Investigate episodes in ITSI
After you finish triaging episodes, begin your investigation. Use the available fields on an episode to assess the urgency, contributing KPIs, and impacted entities associated with the episode.
Select an episode to open the episode details and learn more about the episode.
- Use the Impact tab to view the services, KPIs, and entities that were impacted by the episode. Services are sorted by health score and KPIs are sorted by alert level. Select an impacted service or KPI to open it in Service Analyzer. The Impacted Entities section shows the highest outstanding event for each entity.
- Use the Events Timeline tab to see when individual events within the episode occurred.
- Review the Common Fields tab to see the fields shared by all events in the episode.
- Review the Comments tab to see comments other analysts left about the episode or leave your own comment. To add the same comment to multiple episodes, hold Shift and select the episodes, then click Add Comment.
- Review the Activity to see the recent investigation activity on the episode.
- Use the All Events tab to see the individual notable events contained within the episode and a chart with event severity levels over time. For information on configuring drilldowns from this table, see the Notable Events section of the correlation search configuration.
If service level permissions are enabled for Episode Review, you only see the events you have permission to view in the All Events tab. If there are any events you do not have permission to view, the number of events you see is less than the number in the episode event count.
Any notable events that ITSI generates during a Splunk Enterprise restart are backfilled into episodes after restart.
See a timeline of individual events
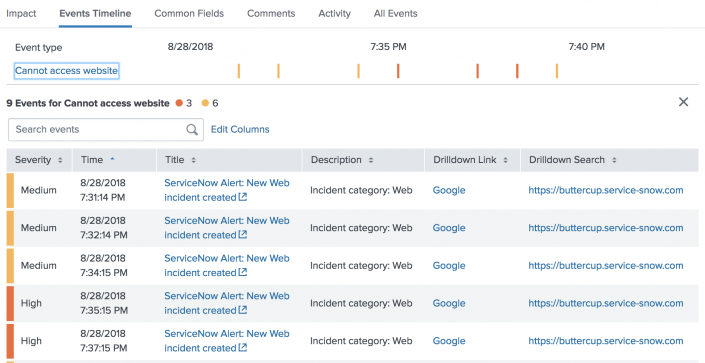
When viewing event details for an episode (a group of events), you can use the Events Timeline to see when individual events occurred. The timeline gives you a detailed look into the notable events contained within each episode and lets you perform a more granular root cause analysis. Colored bars (according to severity) represent individual events.
Use the Sort for and Group by menus to change how events are organized in the timeline, depending on what kind of analysis you want to do.
Sort for
The Sort for menu determines how events are sorted in the timeline.
| Setting | Description |
|---|---|
| Alarm state analysis | Sorts events according to severity, with the most recent, most severe events appearing first. This view focuses on the changing state of the episode and is useful for assessing what is currently broken. |
| Root cause analysis | Sorts events according to when the first event occurred. The exclamation mark identifies the first event in the group to experience a state change (the first event that was no longer "normal" within the context of the group). This view focuses on the cause of the episode and is useful for root cause analysis. |
Group by
The Group by menu determines how events are grouped in the timeline.
| Setting | Description |
|---|---|
| Event type | Groups events according to event type, which is the field generated by the values of the event identifier fields specified in the correlation search. |
| Entity | Groups events according to the entity they are associated with. |
Select an event type or entity name to open a separate table with all the events in that row. Click Edit Columns to add, remove, and reorder columns.
Analyze common fields
View the common fields of all the notable events within an episode and analyze their different values. Common fields can be useful in root cause analysis as you investigate why certain events are grouped as part of the same episode.
Use the slider to filter by the most common fields in the episode. The fields are displayed in alphabetical order.
Investigate similar episodes
Go to the Similar Episodes tab to find out if a problem that's similar or identical to the one you're currently investigating has occurred in the past, and to see how it was resolved.
Select a time range to determine how far back to look for similar episodes. For example, if you remember a similar problem occurring a few months ago, you might set the time range to Last 3 months.
Under Show episodes with similar event fields, select the fields that are most important to you so that ITSI only looks at these fields when comparing to other episodes. The fields you choose are used to analyze and evaluate similarity. For example, if you choose the field host, ITSI displays episodes that came from the same host as the current episode. By default, episodes are compared based on title.
Hover over the Similarity Match for each episode to see the matching event fields. If you see an episode with a high similarity match, open it to investigate what actions were taken to resolve the issue. For example, check the Activity tab to see what actions the analyst took while working on the issue. Look at the Comments tab to see if the analyst left any notes on how they resolved the problem. Open any linked tickets to get even more context about the episode from an external system.
The itsi_event_management_similar_episodes_tickets_lookup macro appends ticketing data when calculating similar episodes, and looks back 30 days by default. Update the default look back period in the macro by updating the search macro.
Selected fields become lost when you navigate away from an episode. However, if you click Actions > Share episode and copy the link, all selected fields are preserved in the linked episode.
| Triage episodes in ITSI | Take action on an episode in ITSI |
This documentation applies to the following versions of Splunk® IT Service Intelligence: 4.11.0, 4.11.1, 4.11.2, 4.11.3, 4.11.4, 4.11.5, 4.11.6, 4.12.0 Cloud only, 4.12.1 Cloud only, 4.12.2 Cloud only, 4.13.0, 4.13.1, 4.13.2, 4.13.3, 4.14.0 Cloud only, 4.14.1 Cloud only, 4.14.2 Cloud only, 4.15.0, 4.15.1, 4.15.2, 4.15.3, 4.16.0 Cloud only, 4.17.0, 4.17.1, 4.18.0, 4.18.1, 4.19.0, 4.19.1, 4.19.2, 4.19.3, 4.19.4

 Download manual
Download manual
Feedback submitted, thanks!