Mark files and events as evidence in Splunk Phantom
When you discover information that's critical to your conclusions, you can mark it as evidence in your investigation. Evidence can include files, artifacts, action results, events, and notes. Tagging evidence helps to separate general information from information that's directly related to diagnosing an incident. All evidence appears on the Evidence tab within an investigation.
Mark a file as evidence
Perform the following steps to mark a file as evidence:
- Navigate to a container in Splunk Phantom.
- Click Analyst to change the container to analyst view.
- Click the Files tab.
- Click the ... button for the file.
- Select Mark as Evidence.
- Click Confirm.
Mark an event as evidence
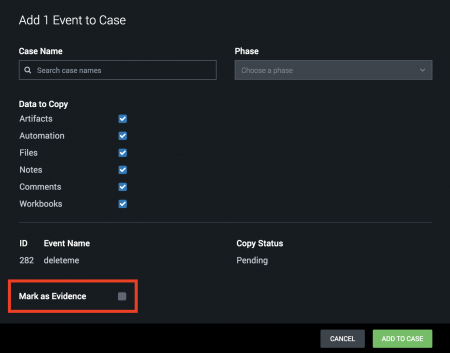
To mark an event as evidence, select Mark as Evidence when adding the event to a case. For more information about adding events to cases, see Add objects to a case in Splunk Phantom. The following screenshot illustrates how to mark an event as evidence.
When you add an event to an existing case, it copies all the data from the existing event into the case you're adding it to while also maintaining the original event data. The information on the Evidence tab is a copy of the original event, not the actual event.
| Approve actions before they run in Splunk Phantom | View recommendations for mission experts, playbooks, and actions |
This documentation applies to the following versions of Splunk® Phantom (Legacy): 4.8, 4.9, 4.10, 4.10.1, 4.10.2, 4.10.3, 4.10.4, 4.10.6, 4.10.7
 Download manual
Download manual
Feedback submitted, thanks!