Classify risk objects based on annotations
This is the fourth step in the Isolate threats with risk-based alerting scenario.
Ram views the annotations associated with the risk objects in the embedded risk workbench panels in Splunk Enterprise Security and classifies the risk objects for more targeted threat investigation. Risk workbench panels provide at-a-glance risk-based insight into the severity of the events occurring in Ram's system or network. They help Ram to to prioritize notable events, assign notable events to security analysts for review, and examine specific notable annotations for investigations.
By visually classifying the risk objects based on risk modifiers, risk scores, MITRE ATT&CK techniques, and tactics, Ram can identify specific adaptive response actions and streamline the threat investigation process as follows:
- From the Splunk Enterprise Security menu, Ram selects Incident Review to display the Incident Review page and see a list of notable events for the security domains.
- Ram expands a notable event by selecting Action next to the Risk Object, Destination, User, or Source fields.
- Ram selects the Workbench-Risk (risk_object) as an asset action.
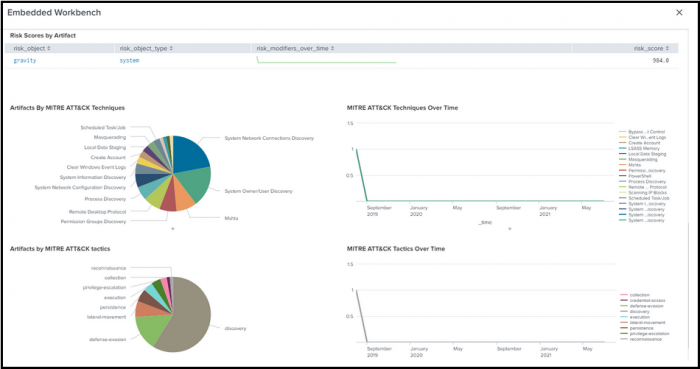
Using the visuals and charts Ram now investigates the risk objects for a single artifact in the Embedded Workbench.
The Embedded Workbench panel displays the following items:
- Recent risk modifiers that apply to the risk object.
- Risk scores by artifact and trends of risk modifiers over time.
- Pie chart displaying the distribution of artifacts by MITRE ATT&CK techniques like Driven by Compromise, Account Manipulation, and so on.
- Pie chart displaying the distribution of artifacts by MITRE ATT&CK tactics like discovery, persistence, defense evasion, and so on.
- Time chart displaying MITRE ATT&CK Techniques Over Time'.
- Time chart displaying the MITRE ATT&CK Tactics Over Time.
Next step
Add a risk message and a risk score to a notable
See also
For more information on risk annotations, see the product documentation:
How risk annotations provide additional context in Splunk Enterprise Security
| Add annotations to enrich risk incident rule search results | Add a risk message and a risk score to a notable |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.3.2, 7.3.3
 Download manual
Download manual
Feedback submitted, thanks!