Modify input settings
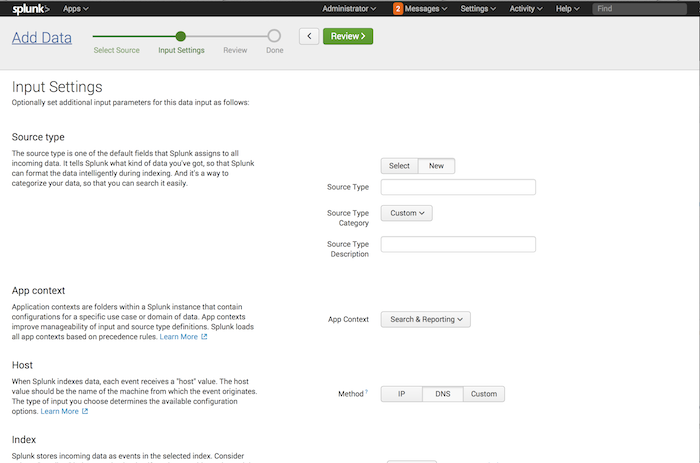
After you select the source (or set your source type when uploading or monitoring a single file), the Modify input settings page appears:
You can specify additional parameters for your data input, such as its source type, its application context, its host value, and the index where data from the input should be stored.
The following input settings are available:
Configure source type
You can specify the source type to be applied to your data with the "Source type" setting. This setting appears when:
- You specify a directory as a data source.
- You specify a network input as a data source.
- You specify a data source that has been forwarded from another Splunk instance.
If your data source does not meet these criteria, then the "Source type" setting does not appear.
Specify a source type
- Click one of the buttons.
- Select: Applies the source type you specify to the data. When you click "Select", a drop-down appears.
- New: Adds a new source type. When you click "New", two text fields and a drop-down appear.
Choose an existing source type
- From the "Select Source Type" drop-down, choose the category that best represents the source type you want.
- Choose the source type from the pop-up list that appears.
Add a new source type
- In the "Source Type" text field, enter the name of the new source type.
- Choose a category for the source type in the "Source Type Category" drop down.
- In the "Source Type Description" field, enter the description for the source type.
Configure app context
The Application Context setting determines the context in which the input should collect data. Application contexts improve manageability of input and source type definitions. App contexts are loaded based on precedence rules. See Configuration file precedence in the Admin manual.
- Select the application context you want this input to operate within by clicking the drop-down list and selecting the application context you want.
Configure host value
tags events with a host. You can configure how the software determines the host value.
- IP: Uses the IP address of the host from which the event originates.
- DNS: Use Domain Name Services (DNS). Events are tagged with the host name that Splunk software determines using DNS name resolution.
- Custom: Uses the host value you assign in the "Host field value" text box that appears when you select this option.
Index
The "Index" setting determines the index where the events for this input should be stored.
- To use the default index, leave the drop-down list set to "Default". Otherwise, click the drop-down list and select the index you want the data to go to by clicking the selection in the list.
- (Optional) If the index you want to send the data to is not in the list, and you have permissions to create indexes, you can create a new index by clicking the Create a new index button.
After you make your selections, click Next to proceed to the final step of the "Add Data" process.
| Modify event processing | Distribute source type configurations in Splunk Enterprise |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13
 Download manual
Download manual
Feedback submitted, thanks!