Unify security operations using the capabilities of Splunk Intelligence Management
The capabilities layer in Splunk Intelligence Management unifies and automates all your data-centric security operations by connecting and leveraging intelligence across your ecosystem of tools, teams, and partners.
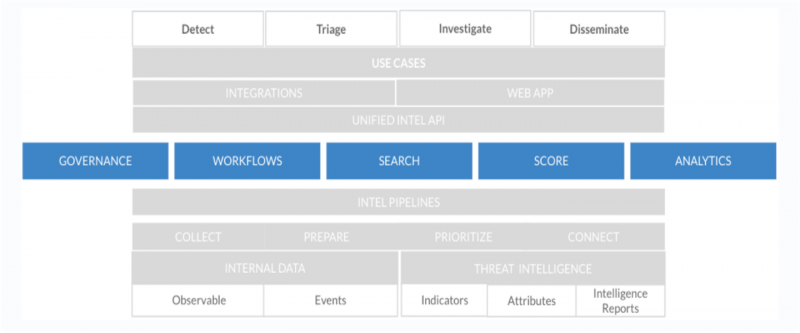
The following figure indicates the various capabilities within the multilayered architecture of Splunk Intelligence Management:
The following capabilities of Splunk Intelligence Management are critical to cybersecurity:
- Governance: To oversee data through role-based access and permissions.
- Workflows: To automate processing and distribution of data and insights.
- Advanced Search: To streamline indicator sets based on attributes and priority scores.
- Scoring: To rank data by prioritizing intelligence feeds or events.
- Analytics: To drive better strategic decisions to protect your organization.
Governance: Manage and control permissions
Use Splunk Intelligence Management to manage and control permissions, including multifactor authentication and enterprise-level single sign-on (SSO). The core of governance within Splunk Intelligence Management is the seamless control and secure dissemination of data using enclaves, which is the ultimate mechanism for data sovereignty.
Use enclaves to organize your intelligence
Enclaves organize your internal or external intelligence into a system of cloud-based repositories with strict access controls. Enclaves are flexible and customizable to meet your organization's unique data access-control requirements.
Typical enclaves include, but are not limited to the following types:
- Private enclaves: Store internal data submitted to Splunk Intelligence Management.
- Sharing community enclaves: Shared across ISACs or ISAOs. Available to any member of the ISAC or ISAO sharing community.
- Splunk Intelligence Management community enclaves: Available to all users of Splunk Intelligence Management. Any individual might submit information to this enclave.
- Intelligence source enclaves: Store the data from external third-party providers. When you subscribe to an external intelligence source, that intelligence gets stored in an enclave with the provider's name as the title.
Example of using enclaves
Enclaves can support many different uses. For example, the ISAO or ISAC has a goal to create a secure place for members to share cybersecurity information and intelligence. Splunk Intelligence Management works with these groups to build enclaves to support that goal:
- Member share enclave: Members can opt to share data to this enclave, However, member share enclaves are not curated.
- ISAO/ISAC approved enclave: Stores data from the member share enclave that gets cleaned and curated by group members or staff.
- Private enclave: Each member company has their own private enclave, which is only accessible to users from that company. Private enclaves provide the ability to filter shared information and redact it as part of the sharing process.
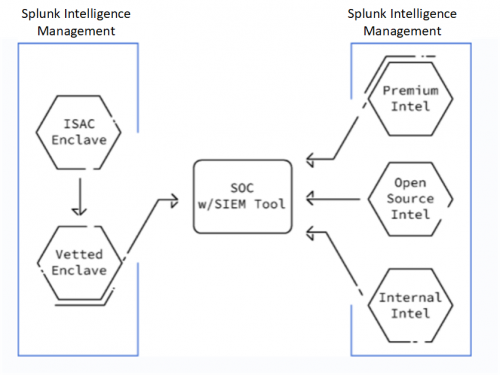
The following figure displays how a typical security operations center (SOC) uses a SIEM tool to access data through an approved enclave and intelligence sources in Splunk Intelligence Management:
Workflows: Automate data processing and distribution
An intelligence workflow is a no-code process to create customized intelligence pipelines that automate data processing. Setting up one or more intelligence workflows can provide quality data faster and help to make crucial security decisions.
Intelligence workflows have the following components:
- Sources: Intelligence sources or events
- Transformations: Priority scores, whitelists, and filtered attributes
- Destinations: Locations such as approved or shared enclaves or third-party security tools
Splunk Intelligence Management offers the following types of customizable workflows:
- Phishing triage: Collects submitted emails and prioritizes those email events using normalized scores and attributes of indicators from intelligence sources. The workflow stores those indicators and events in an approved enclave automatically or through human management so that they get used by security tools.
- Indicator prioritization: Collects indicators from selected sources and prioritizes them using normalized scores and attributes, filters the indicators by specific factors, and finally, sends the remaining indicators to an enclave or to a third-party tool.
To ensure that you receive data on time, create a maximum number of five workflows in a company. Additionally, you can only select a maximum of ten sources in a workflow.
Advanced search: Filter and streamline indicators
Splunk Intelligence Management provides advanced search and filter capabilities that leverage attributes, tags, and notes attached to the indicators. Use the Splunk Intelligence Management REST API or web app to search for an indicator to view a summary or deep dive into intelligence reports or events that contain the indicator.
You can filter indicator search results by attribute or priority score. Filtering lets you to streamline a group of indicators and use those indicators as a detection set for security alerts.
Splunk Intelligence Management stores all intelligence reports so that you can see the reports that contributed to the indicator summary. The reports provide additional context for decision-making.
For more information on refining reports and indicators in Splunk Intelligence Management, see Refine reports and indicators in Splunk Intelligence Management.
For more information on viewing intelligence reports in Splunk Intelligence Management, see View intelligence reports in Splunk Intelligence Management.
Scoring: Manage indicator and event to prioritize threats
The intelligence pipeline generates a single prioritized score for indicators or events. Splunk Intelligence Management provides two capabilities for managing those scores within workflows.
Indicator scoring
The intelligence pipeline generates a single priority score for indicators. You can streamline these priority scores within workflows by assigning weights to the intelligence sources used as input into the indicator prioritization workflow. Streamlining priority scores can help reduce false positive alerts by managing the fidelity of the indicators you import into your workflow tools.
Event scoring
Priority scoring of events such as log events or SIEM alerts lets you to build automation processes into triage workflows, extending the orchestration, and response capabilities of SOAR tools.
Analytics: Use analytics to detect and resolve threats faster
Organizations secure their systems to detect and resolve threats faster. The analytics in Splunk Intelligence Management provides two metrics that are key to analyze the performance of security systems:
- Mean Time to Detection (MTTD)
- Mean Time to Response (MTTR)
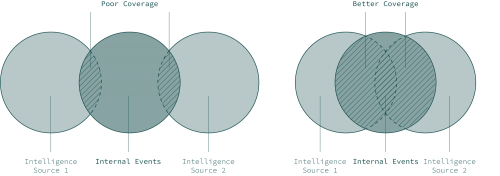
If the primary purpose of security intelligence is to accelerate automation that detects and responds to threats, then coverage is how you measure the effectiveness of your intelligence sources. You must learn how well those sources match with internal events and help to triage those events.
The following figure indicates how to define coverage by measuring the effectiveness of your intelligence sources:
You can track MTTD and MTTR metrics by using internal events and external intelligence feeds and determine the best way to increase your coverage. You can also use those metrics to understand the coverage provided by your subscribed intelligence sources. You can decide to retain or change sources, depending on what works best over time.
See also
| Normalize data from multiple sources using Splunk Intelligence Management | Use cases for Splunk Intelligence Management |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
 Download manual
Download manual
Feedback submitted, thanks!