Overview of the Splunk Intelligence Management web app
Use the Splunk Intelligence Management web app to perform the following tasks:
- Set up workflows
- Lookup data and run advanced searches
- Delete and edit operations
- Search for data across all available enclaves
- Provision users and enclaves
- Manage permissions
- Manage safe-listing and redaction library
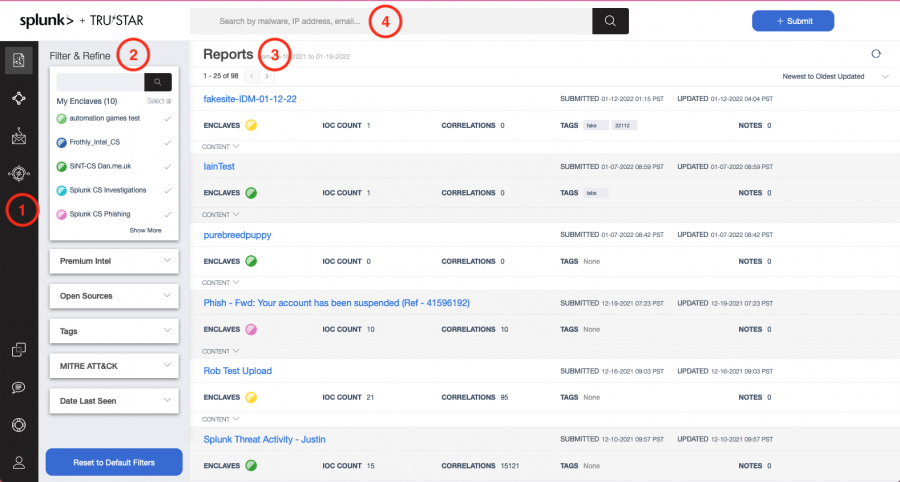
Use the following image as a guide to navigate the Splunk Intelligence Management web app home page:
The home page Splunk Intelligence Management web app includes the following major components:
| Number | Component | Description |
|---|---|---|
| 1 | Navigation bar | Get fast access to intelligence reports, indicators, and other features of Splunk Intelligence Management. See Use the navigation bar to access different features of Splunk Intelligence Management. |
| 2 | Filter and Refine panel | Select enclaves or intelligence sources and refine your selections as you drill deeper into an investigation. Use this panel when working with intelligence reports or indicators. See Use filters to refine reports and indicators in Splunk Intelligence Management. |
| 3 | Main panel | Display information related to the icon that is selected in the Navigation bar. For example, if you click the Reports icon, the main panel displays information about reports. |
| 4 | Search bar | Enter terms to search within the enclaves that are available to you. See Search for specific terms in reports and indicators in Splunk Intelligence Management. |
Access different features of Splunk Intelligence Management
Use the navigation bar to select specific features in Splunk Intelligence Management.
| Icon | Feature area | Description |
|---|---|---|
| Reports | Intelligence reports consist of structured and unstructured data stored in a specific enclave. Splunk intelligence Management extracts indicators in the report and enriches them with information from internal and external intelligence sources. Reports that are in the selected enclave of the Filter and Refine panel are displayed by default. For more information on searching reports, see Search reports and indicators in Splunk intelligence Management. | |
| Indicators | Indicators provide context to help you identify harmful activity on a network, such as a security breach or other suspicious incident. Internal information, such as cases, reports, or emails can contain data about an event on a network or device. These events contain observables such as URLs, hashes, or email addresses. When you send an event to Splunk Intelligence Management, the intelligence pipeline extracts, normalizes, and enriches the observables with the intelligence sources to which you have access, thus transforming them into indicators. | |
| Phishing Triage | Manage phishing emails. | |
| Intelligence Workflow | Use intelligence workflows for complex threat intelligence operations that require integrating data from multiple sources of intelligence. | |
| Marketplace | Many of the intelligence sources in the Splunk Intelligence Management marketplace are available immediately upon subscription, but certain paid and proprietary intelligence sources are only available after validation of API keys and credentials. The Splunk Intelligence Management Marketplace provides easy access to a variety of external intelligence sources from partners and other cyber-intelligence sources. Click the Marketplace icon on the navigation bar to view links to external intelligence sources and to applications that support a full integration with Splunk Intelligence Management.
You must be a company administrator to subscribe or unsubscribe to an intelligence source. | |
| Support | Access information FAQs to learn how to integrate with third-party sources and software. | |
| User Settings | Manage users, API access, redaction, and other advanced features in Splunk Intelligence Management. |
Access your API key
To perform actions such as write custom integrations between your data and the Splunk Intelligence Management platform, you need API keys. For more information on finding your API key, see Finding your API key.
| Collect observables using Splunk Intelligence Management |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
 Download manual
Download manual
Feedback submitted, thanks!