Scenario: Alex automates a security workflow in Splunk Mission Control
The following scenario features Buttercup Games, a fictitious game company.
Buttercup Games recently released the latest version of its sought-after artificial intelligence gaming software to complement one of its popular online games. Alex, a security operations center (SOC) analyst at Buttercup Games, uses Splunk Mission Control to automate their security workflow. In the first two scenarios, Alex found a suspicious IP address during their incident investigation and added relevant events to the incident during their response. See Scenario: Alex triages and investigates an incident in Splunk Mission Control and Scenario: Alex responds to a security incident in Splunk Mission Control. In this scenario, Alex decides that they want to update their manager, Wei, who is a SOC administrator, and automate the workflow to improve incident response time when other similar security incidents occur.
Automate a security workflow
To automate a security workflow using an action and playbook in Splunk Mission Control, Alex follows these steps:
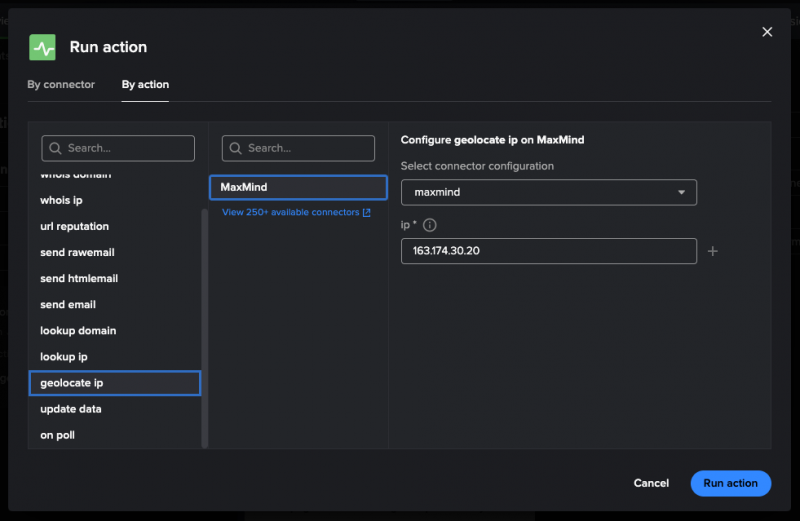
- Alex uses the IP address from the Overview tab of the incident to run an action. In the Automation tab of the incident, Alex selects Run action. They select geolocate_ip for the action and Maxmind for the connector. Then, Alex configures the action and selects Run action.
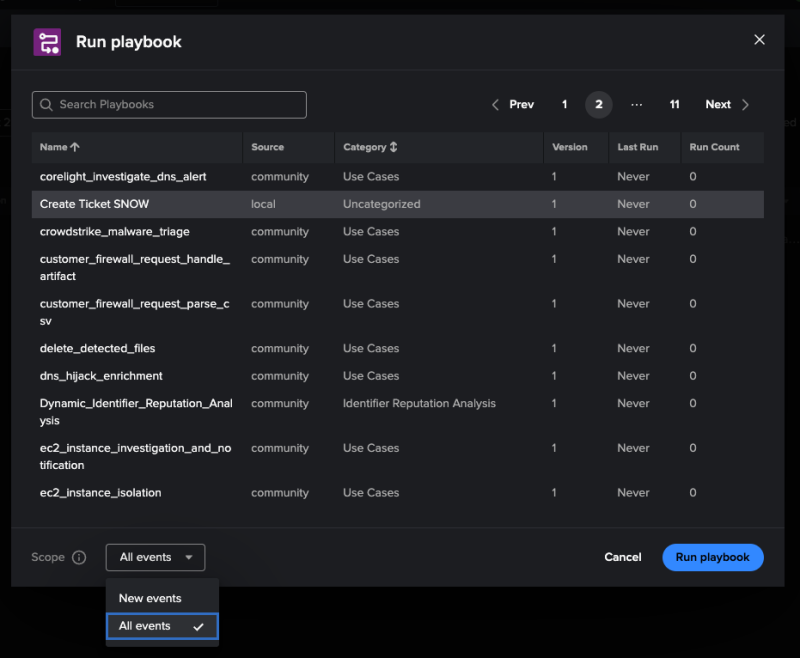
- Alex runs a playbook to automatically file a SNOW ticket that contacts their manager. In the Automation tab of the incident, Alex selects Run playbook. They select Create Ticket SNOW, set the scope to All events, and then select Run playbook.
- Running the playbook assigns a prompt to Wei, a SOC administrator, to escalate blocking the suspicious IP address. In the meantime, Alex returns to the Response tab to continue working through response template tasks.
Summary
In this scenario, Alex automated their security workflow using an action and playbook in Splunk Mission Control. They ran an action using a connector and then ran a playbook that filed a ticket and sent a prompt. The automation that Alex set up allows them to spend less time responding to similar incidents in the future.
In the Splunk Mission Control scenario library, Alex uses Splunk Mission Control to investigate and respond to an improbable login. Alex triages and investigates the incident, applies a response plan to the incident, and uses an action and playbook to automate incident response for future similar security incidents.
Learn more
To learn more about automating your security workflows with Splunk Mission Control, see Automate incident response with playbooks and actions in Splunk Mission Control.
| Scenario: Alex responds to a security incident in Splunk Mission Control | Scenario: Wei creates an intelligence workflow in Splunk Mission Control to reduce false positives |
This documentation applies to the following versions of Splunk® Mission Control: Current
 Download manual
Download manual
Feedback submitted, thanks!