Integrate ITSI with a webhook
Integrate a webhook with IT Service Intelligence (ITSI) so you can send episode data to a webhook URL from ITSI using episode actions, or through automated action rules in notable event aggregation policies.
Set up the integration
Perform the following steps to set up a connection with a webhook.
Prerequisites
| Requirement | Description |
|---|---|
| Webhook URL | You must have a specific webhook URL to send data. |
| ITSI role | You must have the admin role to set up the integration. |
| Authentication details | You must have a username and password to set up basic authentication. You must also have a bearer token to set up bearer authentication. |
Configure a new webhook
- From the ITSI navigation menu, select Configuration' then Data Integrations then select Webhook.
- Select Create webhook.
- Select an authentication type:
- No authentication
- Basic authentication: use a username and password to authenticate the webhook
- Bearer token: specify a specific token (typically a text string) to use to authenticate the webhook
- Add a name for your webhook.
- (Optional) Add a webhook description.
- Add the URL on which episode data will be sent.
- If you selected Basic authentication as your authentication type, input a username and password. If you selected Bearer token as your authentication type, input a bearer token.
- (Optional) Add headers for the URL.
- (Optional) Select Verify certificate if the webhook's SSL certificate is verified.
- Select Save.
Sample webhook payload
The data will be sent as a JSON string to the webhook URL.
"{\"index\": \"itsi_grouped_alerts\", \"itsi_bdt_event\": \"\", \"itsi_dummy_closing_flag\": \"\", \"itsi_group_id\": \"bb9be1b4-f15d-4d0f-bb00-15efb36ed40c\", \"source\": \"test_cs\", \"sourcetype\": \"itsi_notable:group\", \"_time\": \"1713866345.477\", \"_raw\": \"{\\\"referer\\\":\\\"-\\\",\\\"drilldown_search_earliest_offset\\\":\\\"-300\\\",\\\"event_identifier_fields\\\":\\\"source\\\",\\\"orig_raw\\\":\\\"10.56.129.122 - admin [23/Apr/2024:09:58:59.910 +0000] \\\\\\\"GET /en-US/splunkd/__raw/servicesNS/admin/itsi/search/v2/jobs/1713866339.937?output_mode=json&_=1713866315556 HTTP/1.1\\\\\\\" 200 2840 \\\\\\\"-\\\\\\\" \\\\\\\"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36\\\\\\\" - 10c80b2b67d6aa23084e6e934e11bb5c 2ms\\\",\\\"ident\\\":\\\"-\\\",\\\"itsi_group_count\\\":\\\"4\\\",\\\"rid\\\":\\\"0\\\",\\\"uri_path\\\":\\\"/en-US/splunkd/__raw/servicesNS/admin/itsi/search/v2/jobs/1713866339.937\\\",\\\"itsi_instruction\\\":\\\"%itsi_instruction%\\\",\\\"itsi_is_first_event\\\":\\\"false\\\",\\\"clientip\\\":\\\"10.56.129.122\\\",\\\"search_name\\\":\\\"test_cs\\\",\\\"itsi_group_description\\\":\\\"Applies to events that do not meet the criteria of any other active policy.\\\",\\\"orig_time\\\":\\\"1713866345.4765794\\\",\\\"orig_rid\\\":\\\"0\\\",\\\"mod_time\\\":\\\"1713866345.4765794\\\",\\\"method\\\":\\\"GET\\\",\\\"itsi_group_severity\\\":\\\"1\\\",\\\"search_type\\\":\\\"basic\\\",\\\"version\\\":\\\"HTTP/1.1\\\",\\\"req_time\\\":\\\"23/Apr/2024:09:58:59.910 +0000\\\",\\\"itsi_service_ids\\\":\\\"null\\\",\\\"drilldown_search_latest_offset\\\":\\\"300\\\",\\\"orig_index\\\":\\\"_internal\\\",\\\"itsi_group_id\\\":\\\"bb9be1b4-f15d-4d0f-bb00-15efb36ed40c\\\",\\\"uri_query\\\":\\\"output_mode=json&_=1713866315556\\\",\\\"itsi_group_instruction\\\":\\\"null\\\",\\\"itsi_is_last_event\\\":\\\"false\\\",\\\"itsi_split_by_hash\\\":\\\"source:test_cs:\\\",\\\"status\\\":\\\"1\\\",\\\"itsi_first_event_time\\\":\\\"1713866164.889\\\",\\\"other\\\":\\\"- 10c80b2b67d6aa23084e6e934e11bb5c 2ms\\\",\\\"is_use_event_time\\\":\\\"0\\\",\\\"useragent\\\":\\\"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36\\\",\\\"title\\\":\\\"title_1\\\",\\\"itsi_earliest_event_time\\\":\\\"1713866164.89\\\",\\\"file\\\":\\\"1713866339.937\\\",\\\"itsi_parent_group_id\\\":\\\"c8891186-3819-489b-b371-d4a215b900ef\\\",\\\"event_field_max_length\\\":\\\"10000\\\",\\\"root\\\":\\\"en-US\\\",\\\"orig_sourcetype\\\":\\\"splunkd_ui_access\\\",\\\"itsi_group_title\\\":\\\"title_1\\\",\\\"severity\\\":\\\"1\\\",\\\"owner\\\":\\\"unassigned\\\",\\\"itsi_action_rule_keys\\\":\\\"null\\\",\\\"spent\\\":\\\"2\\\",\\\"itsi_group_assignee\\\":\\\"unassigned\\\",\\\"uri\\\":\\\"/en-US/splunkd/__raw/servicesNS/admin/itsi/search/v2/jobs/1713866339.937?output_mode=json&_=1713866315556\\\",\\\"itsi_group_status\\\":\\\"1\\\",\\\"itsi_first_event_id\\\":\\\"b30343d0-0157-11ef-bad6-064456e894d9\\\",\\\"event_id\\\":\\\"1ea6b0cc-0158-11ef-9ad6-064456e894d9\\\",\\\"itsi_policy_id\\\":\\\"itsi_default_policy\\\",\\\"bytes\\\":\\\"2840\\\",\\\"orig_status\\\":\\\"200\\\",\\\"itsi_last_event_time\\\":\\\"1713866345.477\\\",\\\"output_mode\\\":\\\"json\\\",\\\"event_identifier_hash\\\":\\\"9dffbe7047f146d830fec82a5ebf013f19686c72432c70819d82995d2a2a47da\\\",\\\"event_identifier_string\\\":\\\"/opt/splunk/var/log/splunk/splunkd_ui_access.log\\\",\\\"user\\\":\\\"admin\\\",\\\"orig_sid\\\":\\\"scheduler__admin__itsi__RMD5d2ff4c2e3a811a1d_at_1713866340_259\\\"}\", \"host\": \"so1\", \"_sourcetype\": \"itsi_notable:group\", \"_cd\": \"0:290\", \"_bkt\": \"itsi_grouped_alerts~0~C3737AC5-933C-42A4-95A7-4A337234B648\", \"linecount\": \"1\", \"splunk_server\": \"so1\", \"splunk_server_group\": \"\", \"_si\": [\"so1\", \"itsi_grouped_alerts\"], \"_indextime\": \"1713866406\", \"_subsecond\": \".477\", \"drilldown_search_earliest_offset\": \"-300\", \"event_identifier_fields\": \"source\", \"orig_raw\": \"10.56.129.122 - admin [23/Apr/2024:09:58:59.910 +0000] \\\"GET /en-US/splunkd/__raw/servicesNS/admin/itsi/search/v2/jobs/1713866339.937?output_mode=json&_=1713866315556 HTTP/1.1\\\" 200 2840 \\\"-\\\" \\\"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36\\\" - 10c80b2b67d6aa23084e6e934e11bb5c 2ms\", \"itsi_group_count\": \"4\", \"orig_owner\": \"\", \"rid\": \"0\", \"tid\": \"\", \"itsi_instruction\": \"%itsi_instruction%\", \"itsi_is_first_event\": \"false\", \"search_name\": \"test_cs\", \"itsi_group_description\": \"Applies to events that do not meet the criteria of any other active policy.\", \"orig_time\": \"1713866345.4765794\", \"orig_rid\": \"0\", \"mod_time\": \"1713866345.4765794\", \"method\": \"GET\", \"log_level\": \"\", \"itsi_group_severity\": \"1\", \"search_type\": \"basic\", \"itsi_service_ids\": \"null\", \"drilldown_search_latest_offset\": \"300\", \"start_time\": \"1713866164.889\", \"orig_index\": \"_internal\", \"itsi_group_instruction\": \"null\", \"itsi_is_last_event\": \"false\", \"itsi_split_by_hash\": \"source:test_cs:\", \"metric_info_numberOfObjects\": \"\", \"status\": \"1\", \"itsi_first_event_time\": \"1713866164.889\", \"is_use_event_time\": \"0\", \"title\": \"title_1\", \"itsi_earliest_event_time\": \"1713866164.89\", \"itsi_parent_group_id\": \"c8891186-3819-489b-b371-d4a215b900ef\", \"event_field_max_length\": \"10000\", \"sub_component\": \"\", \"orig_sourcetype\": \"splunkd_ui_access\", \"transaction_time\": \"\", \"itsi_group_title\": \"title_1\", \"severity\": \"1\", \"owner\": \"unassigned\", \"itsi_action_rule_keys\": \"null\", \"end_time\": \"\", \"itsi_group_assignee\": \"unassigned\", \"itsi_group_status\": \"1\", \"component\": \"\", \"itsi_first_event_id\": \"b30343d0-0157-11ef-bad6-064456e894d9\", \"event_id\": \"1ea6b0cc-0158-11ef-9ad6-064456e894d9\", \"itsi_policy_id\": \"itsi_default_policy\", \"itsi_last_event_time\": \"1713866345.477\", \"event_identifier_hash\": \"9dffbe7047f146d830fec82a5ebf013f19686c72432c70819d82995d2a2a47da\", \"event_identifier_string\": \"/opt/splunk/var/log/splunk/splunkd_ui_access.log\", \"orig_sid\": \"scheduler__admin__itsi__RMD5d2ff4c2e3a811a1d_at_1713866340_259\", \"referer\": \"-\", \"ident\": \"-\", \"uri_path\": \"/en-US/splunkd/__raw/servicesNS/admin/itsi/search/v2/jobs/1713866339.937\", \"clientip\": \"10.56.129.122\", \"punct\": \"{\\\"\\\":\\\"-\\\",\\\"\\\":\\\"-\\\",\\\"\\\":\\\"\\\",\\\"\\\":\\\"..._-__[//:::._+]_\\\\\\\"_/-//\", \"version\": \"HTTP/1.1\", \"req_time\": \"23/Apr/2024:09:58:59.910 +0000\", \"uri_query\": \"output_mode=json&_=1713866315556\", \"other\": \"- 10c80b2b67d6aa23084e6e934e11bb5c 2ms\", \"useragent\": \"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36\", \"file\": \"1713866339.937\", \"root\": \"en-US\", \"spent\": \"2\", \"uri\": \"/en-US/splunkd/__raw/servicesNS/admin/itsi/search/v2/jobs/1713866339.937?output_mode=json&_=1713866315556\", \"bytes\": \"2840\", \"orig_status\": \"200\", \"output_mode\": \"json\", \"user\": \"admin\", \"limit\": \"\", \"query\": \"\", \"skip\": \"\", \"eventtype\": \"\", \"_eventtype_color\": \"\", \"tag\": \"\", \"tag::eventtype\": \"\", \"_serial\": \"0\", \"instruction\": \"null\", \"description\": \"\", \"last_time\": \"1713866345.477\", \"is_active\": \"1\", \"event_count\": \"4\", \"policy_id\": \"itsi_default_policy\", \"_itsi_is_group_broken\": \"0\"}"
Test the webhook integration
To run your new webhook, follow these instructions.
- Go to the Alerts and Episodes page.
- Select an episode.
- Select the Actions dropdown menu, then select Webhook.
Automatically send episode data to a webhook
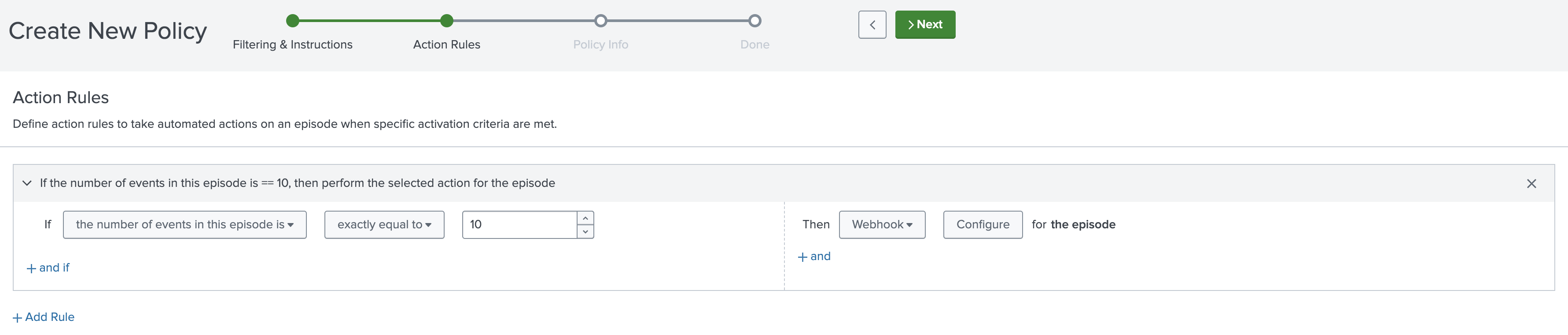
To configure aggregation policy action rules to send episode data to a webhook, follow these steps.
- Select Configuration then Event Management then Notable Event Aggregation Policies.
- Open the aggregation policy you want to integrate with the webhook, or select Create Notable Event Aggregation Policy.
- Select the Action Rules tab.
- Select Add Rule and configure the webhook to forward the episode data.
- Select Configure and provide a name for the webhook, and validate the webhook URL.
| Integrate ITSI with PagerDuty | Integrate ITSI with Splunk On-Call |
This documentation applies to the following versions of Splunk® IT Service Intelligence: 4.19.0, 4.19.1, 4.19.2, 4.19.3, 4.19.4, 4.20.0, 4.20.1
 Download manual
Download manual
Feedback submitted, thanks!