Customize anomaly scoring rules
You can customize the scoring rules for anomalies in Splunk UBA.
Anomaly scores are derived from a variety of factors and conditions defined in a rule. Customizing the scoring rules means you can provide a level of consistency in how anomalies in your environment are scored. For example, the Excessive Data Transmission anomaly is triggered based on the following rules:
- Analysis of Baseline
- Analysis of Peer Group
- Analysis of Transfer
As an example, you can change the scoring rules for this anomaly by elevating the threshold for the Analysis of Peer Group rule and generating a higher anomaly score only when the threshold for this rule is exceeded. This particular rule is also used to score other anomalies, like Excessive Box Downloads. By making the same changes to this rule for all anomalies, you can create consistency in your environment in terms of which factors are emphasized to generate the anomalies and threats you want to see.
Viewing the scoring rules also provides insight into the constitution of each anomaly, and help you understand how to modify the scoring rules based on your needs.
You can also change the scoring ranges for the anomalies themselves, to emphasize certain types of anomalies over others. For example, you may change all anomalies related to data exfiltration to have a higher maximum score than any other anomalies in your system to ensure that threats generated by data exfiltration anomalies will also have higher scores and be prioritized accordingly.
A summary of each anomaly's scoring rules can be viewed in the Score Details pane on the Anomaly Details page. See Review the anomaly details.
View and understand anomaly scoring rules
To view the scoring rules associated with each anomaly, perform the following tasks:
- In Splunk UBA, select Anomalies from the home page, or select Explore > Anomalies from the menu bar.
- Click the anomaly rules (
 ) icon.
) icon. - Click Anomaly Scoring Rules.
- Select an anomaly from the list of anomalies to view the scoring rules.
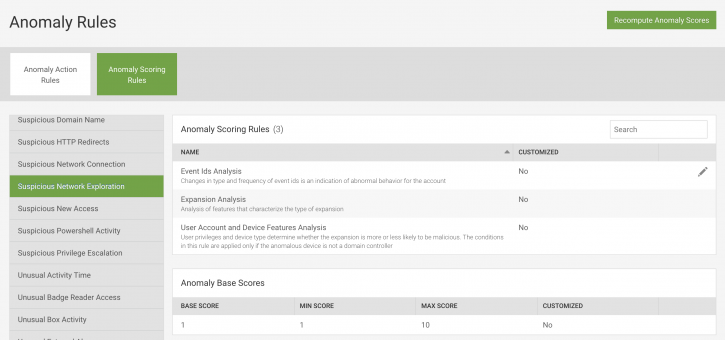
Click on each anomaly name to view the scoring rules for that anomaly. The example below shows the Suspicious Network Exploration anomaly:
View the scoring rules for this anomaly in the Anomaly Scoring Rules section. Scores for the Suspicious Network Exploration anomaly are based on the following rules:
- Event Ids Analysis
- Expansion Analysis
- User Account and Device Features Analysis
Each rule listed also contains a brief description about the rule. The "No" in the Customized column means that the scoring rule has not been edited and is the same as originally shipped with Splunk UBA.
View the base scores for the anomaly in the Anomaly Base Score section. Every anomaly consists of a base, minimum, and maximum score value. These are described in the following table.
| Score Type | Description |
|---|---|
| Base Score | Every anomaly has a base score, which is derived from analyzing the events in your system to find anomalous indicators. Scoring rules add additional context and related metadata to the base score.
|
| Min Score | Lowest score that this anomaly can have. |
| Max Score | Highest score that this anomaly can have. |
The final anomaly score is a value between the minimum score and the maximum score.
Customize the anomaly scoring rules
To customize the scoring rules for an anomaly, perform the following tasks:
- In Splunk UBA, select Anomalies from the home page, or select Explore > Anomalies from the menu bar.
- Click the anomaly rules (
 ) icon.
) icon. - Click Anomaly Scoring Rules.
- Select an anomaly from the list of anomalies to view the scoring rules.
- Hover over the rule name on the Anomaly Scoring Rules page and click on the edit (
 ) icon.
) icon.
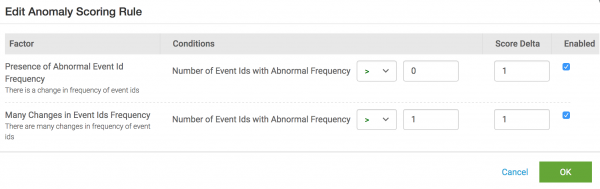
The example below shows the details for the Event Ids Analysis scoring rule.
The items on this page are described in the following table:
| Column | Description |
|---|---|
| Factor | Name and brief description of the factor contributing to the rule. |
| Conditions | The thresholds that determine when the score for the anomaly is changed. This field contains a variety of formats, depending on the nature of the condition. In this example, we can make the following changes:
|
| Score Delta | The amount to increase or decrease the score if the specified condition is met.
In cases with multiple scores, there is an implied AND condition. In this example, if both Presence of Abnormal Event Id Frequency and Many Changes in Event Ids Frequency are triggered, the anomaly score is incremented by 3. You can disable the Presence of Abnormal Event Id Frequency by deselecting the checkbox in the Enabled column, so that when the Many Changes in Event Ids Frequency threshold is crossed, the anomaly score is incremented by 2. |
| Enabled | Make sure the checkbox is selected to have this rule condition be active. Deselect it to make the condition inactive. |
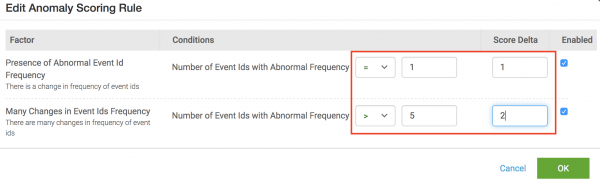
The image shows what the rule looks like after the changes.
Customize the anomaly base, minimum, and maximum scores
To customize scoring for the anomaly, perform the following procedure:
- In Splunk UBA, select Anomalies from the home page, or select Explore > Anomalies from the menu bar.
- Click the anomaly rules (
 ) icon.
) icon. - Click Anomaly Scoring Rules.
- Select an anomaly from the list of anomalies to view the scoring rules.
- Hover over the row with the anomaly scores and click the edit (
 ) icon.
) icon. - In the Edit Anomaly Base Scores window, change the anomaly scores as desired.
- Click OK.
Recomputing anomaly scoring rules
After you finish editing the anomaly scoring rules, click Recompute Anomaly Scores on the Anomaly Rules page to have your changes take effect. This can take up to several hours, depending on the number of anomalies in your system. Splunk UBA maintains an internal versioning system for all anomaly rules that determines which version of a rule to use when recomputing anomaly scores after edits are made, or Splunk UBA is upgraded.
The internal versioning system contains a major and minor version number.
- The major version number is updated as needed whenever Splunk UBA is upgraded
- The minor version number is updated whenever a scoring rule is edited.
All anomalies generated and added to the system will use the scoring rules of the latest major and minor version. For example, when a Suspicious Network Exploration anomaly is generated, it will be scored based on the latest major and minor version of the scoring rule for this anomaly.
The following table summarizes what happens to the existing anomaly scores in your system when you make changes to a scoring rule, or upgrade Splunk UBA.
| Event | Impact on anomaly scores |
|---|---|
| You edit an anomaly scoring rule. | The minor version number for that anomaly is updated. All past anomalies with the same major version and lower minor version number are recomputed, except for anomalies that were scored by an anomaly action rule which is still an active rule. If there are existing anomalies of this type that use an older scoring model (earlier than Splunk UBA 4.2.0), those anomalies are not recomputed. In addition, any new anomalies generated based on the old scoring model are also not re-scored. |
| You upgrade Splunk UBA. | If a scoring rule for a particular anomaly is updated as part of a Splunk UBA release, then the major version number for that anomaly is updated. All customizations for previous versions of the same anomaly are lost. |
Reverting anomaly score rules
You can revert an anomaly scoring rule back to the Splunk UBA default values. If you choose to do this, all of your customizations will be lost.
To revert an anomaly scoring rule back to the Splunk UBA default:
| Take action on anomalies with anomaly action rules | Mask personally-identifiable information in Splunk UBA |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.0.0, 5.0.1, 5.0.2, 5.0.3, 5.0.4, 5.0.4.1, 5.0.5, 5.0.5.1, 5.1.0, 5.1.0.1
 Download manual
Download manual
Feedback submitted, thanks!