View intelligence reports in Splunk Intelligence Management
Use the Reports panel to view reports in the Splunk Intelligence Management web app. Access the Reports panel by clicking the Reports icon in the Navigation Bar.
The Reports panel has two views, each with a specific purpose:
- List view: Displays a list of reports that match the existing filters. This is the default view for reports. You can return to the List view by clicking on the Reports icon in the Navigation Bar.
- Graph view: Displays the details for a selected report. To see a report in Graph view, click the highlighted title of the indicator in the List view.
See the following video to learn about intelligence reports in Splunk Intelligence Management, what the reports include, how to review the reports, and how to manage reports: Working with intelligence reports.
List View to display reports
The list view of the Reports panel shows short summaries of all intelligence reports that match the current filter conditions you have set. This view shows the source enclave for the report, the number of Indicators, correlations, tags, and notes, as well as the date submitted and the date last updated.
- Use the Filter and Refine panel to narrow down the reports to what is most relevant to your investigation.
- Use the menu bar to page through reports and filter the reports by date and submission status.
- Use the drop-down menu to sort the display in the following ways:
- Newest to Oldest Updated (This is the default sort order.)
- Oldest to Newest Updated
- Newest to Oldest Submitted
- Oldest to Newest Submitted
Graph view to display reports
Click on an intelligence report in List view to display the details about that report in the Graph view. The Graph view shows visual links to related reports, enclaves, indicators, and other information.
Use the Graph view to drill down on analysis, filter out irrelevant nodes, add notes or tags, and adjust the timeline of correlations based on your requirements. You can also use the Graph view to view the full JSON report content and the graph visualization of correlations.
The first menu bar displays the following parameters:
- Date Range: You can select 1 day, 7 days, 1 month, 6 months, or maximum (entire date range for the report). A bar graph displays the data range.
- Labels (gear icon): Turns labels on or off (default) for the constellation points.
- Download (down arrow icon): Exports the Indicator data from the Report.
The second menu bar displays the following parameters:
- Filter by Indicators, sources (enclaves), or tags
- Search
- Next report from the List view
- Undo last action
- Redo last action
- Reset to the original view of the report
The main panel displays a graph of the report with links to indicators and tags from the report. The following example shows the original report surrounded by links to tags, URLs, and other Indicators found in the Report.
In the following image, Splunk Intelligence Management community enclave stores the report. The report displays with the Splunk Intelligence Management logo.
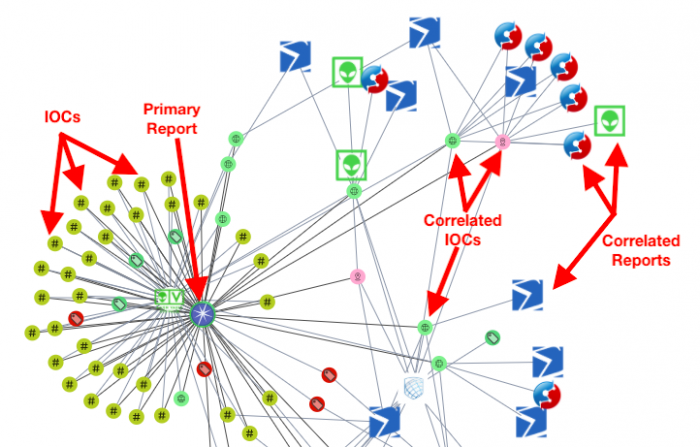
- A Report node represents information collected from a number of different sources, including user-reported incidents, and intelligence sources. The Report node displays the icon specific to the enclave that stores the report.
- An Indicator of Compromise (IoC) node represents all indicators extracted from a specific report. These nodes are represented with smaller icons specific to the data source.
- A Tag node represents tags applied to a report or Indicator and is visually depicted on the graph. Reports branching off the tag share the same tag, contain at least one correlating Indicator, and are present in the same timeline.
A Report node contains one or more IoC nodes. When two different Report nodes contain the same Indicators, they are implicitly correlated to each other and you can see that connection in the lines between the Indicators and the Reports that contain them. CVEs, Threat Actors, and Malware correlations default to hiding second-order correlations to reduce the noise in Graph view.
You can right-click on any item to see a four-part circular menu. Depending on the item, you can choose whatever items are not grayed out.
Details panel
The Details panel displays information in three different sections: Breadcrumb Trail, Report Metadata, and Extracted Indicators.
The Breadcrumb Trail is a convenient way to track the previous detail pages that you've visited while navigating a graph. Clicking on a graph node appends it to the left hand side of the breadcrumb trail, which allows you to revert back to that node by clicking on its respective breadcrumb.
The Report Metadata displays the metadata for the report, including report title, date of submission, date of last update, and the enclave in which it is stored
To view the entire Report, click View Full Report.
The three dots in the upper right corner contain commands to:
- Update the report if you have permission to write to that enclave
- Copy the report to another enclave
- Move the report to another enclave
- Export the report
The Expand icon (four arrows) displays the full data of the report and hides the Extracted Indicators.
The Report Summary displays details that analysts would find most relevant to their analysis. The Report Summary shows a tabular format of the most relevant extracted details, which might vary from source to source and might include details like risk or confidence score, actors associated, malware families associated, kill chain stages, relations reported, and so on.
Click the target icon next to Tags to view tags by enclave. You can add tags to the report by selecting a tag from the menu list for an enclave. Any tags you add are visible to all viewers of the selected enclave and editable by all viewers of that enclave. Tags you add are immediately added to the report and need not be saved. Tags are limited to 32 characters.
Click the target icon next to MITRE ATT&CK to view those tags by enclave. After making changes, click the Save button to commit the changes to the selected enclave.
View extracted indicators
The Details panel shows the list and count of Indicators extracted from the report.
You can use the icons to manipulate the display:
- The A-Z icon reverses the sort direction of the list.
- The Search icon and text field locates instances of a specific term.
- The Eye icon whitelists selected indicators. Click the eye icon next to the Indicator that you want to add to the whitelist.
- The Expand icon (four arrows) shows the entire list of extracted indicators and hides the Report Details section.
Extracted Indicator - Card Front Side
All extracted Indicators are shown as individual information cards.
The logo of the intelligence source is displayed along with any risk score/confidence score/malicious score provided by the source. The type and value of the Indicator is also shown. On the right, you see two controls:
- the top control lets you flip the card to see its backside
- the bottom control shows the Indicator in graph view.
Extracted Indicator - Card Back Side
The back side of each Indicator card displays details of last seen, number of sightings, and number of user-generated notes for that Indicator.
On the right, you see two controls:
- the top control lets you flip the card to see its front side
- the bottom control shows the Indicator in graph view.
| Enable users on Splunk Intelligence Management using Salesforce | Submit intelligence reports to add data to your enclaves |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
 Download manual
Download manual
Feedback submitted, thanks!