Add a risk message and a risk score to a notable
This is the fifth step in the Isolate threats with risk-based alerting scenario.
Ram adds a risk message and a risk score to the notable event that represents a threat by creating an adaptive response action. These adaptive response actions help to gather more information, take an action in another system, send information to another system, modify a risk score, and so on. Adding a custom risk message helps Ram to build detections based on specific information, such as risk scores, instead of merely relying on the Risk Analysis data model schema.
- From a risk notable event, Ram selects the arrow to expand the Actions column and selects Run Adaptive Response Actions.
- Ram selects Add New Response Action and selects the Risk Analysis adaptive response action from the dropdown list to create risk modifier events in the risk index.
- Ram enters the following risk message,
Possible Bypass of User Account Controls.
The following screenshot displays how to configure a risk message as an adaptive response action in the Correlation Search Editor.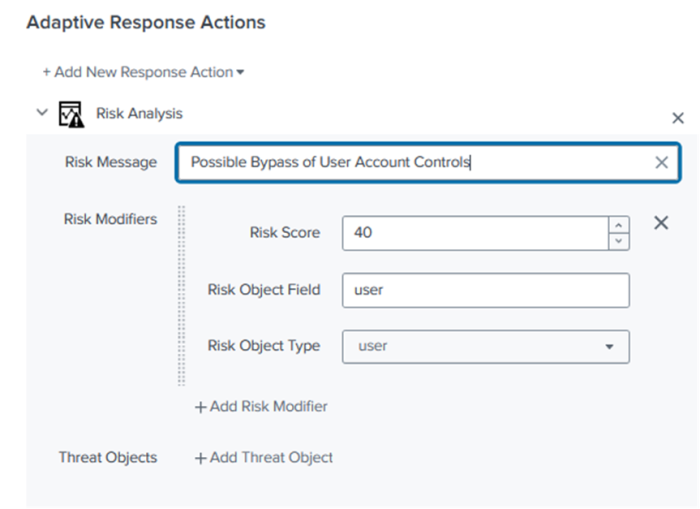
- Ram also adds a risk modifier by populating the following fields:
- Risk Score
- Risk Object Field
- Risk Object Type
- Ram selects Run to run the adaptive risk action on the notable.
Next step
Adjust risk scores for specific objects
See also
For more information on risk messages, see the product documentation:
| Classify risk objects based on annotations | Adjust risk scores for specific objects |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.3.2, 7.3.3
 Download manual
Download manual
Feedback submitted, thanks!