Size and scale a Splunk App for Windows Infrastructure deployment
This topic discusses possible options in sizing and scaling a Splunk App for Windows Infrastructure deployment.
How to size an initial deployment
To initially size a Splunk App for Windows Infrastructure deployment and determine an initial hardware outlay, follow these guidelines:
1. Determine the number of machines that the environment should monitor.
- Count the number of Windows and Active Directory hosts in the network.
2. Determine the amount of daily indexing volume that will occur.
- Estimate your storage requirements. Build a test environment and log the following samples over a day:
- Active Directory data (from a domain controller and DNS server).
- Windows data (from a single Windows host)
- Multiply the figure for each data type listed above by the number of hosts in your environment that match the type.
- Add these figures together to come up with the estimated daily indexing volume.
- Estimate your storage requirements. Build a test environment and log the following samples over a day:
3. Determine the number of people who will have access to the app.
With these values you can determine how much of an initial hardware outlay you need:
4. See "Forwarder to indexer ratios" to determine how many indexers you need to handle incoming data streams from the forwarders.
5. See "Summary of performance recommendations" to determine how many search heads you should use in the environment based on indexing volume and number of people who will have access.
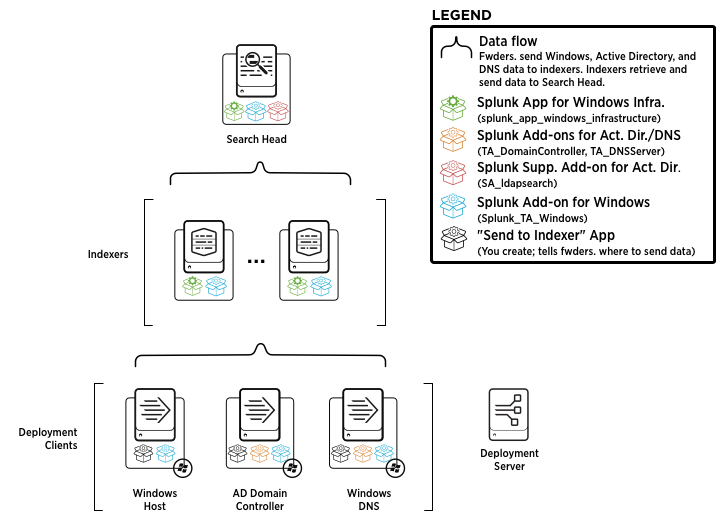
The following diagram depicts a typical distributed Splunk App for Windows Infrastructure Deployment:
Depending on the number of hosts in your deployment, add more indexers to deal with the indexing load.
How to scale an existing environment
When you install the Splunk App for Windows Infrastructure using the process described in this manual, you install most of the services on one host. This is to help you familiarize yourself with the Splunk Enterprise features as well as show that a single indexer based on Splunk Reference hardware can support such an installation.
However, in larger environments, running all components on one server is not feasible. Searching has a heavy impact on an indexer and multiple searches happening at once can overwhelm an indexer.
To address this problem, distribute the environment. You already have in a sense: universal forwarders on every host that provides data make the Splunk App for Windows Infrastructure environment distributed. The next step involves splitting out indexing and search operations into separate tiers to reduce performance pressure on both.
The general rules are:
- The more app users you have, the more indexers you should have. Splunk users create searches, and searches tax an indexer quickly. More indexers means more bandwidth for search heads to get data and return it to the requesting user. As numbers of users increase, you should add more search heads, which subsequently means adding more indexers.
- The more hosts with data you have, the more indexers you should have. While not nearly as harsh on indexers, a lot of data coming into one indexer can cause that indexer to bottleneck, reducing performance drastically. As indexing volume increases, you should add more indexers - at least one for every 1000 hosts.
- All environments differ. Because the Splunk App for Windows Infrastructure collects so much data, there is no one-size-fits-all calculation that you can make. A group that runs one version of Windows Server might collect far more data than another group that runs a different version. Fluctuations in network traffic and Active Directory usage patterns also determine how much indexing throughput you need.
See the Splunk Enterprise Capacity Planning manual for information on these concepts.
| Troubleshoot the Splunk App for Windows Infrastructure | Best practices guide |
This documentation applies to the following versions of Splunk® App for Windows Infrastructure (EOL): 1.1.0, 1.1.1, 1.1.2, 1.1.3, 1.2.0, 1.2.1, 1.3.0
 Download manual
Download manual
Feedback submitted, thanks!