Get started on the Splunk UBA home page
Begin using Splunk User Behavior Analytics (UBA) by logging in to the Splunk UBA web interface on the management server of your deployment.
Log in to the Splunk UBA web interface
In a supported web browser, type in the IP address or host name of your Splunk UBA management server to access the Splunk UBA web interface. If you are logging in for the first time, use the default Splunk UBA credentials of admin as the username, and changeme as the password.
After you log in, perform the tasks in Secure the default account after installing Splunk UBA in Install and Upgrade Splunk User Behavior Analytics.
The IP address you specify may differ slightly depending on your operating system environment. For example, in Linux environments, you specify the IP address of the Splunk UBA management server, but for Amazon Web Services (AWS) environments, you specify the public IP address to access Splunk UBA.
See the end of the installation instructions for your specific environment in Install Splunk User Behavior Analytics in Install and Upgrade Splunk User Behavior Analytics.
Start using Splunk UBA on the Splunk UBA home page
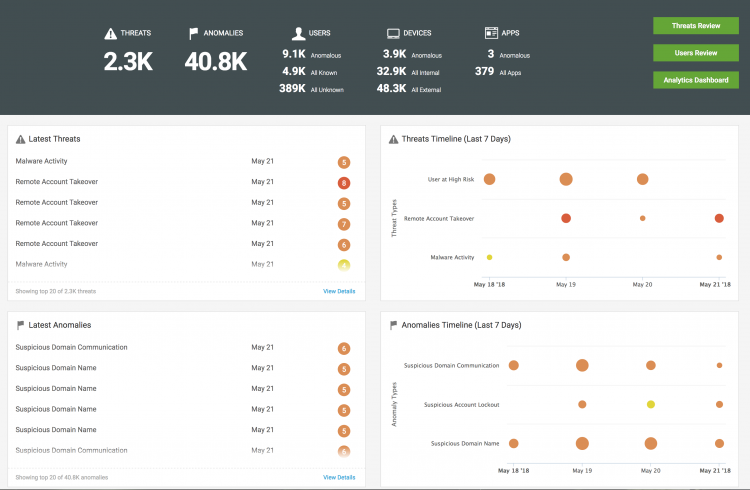
After you log in to Splunk UBA, you see the home page. Review the key indicators and panels to get an overview of the current security posture in your environment.
Review key indicators
The following key indicators are available at the top of the home page:
| Key indicator | Description |
|---|---|
| Threats | Summarizes the total number of active threats in your environment. |
| Anomalies | Summarizes the total number of anomalies in your environment. |
| Users | Summarizes the total number of anomalous, known, and unknown users. |
| Devices | Summarizes the total number of anomalous, internal, and external devices. |
| Apps | Summarizes the total number of anomalous apps compared with the number of total apps. |
Start investigative workflows
Using the green buttons on the right side of the home page, you can start several investigative workflows:
- Select Threats Review to start investigating threats. See Investigate threats as a security analyst.
- Select Users Review to review current user activity. See Review current user activity.
- Select Analytics Dashboard to review recent login activity and data transfer patterns.
Review dashboard panels
Get an overview of recent suspicious activity by reviewing the dashboard panels:
| Dashboard panel name | Description |
|---|---|
| Latest Threats | See the most recent threats facing your organization. Click View Details to open the threats table and view all threats. |
| 7-Day Threats Timeline | Track threats and identify recent trends in threat activity. |
| Latest Anomalies | See the most recent anomalies identified in your organization. Click View Details to open the anomalies table and view all anomalies. See, Review anomalies on the anomalies table. |
| 7-Day Anomalies Timeline | Identify recent anomalies. |
| Events Processing | Make sure that event processing is flowing as expected. Click the number of events to review the Events dashboard. |
| 7-Day Events Trend | Identify any unexpected changes in event processing. |
Filter the scope of anomalies and threats
Click Scope on the menu bar to filter the anomalies and threats that are displayed in Splunk UBA. By default, anomalies and threats for all time are displayed. You can select one of the options to view anomalies and threats for a specific period of time. Any Date is used as the default.
Entity scoring for users, devices, and apps is affected by adjusting this filter. Entity scoring occurs automatically on a daily basis.
| Scope Selected in Splunk UBA | How the Scope Affects Entity Scoring |
|---|---|
| Any Date (Default) | Entity scoring is based on anomalies and threats from the past 2 months. This window of time can be customized by adjusting the entity.score.lookbackWindowMonths property in the /etc/caspida/local/conf/uba-site.properties file.
|
| Last 12 Months | Entity scoring is based on anomalies and threats from the past 2 months. This window of time can be customized by adjusting the entity.score.lookbackWindowMonths property in the /etc/caspida/local/conf/uba-site.properties file.
|
| Last 30 Days | Entity scoring is based on anomalies and threats from the past 30 days. |
| Last 7 Days | Entity scoring is based on anomalies and threats from the past 7 days. |
Entity scoring occurs in real time when new anomalies are raised, or when existing anomalies are placed in the trash, permanently deleted, or restored.
Some anomaly actions can cause real-time entity scoring adjustments and it might take up to 24 hours before the updated scores are reflected in Splunk UBA.
| Change user profile settings in Splunk UBA |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.1.0, 5.1.0.1, 5.2.0, 5.2.1, 5.3.0, 5.4.0, 5.4.1, 5.4.1.1, 5.4.2, 5.4.3
 Download manual
Download manual
Feedback submitted, thanks!