Configure the indicator prioritization intelligence workflow
Configure the indicator prioritization intelligence workflow to automate the extraction, transformation, and sharing of indicators. The indicator prioritization intelligence workflow is a no-code data pipeline designed to automate the extraction, transformation, and sharing of Indicators that meet your specific requirements.
You can set up multiple intelligence workflows to pinpoint responses or target data to specific tools in your cybersecurity setup. Intelligence workflows can reduce data wrangling, accelerate intelligence automation, and reduce false positives, making your team and your processes more efficient and more effective in making security decisions. For example, you may want one intelligence workflow to identify common malware Indicators and share that with one of your cybersecurity tools while another intelligence workflow rates and ranks IP addresses and domain names.
You must be a company administrator in Splunk Intelligence Management to create, edit, and delete intelligence workflows.
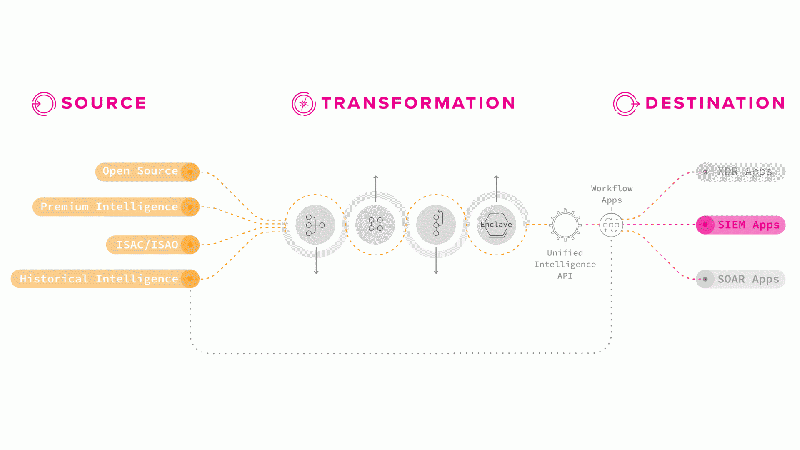
Each intelligence workflow has three stages you can customize to meet your needs:
- Inputs: Choose any of the intelligence sources available to you, either through premium subscriptions or open sources.
- Transformations: Filter the indicators from those sources by score and indicator type and remove any indicators that are on a specified safelist.
- Destination: You can then share the data set as a new Enclave or send it on to a third-party tool using Splunk Intelligence Management workflow apps or managed connectors. You can also use Splunk Intelligence Management's REST API and Python SDK to meet specific destination requirements.
See the following video to learn how to configure the indicator prioritization intelligence workflow and a safelist in Splunk Intelligence Management: Configure intelligence flows and indicator prioritization in Splunk Intelligence Management.
| Malware intelligence sources | Troubleshoot intelligence workflow |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
 Download manual
Download manual
Feedback submitted, thanks!