Create finding groups in Splunk Enterprise Security
You can create groups of findings and intermediate findings using findings-based detections based on certain conditions. Then, you can include the finding groups into an investigation manually and triage them. Finding groups are stored in KVStore collections.
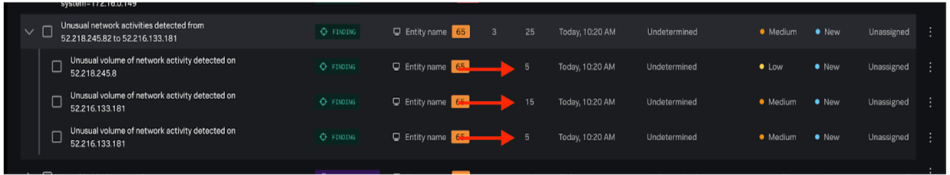
When you add additional findings to a finding group, the finding group moves to the top of the analyst queue on the Mission Control page.
The following screenshot displays a nested finding group in the analyst queue on the Mission Control page:
Configure conditions to create finding groups in Splunk Enterprise Security
Follow these steps to create finding groups in Splunk Enterprise Security:
- In the Splunk Enterprise Security app, go to Security content.
- Select Content management.
- Select +Content and then select Detection to open the editor.
- In the Create findings-based detection editor, go to Finding input type.
- Select a group type to combine the findings from the detection search results into high confidence finding groups.
The following options are available to specify the criteria and group the findings from the detection search results:
Group type Description Example Entity Group findings by asset, identity, user, or device that can be used by Splunk Enterprise Security to identify potential security threats. Creates a finding group when findings for a common entity exceeds a count threshold. If the number of findings created by a user Tom is greater than 10, those findings get nested together in the analyst queue. Threat object Group findings by observables such as a URL, file hash, email address, domain, command line, IP addresses, registry keys, filenames, or file directory that poses an increased security risk. Creates a finding group when findings contain the same threat object for an entity and exceed a threshold. If the number of findings created for an email address such as "sam@splunk.com" drops by 10, those findings get nested together in the analyst queue. Cumulative entity risk Group findings by the total risk that an entity such as an asset, identity, user, or system might represent during a given period of time. Creates a finding group when findings reach a risk score threshold for an entity. If the findings created for a system such as "localhost1234" have a risk score which rises by 100, those findings get nested together in the analyst queue. Kill Chain Group findings based on the Cyber Kill Chain framework such as Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command, Control, Action on Objectives, which identifies the phases of a cyber-attack and helps to anticipate the sequential actions of an attacker. Creates a finding group when the findings exceed a threshold number for the phases in the Kill Chain. If the number of Kill Chain phases for some findings is less than 10, those findings get nested together in the analyst queue. MITRE ATT&CK Group findings by the MITRE ATT&CK framework, which is a knowledge base of adversary tactics and techniques used to develop threat models and methodologies. Create a finding group when findings exceed a threshold for the number of MITRE ATT&CK tactics or techniques. If the number of MITRE ATT&CK tactics or techniques for some findings is greater than 10, those findings get nested together in the analyst queue. Similar findings Create a finding group when the count of similar findings or intermediate findings exceeds a threshold. If the number of similar findings is equal to 10, those findings get nested together in the analyst queue. Outbreak Create a finding group when a given field of findings exceeds a threshold of shared values. If the given field in a finding such as "src" or "dest" is equal to 10, those findings get nested together in the analyst queue. Sequence Create a finding group when specified findings occur in a sequence. If you select specific findings from the drop-down menu and they appear in the specified sequence, those findings get nested together in the analyst queue. Custom Create a finding group when specific custom conditions in a custom search are met. Enter a custom SPL search that specifies conditions and findings that meet those conditions get nested together in the analyst queue.
See also
For more information on findings and intermediate findings, see the product documentation:
Use findings for security monitoring in Splunk Enterprise Security
| Expand tokens in findings in Splunk Enterprise Security | Findings and finding groups in Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.31, 8.0.40
 Download manual
Download manual
Feedback submitted, thanks!