Automate security operations using Splunk Intelligence Management
Use Splunk Intelligence Management to transform your intelligence to actionable automation across detection, triage, investigation, and dissemination use cases. The data-centric approach of Splunk Intelligence Management lets you to efficiently automate use-cases and reduce Mean-Time-to-Detection (MTTD) and Mean-Time-to-Response (MTTR).
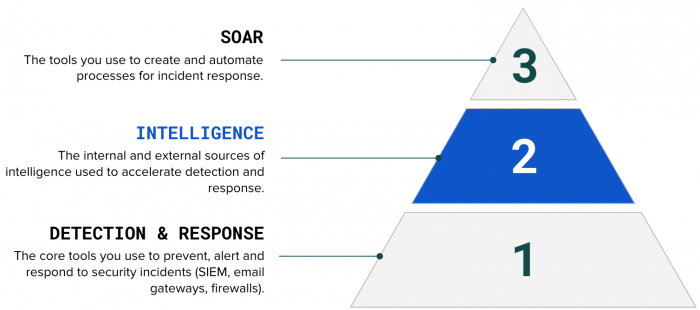
While automating data-centric security, you are usually required to manage intelligence separately from the applications that you use to automate actions. However, Splunk Intelligence Management serves as the "reasoning layer" that lets you to manage the intelligence sources upstream from your applications and deliver on the promise of Security Orchestration, Automation, and Response (SOAR) tools.
The following figure explains how Splunk Intelligence Management can transform your intelligence to actionable automation using your existing SOAR tools:
Splunk Intelligence Management provides maximum flexibility and integrates into your existing security environment using the following options:
- Use the pre-built integrations in Splunk Intelligence Management with third-party tools and apps.
- Build your own integrations using the REST API of Splunk Intelligence Management and Python SDK.
- Leverage the standalone web app for searching and contextual lookups across all your sources.
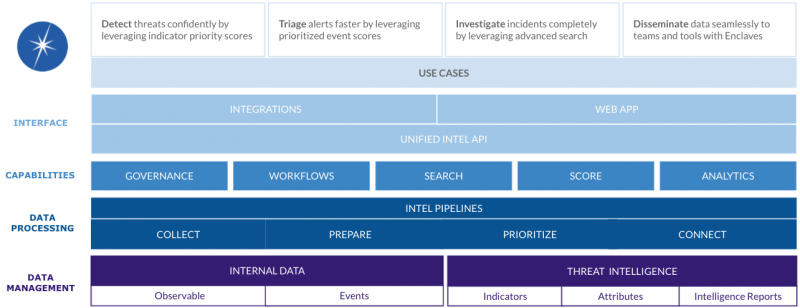
How does the multilayered architecture of Splunk Intelligence Management work?
Use the multiple layers of Splunk Intelligence Management to collect, prepare, prioritize and connect all internal and external sources of intelligence to your security operations tools and use cases.
The following diagram explains the various layers that comprise Splunk Intelligence Management:
- Data management and data processing: Focuses on core data operations, including collecting, managing, and processing the data.
- Capabilities: Displays what you can do with your data.
- Interfaces: Provides the options to leverage data across your tools and teams.
- Use cases: Explains how to use Splunk Intelligence Management within your security operations.
See also
- Add intelligence to improve data quality using Splunk Intelligence Management
- Normalize data from multiple sources using Splunk Intelligence Management
- Unify security operations using the capabilities of Splunk Intelligence Management
- Use cases for Splunk Intelligence Management
- Common terms in Splunk Intelligence Management
Videos to get started with Splunk Intelligence Management
See the following videos to get started with Splunk Intelligence Management:
-
Learn how Splunk Intelligence Management can help your security team.
Overview of Splunk Intelligence Management -
Begin your journey with Splunk Intelligence Management by following the initial configuration steps.
Getting started with Splunk Intelligence Management -
Learn how to install, configure, and use the Chrome extension for Splunk Intelligence Management.
Using the Splunk Intelligence Management Chrome extension - Learn about the Splunk Intelligence Management indicator enrichment playbook for Splunk SOAR.
Splunk Intelligence Management and Indicator Enrichment Playbook for Splunk SOAR - Learn how you can use Splunk Intelligence Management to save time from the manual handling and curation of indicators related to the Log4Shell threat and improve your investigations. Log4Shell vulnerability in the popular Apache Log4j 2 is a critical zero-day vulnerability that enables bad actors to run remote code execution (RCE).
Log4j Use Case
| Add intelligence to improve data quality using Splunk Intelligence Management |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
 Download manual
Download manual
Feedback submitted, thanks!