Use the phishing triage workflow to automate suspicious email triage
Splunk Intelligence Management's phishing triage intelligence workflow is designed to remove the manual, time-consuming tasks associated with the traditional triage process of user-reported suspicious emails.
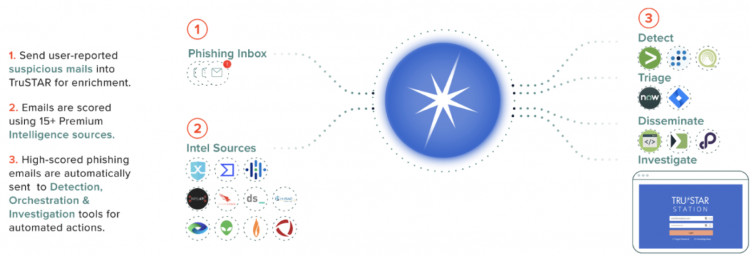
Splunk Intelligence Management automatically ingests suspicious emails, extracts observables, and enriches them from your choice of over fifteen intelligence sources to create a single normalized indicator score for each indicator. Splunk Intelligence Management uses those individual scores to assign a priority event score to the email that helps analysts surface the most relevant events for automated or human-in-the-loop investigation workflows.
See Use the REST API or Python SDK to access scored emails
See also *How to use the phishing triage workflow
Activate phishing triage
To activate the phishing triage intelligence workflow, contact Splunk Intelligence Management Support Portal and request activation. The feature activation includes creating two new enclaves:
- A phishing emails enclave, where events or emails will be submitted and processed.
- A phishing vetted indicators enclave, where scored events are stored.
Activation options
Use one of the following two methods to move indicators from the Phishing Emails enclave to the Phishing Indicators enclave:
- Automated workflow: Automatically moves all malicious indicators with a normalized indicator score of 1, 2, or 3 from scored emails that have a priority event score of 1, 2, or 3 to the Phishing Indicators enclave.
- Manual workflow: Automatically moves only the scored indicators with a normalized indicator score of 1, 2, or 3 from confirmed phishing emails that have a triage status of confirmed to the Phishing Indicators enclave.
By default, Splunk Intelligence Management activates the automated workflow when you request that phishing triage be configured. If you want to tranisition to the manual process, specify this when you request that phishing triage be activated.
Requirements to use the phishing triage feature
Ensure that you meet the following requirements to use the phishing triage feature:
- Activate an enclave inbox.
- Activate the automation of email forwarding.
- Subscribe to one or more external intelligence sources that you want to use to enrich the observables and provide priority scores for indicators and events. You can subscribe to sources through the Splunk Intelligence Management Marketplace.
Best practices
After your Splunk Intelligence Management account representative has configured the two enclaves for phishing triage, you can use the enclave inbox to configure a dedicated email inbox. This enables you to use and distribute this email address within your organization as a quick and easy way to submit suspected phishing events.
Splunk Intelligence Management does not decode URLs submitted by third party tools that have been encoded. Users who want to leverage the capabilities of Splunk Intelligence Management's phishing triage and indicator correlation must have their URLs decoded before submitting them to Splunk Intelligence Management. Contact the third party vendor's support team to decode URL's to use with Splunk Intelligence Management.
How phishing triage works
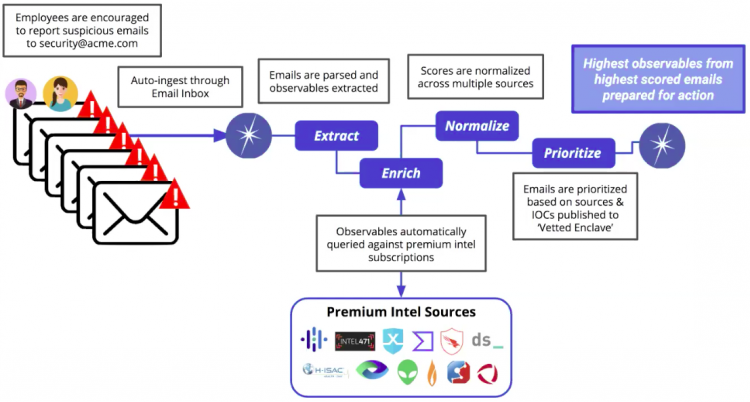
The phishing triage intelligence workflow provides a powerful, automated process that extracts the data you need to fight phishing in our organization.
- Submit: Use Splunk Intelligence Management's enclave inbox to auto-submit suspected phishing emails to a dedicated private enclave.
It can take up to four hours for a submitted phishing email to be completely processed with enrichment and scores. After the submission is processed, the report appears in the Phishing Triage dashboard. - Extract: Splunk Intelligence Management automatically parses the submitted emails and extracts the following observables:
- URL
- IP address
- Hashes: MD5, SHA1, SHA256
- Email address
- Enrich: Splunk Intelligence Management takes these observables and automatically queries the external intelligence sources that you subscribe, looking for correlations with historical Indicators. The Phishing Triage dashboard will not display enrichment beyond 30 days of the submission.
- Normalize: Each correlation provides a score, but each source uses a different scoring system, so Splunk Intelligence Management uses normalized indicator scoring to calculate a single comprehensive score for each Indicator.
- Prioritize: Splunk Intelligence Management indicates the priority of each email by assigning it a priority event score.
- Store: Finally, Splunk Intelligence Management sends the indicators to the Phishing Indicators enclave.
You can use the information in the Phishing Indicators enclave in any number of ways:
- Detect: Integrate with SEIMs such as IBM Q-Radar for automated hunting.
- Orchestrate: Create playbooks for advanced response and remediation. Demisto and ServiceNow are two Splunk Intelligence Management integrations that support the fast creation of phishing playbooks.
- Disseminate: Automate data sharing with other tools, teams, and groups using Splunk Intelligence Management's REST API or TAXII server.
| Work with safelist libraries as a transformation | Use the REST API or Python SDK to access scored emails |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
 Download manual
Download manual
Feedback submitted, thanks!