Risk Analysis
The Risk Analysis dashboard displays the recent changes to risk scores and the objects that have the highest risk score. As an analyst, you can review this dashboard to assess the relative change in risk scores and examine the events that contributed to an object's risk score.
Risk scoring
A risk score is a single metric that shows the relative risk of a device or user object in the network environment over time. An object represents a system, a user, or an un-classified other.
In Enterprise Security, assets and identities are the context that machine data sources are applied to. These objects are your users and networked devices. Correlation searches are the tool used to correlate data sources to an asset or identity by searching for a conditional match to a question. An alert is created when the correlation search matches. The alert can generate a notable event, a risk modifier, or both.
- A notable event becomes a task. It is an event that must be assigned, reviewed, and closed.
- A risk modifier becomes a number. It is an event that will add to the risk score of the device or user objects.
See Configure Risk Scoring in the Installation and Configuration manual.
Risk scoring example
The host RLOG-10 is a jump server that is generating several notable events. The correlation searches Excessive Failed Logins, and Default Account Activity Detected are creating one notable event a day for that system. As RLOG-10 is a jump server, there are many network credentials being used against this host, and software or other utilities may have been installed. In aggregate, this behavior seems less interesting then if the same behavior occurred on the production DNS server. It's tempting to ignore or suppress notable events coming from any host that's a known jump server due to the relative noise created. You need to know the host is being monitored, but would prefer it was measured under a different set of rules.
One solution is a new correlation search that assigns a risk modifier when the correlation matches on hosts that serve as jump servers.
- Use a whitelist to isolate the jump servers from the existing correlation searches.
- Create and schedule a new correlation search based on Excessive Failed Logins, but isolate the search to the jump server hosts and assign a risk modifier alert type only.
- Verify the risk modifiers are applied to the jump server hosts, raising their risk score incrementally. With the new correlation search, no notable events will be created for those hosts based upon failed logins.
As the relative risk score goes up, RLOG-10 can be compared to all network servers and to other jump servers. If the relative risk score for RLOG-10 exceeds its peers, that host would be investigated by an analyst. If the risk scores of all jump servers are higher relative to other network hosts, an internal security policy may need to be reviewed or implemented differently.
- See the Risk Analysis With Enterprise Security 3.1 blog post for additional examples.
Use the Risk Analysis dashboard
An analyst uses the Risk Analysis dashboard to review changes to an object's risk score, determine the source of the risk increase, and decide if additional action is warranted.
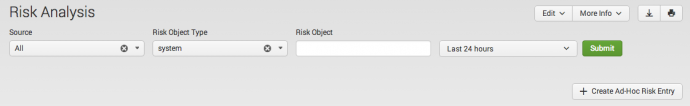
Dashboard filters
Use any of the four available filters on the Risk Analysis dashboard to search and filter the results. The filter is applied to all panels in the dashboard.
| Filter by | Description | Action |
|---|---|---|
| Source | Filter by the correlation search that has risk modifiers | Drop-down: select to filter by |
| Risk Object Type | A reverse lookup by the object type and risk object. Requires an entry in the Risk Object field. Defaults to system. | Drop-down: select to filter by |
| Risk Object | Filter by string. Only works against the defined Risk Object Type. | Text field. Wildcard with an asterisk (*) |
| Time | Select a time range to filter results | Drop-down: select to set time-range |
The Risk Object Type and Risk Object are one filter, and work together. When the two are properly defined, the search begins with a reverse lookup against the Assets and Identities tables to find all fields that have been associated with the Risk Object. All associated objects found will have their risk results returned and displayed in addition.
Example: Defining a Risk Object Type of system and a Risk Object of 10.10.1.100, the reverse lookup against the assets table could return a MAC address. The Risk Analysis dashboard will update to display any risk score applied to the 10.10.1.100 address and a MAC address. If no match to another object was found in the asset table, only the IP address matches from the Risk Analysis data model will be displayed.
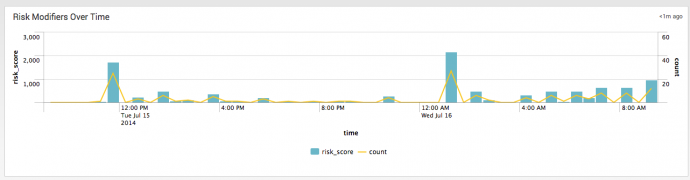
Risk Modifiers Over Time
This timeline view displays the changes made by risk modifiers over time. Use the filters to scope the view to a specific object or group of objects. Use the drilldown to explore the data as events.
Drilldown
The drilldown displays events from the Risk data model. Some of the interesting fields are the same fields used in the primary views on the Risk Analysis dashboard:
| Risk data model field | Description |
|---|---|
| Source | The correlation search name that applied risk modifiers. A full description appears as All_Risk.description |
| dest | Depending upon the correlation search, an object the risk modifier is applied to. The object also appears as All_Risk.risk_object |
| src | Depending upon the correlation search, an object the risk modifier is applied to. The object also appears as All_Risk.risk_object |
See Risk Analysis data model in the Installation and Configuration manual.
Additional Risk Score Views
The Risk Analysis dashboard offers three additional views to assist in analyzing risk scoring changes and what was responsible for making the changes. Use the filters to scope the view to a specific object or group of objects. Use the drilldown to explore the data as events.
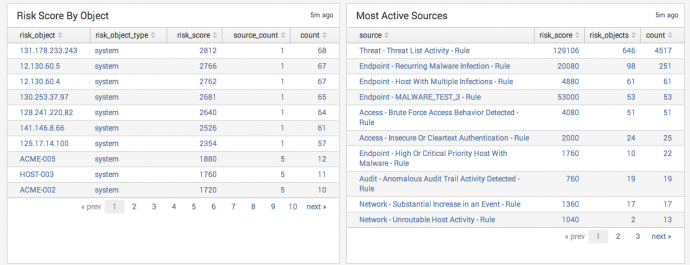
Risk Score By Object
Displays the objects with the highest risk score. Drilldown is scoped to the risk object.
Most Active Sources
Displays the correlation searches that contributed the highest amount risk to any object. Drilldown is scoped to the source search.
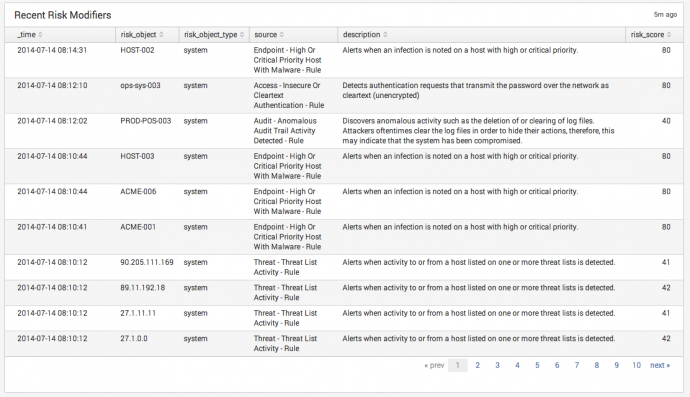
Recent Risk Modifiers
Displays the most recent changes in a risk score, the source of the change, and the object.
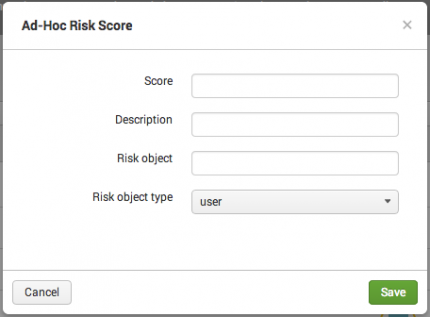
Create Ad-Hoc Risk Entry
An ad-hoc risk entry is a method to make a manual adjustment to an object's risk score. It is used to add a positive or negative number to the risk scores of objects as a one time task.
| Ad-hoc Risk Score field | Description |
|---|---|
| Score | The number added to a Risk object. Can be a positive or negative integer. |
| Description | A reason or note for manually adjusting an object's risk score. The Description field is mandatory for an ad-hoc risk score. |
| Risk object | Text field. Wildcard with an asterisk (*) |
| Risk object type | Drop-down: select to filter by. |
| Event Investigator dashboards | Advanced Threat dashboards |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.1, 3.1.1, 3.2, 3.2.1, 3.2.2
 Download manual
Download manual
Feedback submitted, thanks!