Configure the urgency for findings in Splunk Enterprise Security
You can prioritize findings in the investigation workflow by using urgency levels. Every finding is assigned an urgency level. Splunk Enterprise Security calculates the urgency level using the severity of the events created by the detection and the priority of the asset or identity involved in the event. You can also change the urgency of a finding.
You can find the urgency levels for findings on the analyst queue of the Mission Control page in Splunk Enterprise Security. Urgency levels can be Unknown, Low, Medium, Informational, High, or Critical. Any value that is not one of these filtered urgencies defaults to "unknown". This ensures that you can see all findings in the analyst queue.
How urgency is assigned to findings
Splunk Enterprise Security uses the urgency_lookup to determine the urgency level of findings that are generated by detections. Splunk Enterprise Security calculates urgency by using both the severity and priority values assigned to the finding based on the priority assigned to specific fields in the assets and identities.
The following fields are used to determine priority when the priority is assigned through an asset and identity lookup:
- For identities:
userorsrc_user - For assets:
dest,src, ordvc
Splunk Enterprise Security sets the severity value directly on the finding generated by the detection. If both the asset and identity in the finding have an assigned priority, the higher priority is used to calculate the urgency. You can use the Urgency field to prioritize the investigation of findings.
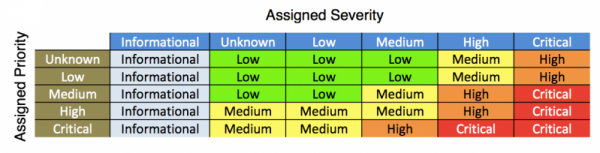
The following table provides an example of how Splunk Enterprise Security calculates the default urgency values for findings. You can overwrite the default results by modifying priority and rank, search syntax, or urgency lookups.
- If event severity is informational, the event urgency is informational, regardless of asset priority.
- If asset priority is unknown or low and event severity is unknown, low, or medium, the event urgency is low.
- If asset priority is unknown or low and event severity is high, the event urgency is medium.
- If asset priority is unknown or low and event severity is critical, the event urgency is high.
- If asset priority is unknown or low and event severity is critical, the event urgency is high.
- If asset priority is medium and event severity is unknown or low, the event urgency is low.
- If asset priority is medium and event severity is medium, the event urgency is medium.
- If asset priority is medium and event severity is high, the event urgency is high.
- If asset priority is medium and event severity is critical, the event urgency is critical.
- If asset priority is high and event severity is unknown, low, or medium, the event urgency is medium.
- If asset priority is medium and event severity is high, the event urgency is high.
- If asset priority is medium and event severity is critical, the event urgency is critical.
- If asset priority is critical and event severity is unknown or low, the event urgency is medium.
- If asset priority is critical and event severity is medium, the event urgency is high.
- If asset priority is critical and event severity is high or critical, the event urgency is critical.
Splunk Enterprise Security can assign a finding an "unknown" urgency level if the priority value from the asset and identity lookups or the severity value assigned by the detection or in a triggering event is not recognized.
Modify the urgency of a finding
You can also modify the urgency level after the finding is created. Use one of the following methods to modify the urgency assigned to findings:
- Modify priority and rank in the asset and identity framework
- Modify the severity of the finding in the detection SPL syntax
- Modify the urgency lookup directly
Modify priority and rank in the asset and identity framework
The asset and identity framework helps to calculate the urgency when asset and identity correlation is activated and you have made your lookups automatic, When a detection runs, the results are enriched with the data from these automatic lookups. The priority field in an automatic lookup table affects the urgency of a finding.
You can rank the order of your asset and identity lists to determine priority for merging assets and identities. For example, if you have identity lists called source A and source B:
| Source A | Source B |
|---|---|
|
|
These merge on the matching key identity fields, and the priority is set to low. Source A is the higher rank, and therefore takes higher precedence when merging single valued fields. If two or more sources have the same rank, then the last nonempty value is the priority.
The data is merged into three different collections: asset_lookup_by_str, asset_lookup_by_cidr, and identities_lookup_expanded. Lookups on these collections are based on a primary key. Therefore, an event is typically not enriched by both an asset and an identity collection. However, if it does happen, then you can see a field such as priority depending on its alias as defined in props.conf. If there is an event that is enriched by both asset and identity lookups, then the event has the fields dest_priority, dvc_priority, and src_priority, which comes from asset enrichment and src_user_priority and user_priority, which comes from identity enrichment.
Modify the severity of the finding in the detection SPL syntax
Modify the urgency of a finding by defining severity in the detection SPL syntax. You must have access to edit detections to make these changes.
For example, you can change the severity of a detection according to the number of failures in the search results. To set a "critical" severity when there are more than 100 failures, a high severity when there are more than 50 failures, and a medium severity for the rest of the results, add search syntax like the following example to the end of the detection SPL:
... | eval severity=case(failure>100,"critical",failure>50,"high",failure<=50,"medium")
Severity defined in the search syntax results in an event where severity takes precedence over the severity defined in the finding adaptive response action.
Modify the urgency lookup directly
You can change which severity and priority values result in which calculated urgency values for findings in Splunk Enterprise Security.
Only specific values are valid for severity or priority values. Use only those values when modifying the lookup. Do not modify the names of the urgency values of findings.
- Valid severity values: unknown, informational, low, medium, high, critical.
- Valid priority values: unknown, low, medium, high, critical.
- Valid urgency values: informational, low, medium, high, critical.
Follow these steps to modify the urgency lookup:
- On the Splunk Enterprise Security menu bar, select Security content and then select Content management.
- Choose the Urgency Levels lookup. Then, you can see an editable, color coded table representing the urgency lookup file.
- In any row where the priority or severity is listed as unknown, review the assigned urgency.
- (Optional) Edit the table and change the urgency to another one of the accepted values. All urgency values must be lower case.
- Select Save.
See also
For more information on how to manage urgency levels for findings and investigations in Splunk Enterprise Security, see the product documentation:
- Configure users and roles in the Splunk Enterprise Security Installation and Upgrade Manual.
- Override and replace the calculated urgency of a finding or an investigation
- Manage analyst workflows using the analyst queue in Splunk Enterprise Security
| Configure findings manually to track specific fields in Splunk Enterprise Security | Change the status of a finding or an investigation in Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.31, 8.0.40
 Download manual
Download manual
Feedback submitted, thanks!