Identity dashboards
The Identity domain correlates host information to assets and provides additional information about the source and targets of events. The concepts of Identity correlation and Asset management are treated similarly in the Splunk App for Enterprise Security. For a thorough background in the use of Asset records and Identity records, see the section on Asset management.
For Asset Center, clicking on "ip", "nt_host", "mac", or "dns" will take you to the Asset Investigator dashboard. Clicking on "owner" will take you to the Identity Investigator dashboard. Clicking on anything else takes you to the Search dashboard.
For Identity Center, clicking on an "identity" value will take you to the Identity Investigator dashboard. Clicking on anything else (for example, priority=critical) will take you to the Search page.
If asset_investigator and/or identity_investigator are not present on the system, the drill down takes you to the Search dashboard.
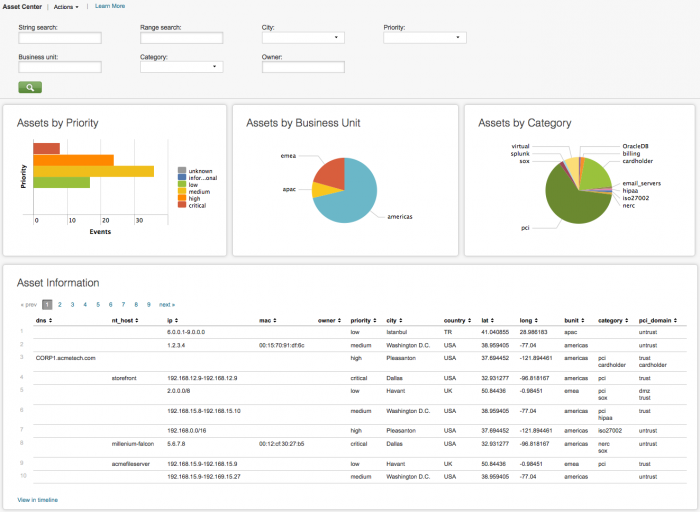
Asset Center dashboard
The Asset Center provides a way to review and search the asset list. To use this dashboard, an asset list must be created - a list of hosts, IP addresses, and subnets within the organization, along with information about each asset. The asset list provides information about the source and destination of events and is used to determine asset properties such as asset location and the urgency of notable events.
Clicking on chart elements or table rows on this page displays the raw events that are generating the items represented. See dashboard drilldown for more information.
The following table describes the panels for this dashboard.
| Panel | Description |
|---|---|
| Dashboard filters | Restricts the view on the current dashboard to assets that match the selected criteria. Selections apply to the current dashboard only. See descriptions of the standard filter options. The following domain-specific options are available:
|
| Assets by Priority | Shows the relative number of assets by priority and helps identify how the asset priorities are distributed. Generally, it is a good idea to designate fewer hosts as critical priority with progressively more hosts within the lower priorities. |
| Assets by Business Unit | Shows the relative number of assets by business unit and helps identify how the assets are distributed. |
| Assets by Category | Shows the relative number of assets by category and helps identify how the assets are distributed. |
| Asset Information | Shows all assets that match the current dashboard filter. |
Note: Text values in search fields must be lowercase text.
Using string and range IP address searches
The Asset Center provides two types of IP address searches, to support differentiation between individual machine records and descriptive range records. String searches are useful for hostname and wildcard searches, such as listing systems that are in private RFC1918 network ranges. Range searches are useful for finding a specific and complete IP address, even if that address is not explicitly listed.
For example, these three records from the sample data can be used (trimmed for length):
nt_host,ip,priority - asset table lookup headers for sample data
,192.168.15.8-192.168.15.10,medium acmefileserver,192.168.15.9-192.168.15.9,low ,192.168.15.9-192.169.15.27,high
- A string search for "192.168.15.*" will return all three records, because the string "192.168.15." can be found in all three ip fields.
- A range search for "192.168.15.*" will return nothing, because the wildcard has no numeric value.
- A string search for "192.168.15.9" will return nothing, because there is no individual record with that address (even though the address is matched by two ranges).
- A range search for "192.168.15.9" will return "acmefileserver,192.168.15.9-192.168.15.9,low" because it is the most specific matching record
- A string search for "192.168.15.10" will return nothing, because there is no individual record with that address (even though the address is matched by two ranges).
- A range search for "192.168.15.10" will return ",192.168.15.8-192.168.15.10,medium" because it is the most specific matching record
- A string search for "acmefileserver" will return "acmefileserver,192.168.15.9-192.168.15.9,low" because the nt_host field matches exactly.
Range searches can be used for textual strings as well, but this is not recommended. For instance, a range search for "acmefileserver" will return "acmefileserver,low" because it is the most specific matching record to that hostname. The IP address 192.168.15.9 is omitted from the returned result though, which can be confusing.
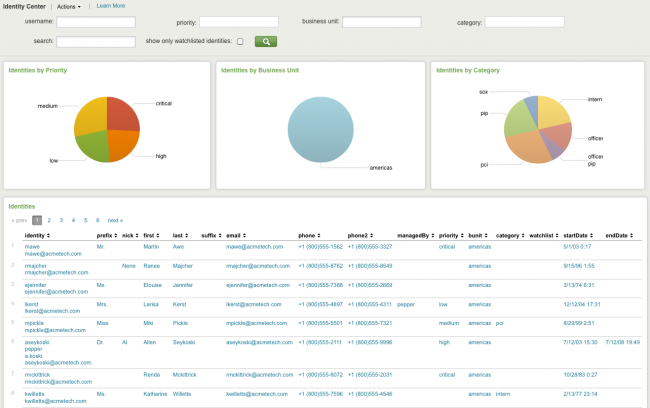
Identity Center dashboard
The Identity Center dashboard provides information about all of the identities associated with this instance of the Splunk App for Enterprise Security.
The Identity Center provides a way to review and search the identity list. To use this dashboard, an identity list (or table) must be created - a list of account names, legal names, nicknames, alternate names, and phone numbers within the organization. The identity list provides contact information for individuals involved in events and is used to determine asset properties such as owner and user.
Click on the magnifying glass (![]() ) to see the identities currently associated with the instance.
) to see the identities currently associated with the instance.
| Panel | Description |
|---|---|
| User name | |
| Priority | Select priority (unknown, low, medium, high, critical) from drop-down list |
| Business unit | Enter text by key=name pairs (for example, bunit=americas) |
| Category | Select from drop-down list |
| Search | Search by key=name pairs (for example, priority=critical) |
Note: Text values in the filter fields must be lowercase text. To see only identities tagged as "watchlist" in the Identities list, click "Watchlisted identities only".
For more detail,click on an identity in the Identities list in this dashboard.
And the name is populated in the Assets and Identities Search dashboard.
Using the filters (and search) it is possible to drill down for more information.
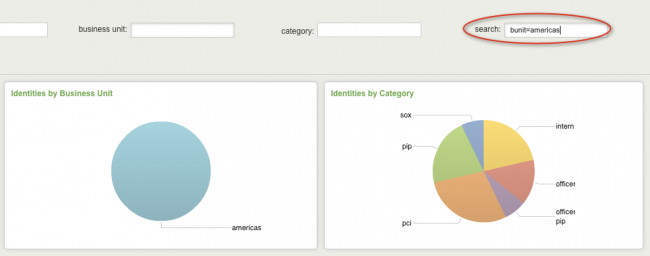
The filter for the Identity Center dashboard uses a search that is operating on an identity table, not events. The search needs key=value pairs to be specified in this filter to work correctly, not text.
Example key=value pairs:
email=*acmetech.com nick=anickname bunit=americas
Here is an example of how these key=value pairs would be used with search:
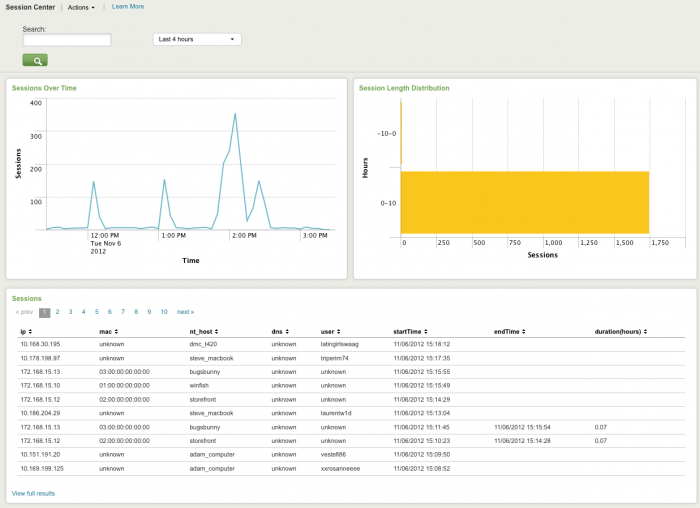
Session Center dashboard
The Session Center dashboard provides an overview of network sessions. Network sessions are used to correlate network activity to a user using session data provided by DHCP or VPN servers, for example. Use the Session Center to review the session logs and identify the user or machine associated with an IP address used during a session.
The Session Center can also help identify anomalous activity such as excessively long sessions. The drill-down option is not available from this dashboard. Configure new data inputs through the Splunk Settings menu or search for particular traffic events directly through Incident Review.
The following table describes the panels for this dashboard.
| Panel | Description |
|---|---|
| Dashboard filters | Restricts the view on the current dashboard to sessions that contain the search string. |
| Longest Sessions | Lists excessively long network sessions. Long sessions may indicate insecure network usage. For example, some employees may establish and maintain a VPN session from their home network to the company network continuously. A continuous network session increases the chance that a security problem on the employee's network could impact the company by allowing an attacker to use the VPN connection to compromise additional systems. |
| Most Recent Sessions | Lists the network sessions that have been most recently opened, based on the session start time. This panel shows details associated with each recently opened session, such as the user, MAC address, IP address, NT host name and DNS name. |
Note: Text values in search fields must be lowercase text.
| More Network dashboards | Audit dashboards |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.0, 3.0.1

 Download manual
Download manual
Feedback submitted, thanks!