Map to CIM
In Map to CIM, map the fields from your data to the fields in one of the predefined common information models (CIM) to normalize data at search time.
The Splunk Common Information Model add-on is required to use this feature.
- Download the Splunk Common Information Model add-on from Splunkbase.
- For details about installation, see Install the Splunk Common Information Model Add-on.
Add an event type
Before you can map fields, you need to create an event type to generate events from which to extract fields.
For each source type for which you want to map fields, add an event type:
- On your add-on homepage, click Map to CIM on the Add-on Builder navigation bar.
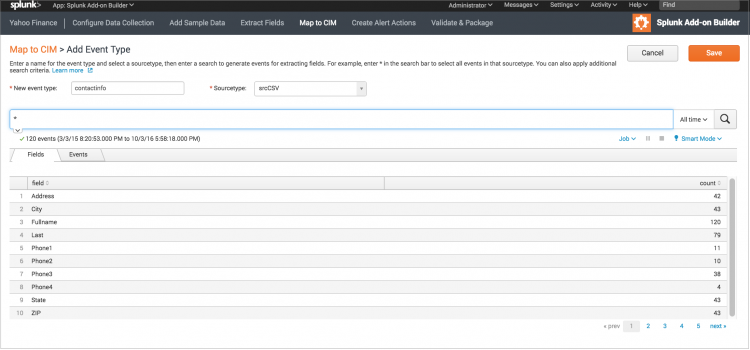
- On the Map to CIM page, click Add Event Type.
- Enter a name for the event type, and select a source type from which to generate events.
- In the search bar, enter a search to select events:
- Click Save.
* Enter "*" to select all events for the source type. * Apply additional search criteria as needed.
The Add-on Builder returns to the Map to CIM page, and you can now map events from this event type to the CIM.
Map events to the CIM
Map events from an event type to the CIM:
- On your add-on homepage, click Map to CIM on the Add-on Builder navigation bar.
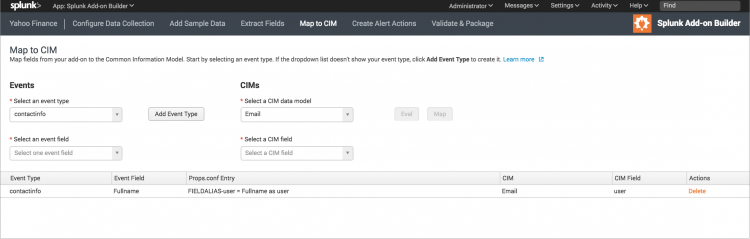
- On the Map to CIM page, select an event type. Fields from this event type appear in the list of event fields.
- Select an event field.
- Select a CIM from the list of pre-defined CIM data models.
- Select a CIM field that you want to map to the event field.
- Optionally, click Eval to apply an eval statement to the mapping. Enter the eval string and click Submit.
- Click Map. The CIM mapping appears in the list.
Repeat this procedure for all of the fields you want to map.
Learn more
For more information, see the following Splunk Enterprise documentation:
- About event types in the Knowledge Manager Manual
- Use the CIM to normalize data at search time in the Common Information Model Add-on Manual
| Extract fields | Create alert actions |
This documentation applies to the following versions of Splunk® Add-on Builder: 2.0.0
 Download manual
Download manual
Feedback submitted, thanks!