Install and configure a Splunk Enterprise Indexer
This topic discusses installing the basic building block of a Splunk App for Windows Infrastructure deployment: a Splunk Enterprise indexer.
In this procedure, you will install the indexer and then configure it to receive data from other Splunk Enterprise instances.
Install the indexer
To install an indexer:
1. Prepare a host that meets or exceeds the Splunk Enterprise system requirements. During preparations:
- Write down the host name and IP address for the host.
- Ensure that no firewall blocks any network traffic into the host.
2. Download the Splunk Enterprise software onto the machine.
3. Install the correct version of the software for the operating system that the host runs.
4. After installation, confirm that the Splunk Enterprise software functions. At a minimum:
- The software should start without error. If it doesn't, try troubleshooting it.
- You should be able to perform a basic search using the Search app. Learn how. If that doesn't work, figure out why.
If everything checks out, configure the indexer to have the correct indexes for the Splunk App for Windows Infrastructure.
Configure indexes
The indexer must have the indexes for the Splunk App for Windows Infrastructure defined before you can begin indexing the data. The Splunk App for Windows Infrastructure installation package comes with a file that defines those indexes. Every indexer in a Splunk App for Windows Infrastructure environment needs this configuration file.
To get this file:
- In a web browser, proceed to the Splunk App for Windows Infrastructure download page.
- Click the download link to begin the download process.
- Make sure you download the latest version of the app.
- You might need to sign in with your Splunk account before the download starts.
- When prompted, choose an accessible location to save the download. Do not attempt to run the download.
- Use an archive utility such as WinZip to unarchive the file to an accessible location.
- Define your indexes.
- Create a
indexes.conffile inetc/apps/winfra/local/oretc/system/local - In
indexes.conf, define the msad, perfmon, and winevents indexes.
[msad] homePath = $SPLUNK_DB/msad/db coldPath = $SPLUNK_DB/msad/colddb thawedPath = $SPLUNK_DB/msad/thaweddb maxDataSize = 10000 maxHotBuckets = 10 [perfmon] homePath = $SPLUNK_DB/perfmon/db coldPath = $SPLUNK_DB/perfmon/colddb thawedPath = $SPLUNK_DB/perfmon/thaweddb maxDataSize = 10000 maxHotBuckets = 10 [winevents] homePath = $SPLUNK_DB/winevents/db coldPath = $SPLUNK_DB/winevents/colddb thawedPath = $SPLUNK_DB/winevents/thaweddb maxDataSize = 10000 maxHotBuckets = 10
- Create a
- Restart your Splunk platform instance. From the same PowerShell window:
> cd \Program Files\Splunk\bin > .\splunk restart
You can now configure the indexer to receive data from other Splunk instances.
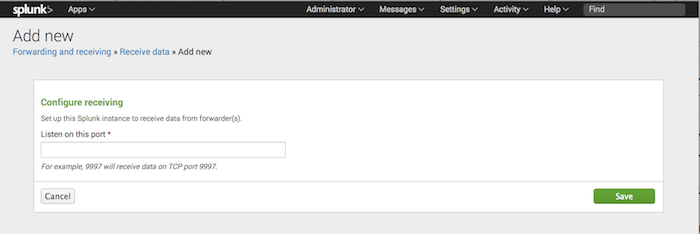
Configure receiving
The Splunk App for Windows Infrastructure depends on an indexer that can receive data from other hosts. Without this capability, the app cannot function. You will now enable receiving on this indexer.
To configure the indexer to receive data from other Splunk Enterprise instances:
1. Log into Splunk Enterprise on the indexer.
2. In the system bar, click Settings > Forwarding and Receiving. Splunk Enterprise loads the "Forwarding and Receiving" page.
3. Under "Receive Data" click Configure Receiving.
4. Click New.
5. In the Listen on this port field, enter the port number that you want Splunk Enterprise to listen on for incoming data from other Splunk instances. The conventional port number is 9997.
6. Click Save. Splunk Enterprise saves the port number and enables receiving on the indexer.
What's next?
With the indexer set up, you have begun the process of building out a Splunk App for Windows Infrastructure deployment.
Confirm that you have written down the host name or IP address and port number of the indexer. You will need it for the next step of the setup process.
Before you proceed, read our documentation on apps. You will create a simple app in the next step.
| How to deploy the Splunk App for Windows Infrastructure | Create the "send to indexer" app |
This documentation applies to the following versions of Splunk® App for Windows Infrastructure (EOL): 1.1.0, 1.1.1, 1.1.2, 1.1.3, 1.2.0, 1.2.1, 1.3.0, 1.4.0
 Download manual
Download manual
Feedback submitted, thanks!