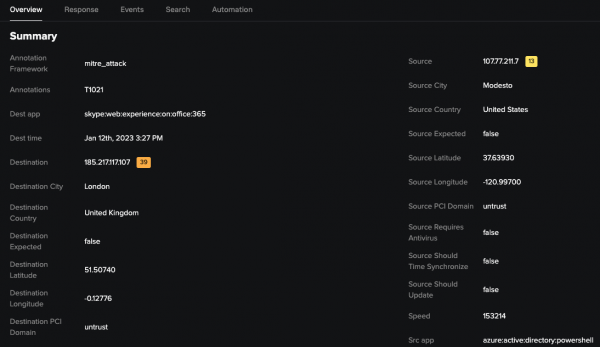
- Alex navigates to the Overview tab for the incident and starts to review the information.
- Alex reviews the IP addresses listed in the summary information for the incident and discovers the improbable login attempt. Alex analyzes various fields in the incident to support their investigation including the risk-based alerting (RBA) scores associated with each IP address.
Alex starts to plan a response to the incident.
Summary
In this scenario, Alex triaged and investigated a security incident in Splunk Mission Control. Alex filtered for incidents assigned to them, marked the incident they wanted to investigate as in progress, and reviewed the relevant incident on the Summary tab to begin investigating.
Learn more
To learn more about investigating incidents in Splunk Mission Control, see:
- Triage incidents using incident review in Splunk Mission Control
- Investigate an incident in Splunk Mission Control
Next step
To learn how Alex responds to the security incident, see Scenario: Alex responds to a security incident in Splunk Mission Control.
| Splunk Mission Control scenario library | Scenario: Alex responds to a security incident in Splunk Mission Control |
This documentation applies to the following versions of Splunk® Mission Control: Current
 Download manual
Download manual
Feedback submitted, thanks!