Manage analyst workflows using the analyst queue in Splunk Enterprise Security
Use the Analyst queue on the Mission Control page in Splunk Enterprise Security to view a list of findings and investigations in a centralized location for faster and easier triage.
You can triage findings for investigations as they are displayed on the Analyst queue. However, you cannot triage intermediate findings as they are not displayed on the Analyst queue.
You can configure whether a detection generates findings or intermediate findings. You can also group findings together as a finding group. Finding groups are displayed on the Analyst queue. You can expand the list of findings in a group in the Analyst queue.
The following actions can be performed on findings, finding groups, and investigations in Splunk Enterprise Security from the Analyst queue:
- Assign a finding or an investigation using the analyst queue
- View details of a finding or an investigation using the analyst queue
- Add or remove a finding or finding group from an investigation using the analyst queue
- Run playbook for a finding or an investigation using the analyst queue
- Copy link to a finding or an investigation using the analyst queue to collaborate in Splunk Enterprise Security
- Suppress finding from the analyst queue
- Run adaptive response actions using the analyst queue
The following figure is a screenshot of how the Analyst queue is displayed on the Mission Control page in Splunk Enterprise Security:
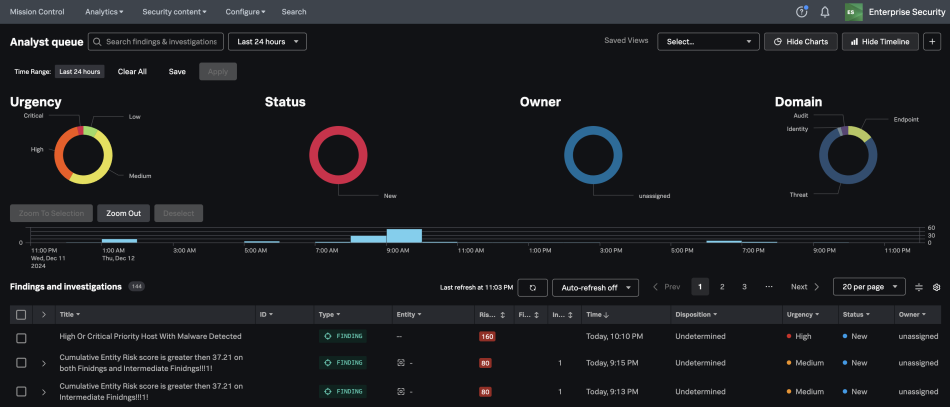
The following fields are displayed for the findings and investigations in the Analyst queue of the Mission Control page:
| Field | Description | Example |
|---|---|---|
| Title | Title of the finding or investigation. | Possible phishing attack |
| ID | Unique identifier for the finding or investigation in Splunk Enterprise Security. | ES-79845 |
| Type | Identifies whether the listed item is a finding or an investigation. | FINDING or INVESTIGATION |
| Entity | Name of the entity (asset or identity) for which the finding or investigation was created. | IP address such as 98.139.180.149 |
| Risk score | Numeric metric that shows the relative risk of the asset or identity such as a device or a user in your network environment for which the finding or investigation got created. | 420 |
| Findings | Number of contributing findings in a finding group or an investigation. | 4 |
| Intermediate findings | Number of intermediate findings in a finding group or an investigation. | 9 |
| Time | Time stamp when the finding or investigation got created. | Today, 10:20 AM |
| Disposition | Identifies the threat level associated with the finding. | Following are possible disposition values:
|
| Urgency | Value calculated using the severity of the finding and the priority of the asset or identity involved. | Following are possible urgency values:
|
| Status | Indicates the actions in the analyst workflow to address the finding or investigation. | Following are possible status values
|
| Owner | Owner assigned to review the finding or investigation. | Owners are unassigned by default. |
Notify an analyst of untriaged findings
You can use a detection SPL to notify an analyst if a finding is not been triaged.
Follow these steps to notify an analyst of findings that are not triaged:
- In the Splunk Enterprise Security app, select Security content.
- Select Content Management.
- Locate the Untriaged Notable Events detection using the filters.
- Modify the search, changing the finding owner or status fields as desired.
- Set the desired alert action.
- Save the changes.
- Turn on the Untriaged Notable Events detection.
Available features on the analyst queue in Splunk Enterprise Security
You can specify the time range for which you want to display findings and investigations in the Analyst queue. For example, select a time range such as 7 days in the Time range drop-down. The default time range is 24hours.
You can view the contributing findings in finding groups and investigations within the Analyst queue by selecting the caret next to the finding group or investigation. You can add a finding or a finding group into an investigation if it represents a security threat.
By using features such as filtering, saved views, shared views, and customizing table settings, you can surface or categorize findings and investigations by potential severity so that you can quickly audit, customize, triage, assign, and track security threats.
If you want to run a Search Processing Language (SPL) search in the analyst queue to filter for findings and investigations, you must wrap the search with double quotation marks. For example, "SPL SEARCH" . When using OR after your search, also add double quotation marks around the values. For example, OR (name="value" OR description="value" OR rule_name="value").
You can display a timeline visualization on the Mission control page for the findings and investigations in the Analyst queue by selecting Show timeline. You can also hide the timeline visualization by selecting Hide timeline. Additionally, you can zoom in, zoom out, and deselect specific findings and investigations on the timeline visualization.
You can display the urgency, status, owner, and domain distributions for the findings and investigations as chart visualizations by selecting Show charts. Additionally, you can hide the chart visualizations by selecting Hide charts.
You can add or remove a finding or an investigation directly from the Analyst queue. As a Splunk Enterprise Security administrator, you can also assign a finding or an investigation to yourself or view details. As an analyst, you can also assign a finding or an investigation to yourself or view details based on access permissions.
Assign a finding or an investigation using the analyst queue
Follow these steps to assign a finding or an investigation to yourself using the Analyst queue:
- In the Splunk Enterprise Security app, go to the Analyst queue on the Mission Control page.
- Select the three dots next to the finding or finding group to open a drop-down.
- Select Assign to me to assign the finding or an investigation to yourself based on access permissions.
View details of a finding or an investigation using the analyst queue
Follow these steps to add or remove a finding or a finding group from an investigation using the Analyst queue:
- In the Splunk Enterprise Security app, go to the Analyst queue on the Mission Control page.
- Select the three dots next to the finding or finding group to open a drop-down.
- Select Assign to me and view details to assign the finding or an investigation to yourself and view information on it based on access permissions.
Add or remove a finding or finding group from an investigation using the analyst queue
Follow these steps to add or remove a finding or a finding group from an investigation using the Analyst queue:
- In the Splunk Enterprise Security app, go to the Analyst queue on the Mission Control page.
- Select the three dots next to the finding or finding group to open a drop-down.
- Select Add to investigation to add a finding or a finding group to an investigation.
- Select Remove from investigation to remove a finding or a finding group from an investigation.
Run playbook for a finding or an investigation using the analyst queue
Follow these steps to run a playbook on a finding or investigation from the Analyst queue:
- In Splunk Enterprise Security, go to the Analyst queue on the Mission Control page.
- Locate a finding that you want to investigate further. Optionally use the search field, time filters, or both to focus the findings and investigations in the list.
- Select the box next to the finding or investigation that you want to investigate. Then select Run playbook.
- In the Run playbook window, select the playbook you want to run, then select Run playbook.
Messages show the status while the playbook runs. To see the status of all playbook runs for this finding or investigation, select the finding or investigation. Then in the details panel, review the Automation history and adaptive responses section. - Repeat these steps for additional findings or investigations. If you want to run the same playbook on several findings, investigations, or both, select the box next to each finding or investigation, then select Run playbook.
Suppress finding from the analyst queue
You can suppress findings from displaying on the Analyst queue. You can only suppress findings that are created by detections in the future.
Follow these steps to suppress findings from displaying on the Analyst queue:
- In the Splunk Enterprise Security app, go to the Analyst queue on the Mission Control page.
- Select the three dots next to the finding or finding group to open a drop-down.
- Select Suppress finding to open the Suppress finding dialog.
- In the Suppression name field, enter a name for the suppression.
- Specify the time for which you want to suppress the finding. For example, 1 day, 1 week, or Custom
- Expand Advanced and in the Description field, enter detailed information on the suppression.
- Select the fields based on which you want to suppress the findings. For example, event_hash, rule_name
- Select Save to save the suppression rule.
Run adaptive response actions using the analyst queue
You can run adaptive response actions from the Analyst queue on the Mission Control page. For more information on configuring and running adaptive response actions in Splunk Enterprise Security, see the product documentation:
- Configure adaptive response actions for detections in Splunk Enterprise Security.
- Run adaptive response actions in Splunk Enterprise Security
Follow these steps to run adaptive response actions from the Analyst queue on the Mission Control page:
- In the Splunk Enterprise Security app, go to the Analyst queue on the Mission Control page.
- Select the three dots next to the finding or finding group to open a drop-down.
- Select Run adaptive response actions to open the Adaptive response actions dialog.
- Select the adaptive response actions to run for the finding or investigation from the list of recommended actions. You can also configure new adaptive response actions.
- Select Run to run the adaptive response action.
See also
For more information on the analyst workflow in Splunk Enterprise Security, see the product documentation:
- Overview of Mission Control in Splunk Enterprise Security in the Use Splunk Enterprise Security manual.
- Triage findings and investigations in Splunk Enterprise Security in the Use Splunk Enterprise Security manual.
| Log files in Splunk Enterprise Security | Configure the settings for the analyst queue in Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.31, 8.0.40
 Download manual
Download manual
Feedback submitted, thanks!