Add CIM-compliant data from the Splunk platform to Splunk UBA
Add CIM-compliant data mapped to security-relevant data models from the Splunk platform to Splunk UBA.
Use Splunk Direct to add a CIM-compliant data source to Splunk UBA
After you determine the Splunk UBA categories that correspond to your CIM-compliant data, add the data to Splunk UBA.
- In Splunk UBA, select Manage > Data Sources.
- Click New Data Source and complete the pages in the wizard to configure the data source.
- Step 1 of 7: Data Source Type
Select a data source type of Splunk and click Next. - Step 2 of 7: Connection
- Specify a name for the data source, such as SplunkEnterprise. The data source name must be alphanumeric with no spaces or special characters.
- Type a connection URL that matches the URL for your Splunk platform or Enterprise Security search head and management port, for example,
https://splunksearchhead.splunk.com:8089. If you have search head clustering configured and a load balancer is available, you can specify the load balancer host name to avoid a single point failure. Ensure that port 8089 is accessible on the load balancer. - Type the username and password for the Splunk platform account.
- Leave the default Connector Type of Splunk Direct.
- Click Next.
- Step 3 of 7: Time Range
- Select a time range.
- To continuously retrieve data using time-based micro batch queries, select Live and All time. See How data gets into Splunk UBA.
- To retrieve for a specific time window, select Live and Time Window and specify a time period. For example, specify 8h 30s to retrieve data for the past 8 hours and 30 seconds. This is a one-time search and is performed when the data source is added to Splunk UBA. Micro-batch queries are not used for this search.
- To add historical data from the Splunk platform, select Date Range and select a calendar date range. Only events within the specified calendar window are retrieved. This is a one-time search and is performed when the data source is added to Splunk UBA. Micro-batch queries are not used for this search.
- Click Next.
- Select a time range.
- Step 4 of 7: Events to Process
- Select the events to process. Select Splunk Query and enter a search in the field to identify the source type.
You can select Source Types to view a list of all source types from the Splunk platform. Select the check boxes for source types that all map to the same CIM data model and Splunk UBA category. For example, select three different source types of data mapped to the Malware data model that map to the Host AV category in Splunk UBA.Selecting Source Types can have a significant impact on the performance of the Splunk indexers.
- Click Next.
- Select the events to process. Select Splunk Query and enter a search in the field to identify the source type.
- Step 5 of 7: Data Format
- Select the category for the data source types that you selected.
- Review the list of field mappings to make sure that fields are correctly mapped. The wizard automatically maps a field from the Splunk platform data to the corresponding field expected by Splunk UBA if it has the same name. If needed, map the fields required by Splunk UBA to the matching fields in the Splunk platform data.
- Click Next.
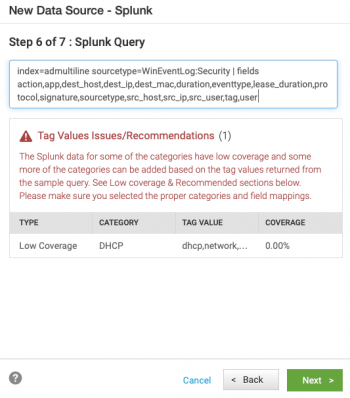
- Step 6 of 7: Splunk Query
Review the Splunk search created by the wizard. If you want, run the search in the Splunk platform to verify that the data output matches what you expect to see.
The source type in the Splunk platform appears on threats and anomalies in Splunk UBA. If you want to alias the source type to a more meaningful or accurate value, add an eval statement to the search to set the source type value to a custom value:|eval sourcetype="Your Custom Value"When creating a Splunk Direct data source with multiple formats, make sure the SPL ends with
| fields *so all fields are returned to Splunk UBA from the Splunk platform.When using Splunk Direct to create a data source, Splunk UBA performs CIM validation on a sample of events returned from the query and suggests the categories you should select based on the tags observed, specifies the coverage percentage, and provides recommendations. In this example, the DHCP category was selected in the previous step but Splunk UBA's CIM validation shows that there is no coverage for this category based on sample events. In this situation, return to the previous screen and remove DHCP as a category.
If Splunk UBA detects full coverage on the sample events, no message is displayed.
- Step 7 of 7: Test Mode
To add the data source in test mode, leave the check box selected. See Add data sources to Splunk UBA in test mode. - Click OK to save the data source.
You can select multiple sourcetypes and map the sourcetypes to multiple categories. It is a good idea to start by mapping one category at a time because mapping fields can be complex when attempting to map different types of data at the same time.
Use Splunk Direct to add all CIM-compliant data sources to Splunk UBA
If all of your data sources are CIM-compliant, you can add them all to Splunk UBA together. Select the CIM Compliant checkbox in the Connection page to have Splunk UBA generate a query that will pull all events from all indexes in your Splunk platform instance.
If you want to pull all events from all indexes, you must meet these conditions:
- Work with a Splunk UBA customer support representative to make sure all of your data sources are verified CIM compliant. Any events that are not CIM compliant are dropped.
- After the search is run, there are fewer than 10,000 events per second returned.
To add all of your CIM-compliant data sources to Splunk UBA together, perform the following tasks:
- In Splunk UBA, select Manage > Data Sources.
- Click New Data Source and complete the pages in the wizard to configure the data source.
- Step 1 of 5: Data Source Type
Select a data source type of Splunk and click Next. - Step 2 of 5: Connection
- Specify a name for the data source, such as SplunkEnterprise. The data source name must be alphanumeric, with no spaces or special characters.
- Type a connection URL that matches the URL for your Splunk platform or Enterprise Security search head and management port (for example:
https://splunksearchhead.splunk.com:8089). If search head clustering is configured and a load balancer is available, you can specify the load balancer host name to avoid a single point of failure. Ensure that port 8089 is accessible on the load balancer. - Type the username and password for the Splunk platform account.
- Leave the default Connector Type of Splunk Direct.
- Select the CIM Compliant checkbox to ingest all your CIM compliant data as a single source and automatically parse events based on the value in the
tagfield.
Verify the quality of the data and CIM compliance before using the CIM Compliant option; data that is not CIM compliant is dropped. You can create multiple CIM compliant data sources and edit the query so that each data source only ingests a subset of the data from all Splunk indexes. - Click Next.
- Step 3 of 5: Time Range
- Select a time range.
- To continuously retrieve data using time-based micro batch queries, select Live and All time. See How data gets into Splunk UBA.
- To retrieve for a specific time window, select Live and Time Window and specify a time period. For example, specify 8h 30s to retrieve data for the past 8 hours and 30 seconds. This is a one-time search and is performed when the data source is added to Splunk UBA. Micro-batch queries are not used for this search.
- To add historical data from the Splunk platform, select Date Range and select a calendar date range. Only events within the specified calendar window are retrieved. This is a one-time search and is performed when the data source is added to Splunk UBA. Micro-batch queries are not used for this search.
- Click Next.
- Select a time range.
- Step 4 of 5: Splunk Query
Review the Splunk search created by the wizard. If you want, run the search in the Splunk platform to verify that the data output matches what you expect to see.- The query represents all of the data sources found in your environment, so you can edit it to include only the data sources that are verified CIM compliant.
- If the query results exceed 10,000 events per second, you can create multiple, smaller data sources using any subset of queries for each data source.
Click Next.
- Step 5 of 5: Test Mode
To add the data source in test mode, leave the check box selected. See Add data sources to Splunk UBA in test mode. - Click OK to save the data source.
Monitor and verify your data
After you add a CIM-compliant data source using the Splunk Direct connector, you can perform any of the following tasks for verifying your data source:
- Examine some sample events to make sure that the fields are being parsed correctly. See Verify that you successfully added the data source.
- If any events have field values that can't be accepted by Splunk UBA, the events may be dropped and therefore not used by any data models. See Monitor the quality of data sent from the Splunk platform.
- Check the status of your data sources. See Review and edit existing data sources in Splunk UBA.
- See if there are any data sources that are missing fields, thus preventing detections from being activated in Splunk UBA. See Validate data availability.
| Which Windows events are used by Splunk UBA? | Add raw events from the Splunk platform to Splunk UBA |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.0.0, 5.0.1, 5.0.2, 5.0.3, 5.0.4, 5.0.4.1, 5.0.5, 5.0.5.1, 5.1.0, 5.1.0.1
 Download manual
Download manual
Feedback submitted, thanks!