Splunk UBA version 5.3.0 includes two new VPN login related anomaly detection batch models:
- Abnormal VPN Session Associated with Rare Location
- Changepoint Model for VPN Location of Authentication Events
| Model name | Description | Tables used | Anomalies generated |
|---|---|---|---|
| Abnormal VPN Session Associated with Rare Location | Detects abnormal VPN session associated with rare login geolocation. | semiaggr_s, windowsevents, fileaccess_s
|
Abnormal VPN Session From Rare Location |
| Changepoint Model for VPN Location of Authentication Events | Detects location changepoint in VPN authentication events. | semiaggr_s
|
VPN Location Changepoint |
Abnormal VPN Session Associated with Rare Location
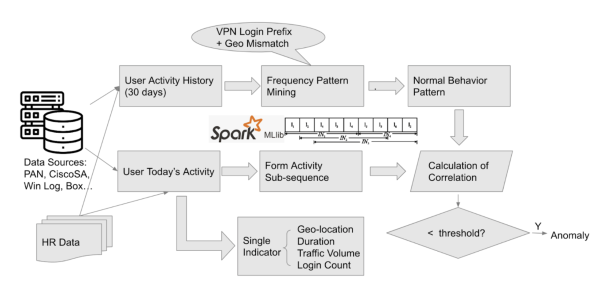
The model finds unusual patterns of activities on the same day of VPN logins, and determines whether the corresponding login is abnormal. The following diagram shows the detection logic of the model:
This Abnormal VPN Session Associated with Rare Location model is designed to detect abnormal VPN sessions through pattern mining of post-VPN login activity sequence.
This model is computationally expensive and might take a long time to run. You can tune the model parameters such as memory, which defines the length of historical data to train the model. The smaller the value, the less computation resources are used. You can also tune the anomalyScoreThreshold, which defines the threshold of frequent patterns to be considered as anomalous. The larger this value, the less computation resources are used.
The model uses the following data fields from semiaggr_s cubes to form behavioral sequence for pattern mining:
- Number of events (
numEvents) - Event Description (
evcls) - Source User Identification Number (
sourceUserId) - Source Country (
sourceCountry) - Source City (
sourceCity) - Destination Country (
destinationCountry) - Destination City (
destinationCity)
Standard configuration also includes two supportive fields from another two cubes that manifest user or entity behaviors after VPN logins:
- Event ID (
eventId) from cubewindowsevents - Service Name (
serviceName) from cubefileaccess_s
If data sources to generate these two cubes are not available, the pre-defined supportive fields are automatically ignored by the model. The model does not assume a specific event ID, or specific service to be abnormal or a threat. Instead, the model mines the frequent patterns of occurrence of these fields, in addition to the feature fields in semiaggr_s cube to detect unusual events.
This model has the capability to detect unknown threats. You can re-define the supportive fields by modifying, removing, and adding fields based on available data sources in your environment. The definition of any customized supportive fields can be placed in the /etc/caspida/local/conf/modelregistry/offlineworkflow/ModelRegistry.json file. The number of supportive fields is not restricted but is dependent on the computation capacity (memory and run time). Each supportive field must be defined as a fixed three item tuple, including the cube name, ID to match user identification, and indicator field as shown in the following example:
{
"models" : [
{
"name": "Abnormal_VPN_Session_Model",
"params": {"supportiveFeatureList":
["windowsevents", "sourceUserId", "eventId"],
["fileaccess_s", "originatingUserId", "serviceName"]
}
}
]
}
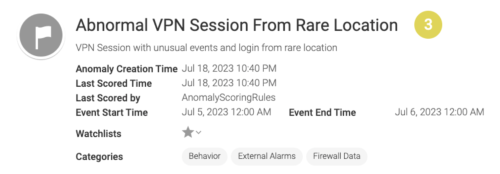
The anomaly detected by this model is named as Abnormal VPN Session From Rare Location. You can select a detected anomaly from the Anomalies Table and navigate to a detailed view and shown in the following image:
The detailed view shows why this anomaly is flagged and includes the following information:
- Summary of the account associated with anomaly
- VPN origin and destination country/city
- VPN Events of the event(s) associated with this VPN session
- Rare Values and Associations of up to three rare values or activities associated with VPN events
Changepoint Model for VPN Location of Authentication Events
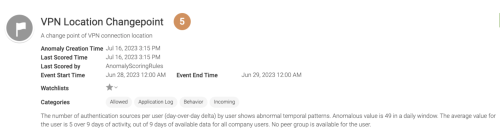
This model detects the changepoint of VPN login geolocations. The model finds a changepoint by tracking the average value of the ratio between unique source points and servers, as an indicator of abnormal geolocation login from a user. Geolocation is represented by IP address differences, the accuracy of which is dependent upon updates to the IP address mapping database. By default the model looks back at one month of historical data to evaluate changepoints.
The model uses semiaggr_s cube as the data source. The anomaly detected by this model is named as VPN Location Changepoint. Each anomaly is illustrated its support evidence starting with a summary description as shown in the following image;
In addition to regular time-series related anomaly analytics fields and drilldown data, other support evidence in the investigation page include the following:
- Login user ID
- Source country of authorization
- Event description
| Lateral Movement model | Time-series models |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.3.0, 5.4.0, 5.4.1, 5.4.1.1, 5.4.2, 5.4.3
 Download manual
Download manual
Feedback submitted, thanks!