Add annotations to enrich risk incident rule search results
This is the third step in the Isolate threats with risk-based alerting scenario.
Ram adds annotations to enrich the results of the risk incident rules in Splunk Enterprise Security. Using annotations, Ram sends the search results to a risk index that uses specific security lenses for review. Annotations provide context to the risk objects based on industry standard cyber security mappings.
Usually, annotations depend on four default cybersecurity frameworks, including CIS20, Kill 10, MITRE ATT&CK, and NIST, with additional support for custom frameworks. Annotations depend on risk scores. Ram can generate an alert when a user or a system achieves a risk score greater than 100 in a 24-hour span. Annotations can also depend on outliers in the business unit or active directory roles and can generate notables when a user's risk score is one or two standard deviations over the norm for that specific business unit or role.
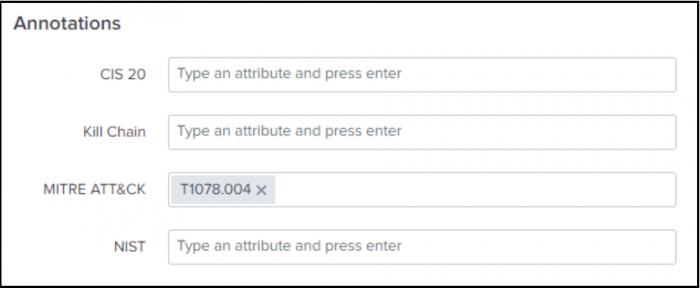
- Ram decides to add MITRE ATT&CK annotations to the correlation search by navigating to the Annotations panel in the Edit Correlation Search window.
- Ram enters T1078.004 in the MITRE ATT&CK field to align the security detection to the MITRE ATT&CK sub-technique.
- Ram can also add custom annotations to the security detections in the SPL of the correlation search.
- Ram uses the correlation search "Risk Notable: Risk Threshold Exceeded For Risk Object Over 24 Hour Period", which is customized to identify the alerts created when a user exceeds an aggregated score of 100 in a 24-hour period.
Ram now has the context provided by the annotations to investigate all the factors that contributed to generating the alert.
Next step
Classify risk objects based on annotations
See also
For more information on annotations, see the product documentation:
| Generate risk notables using risk incident rules | Classify risk objects based on annotations |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.3.2, 7.3.3
 Download manual
Download manual
Feedback submitted, thanks!