Review Peer Groups in Splunk UBA
For each user, user account, or device, Splunk User Behavior Analytics (UBA) finds other entities most similar in behavior, (called "peers") and groups these similar entities together using clustering methods. For users, these groups are called Peer Groups, and for devices these groups are called Device Groups.
Peer Groups are defined by patterns of similar behavior by accounts. Splunk UBA identifies behavior patterns in login activity, AD events, and the sources and destinations from which accounts are accessed to determine the behavior peers for accounts.
Device Groups are defined by patterns of similar behavior by devices.
Peer Group limitations
Peer groups update on a daily basis.
Only accounts with AD activity can be in user peer groups. Each account with AD activity belongs to exactly one behavior account peer group.
Splunk UBA considers several different behavior attributes when computing peer groups, such as login and session activity and AD group membership. Some data science models use different groups as a factor in anomaly creation and scoring. For example, the User Exfiltration and the Filter models use the organizational unit (OU) peer group.
Only devices with network traffic activity and firewall-relevant data can be in device peer groups. Each device belongs to exactly one device peer group.
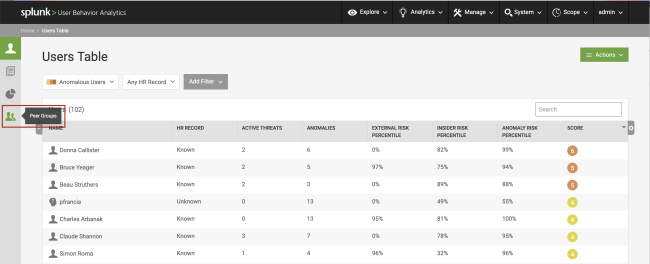
View Peer Groups for Users
You can view the peer groups for users on the User Accounts page. See User Accounts. You can view the peer groups for an account on the Peer Groups page. See Peer Groups.
To see all the user and account peer groups in your environment, select Explore > Users to open the Users Table. You can then select the Peer Groups icon on the left menu.
The following types of peer groups are available:
- Behavior Account Groups: These groups are defined by patterns of similar behavior by accounts. Splunk UBA identifies behavior patterns in login activity, AD events, and the sources and destinations from which accounts are accessed to determine the behavior peers for accounts. Each account belongs to exactly one peer group.
- OU User Groups: These groups are defined by the organization units (OU) specified in the HR data added to Splunk UBA.
- AD Account Groups: These groups are defined by the active directory (AD) privilege groups specified in the HR data added to Splunk UBA.
- HR Peer Groups: These groups are defined by similar properties shared between user accounts. Properties are defined in the active directory (AD) provided in the HR data added to Splunk UBA.
Each circle represents a group, and the number represents the number of accounts within that peer group. Select any circle.to view the members and view the breakdown of members of that peer group.
You can use Add Filter to learn more about the types of accounts in the peer groups. The circles change color to reflect your filters, with the light blue circle representing the number of accounts that match the filters you select. The number in the circle also changes to reflect how many accounts from the peer group match the filters.
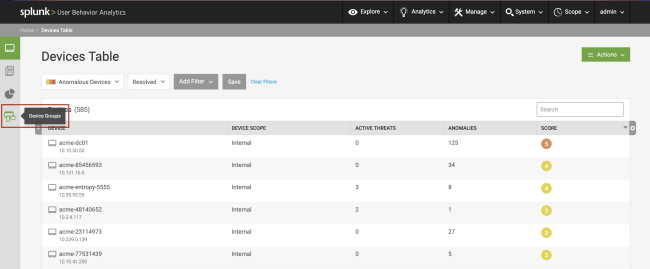
View Device Peer Groups
To see all the device peer groups in your environment, select Explore > Devices to open the Devices Table. You can then select the Device Groups icon on the left menu.
On the Device Groups page you can view the number and size of device groups identified by Splunk UBA in your environment. Hover over a device group to learn more about why Splunk UBA grouped the devices together in that group.
You can use Add Filter to identify which devices in a device group match a set of criteria. For example, add a filter of Anomalies Count >= 1 to identify devices involved in anomalies. Select an affected device peer group to view the list of devices in the device peer group.
Select any Device Group to review the list of devices in the device peer group, and a summary of the behaviors causing the devices to be grouped.
| Review overall user activity | Investigate threats as a security analyst |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.0.5, 5.0.5.1, 5.1.0, 5.1.0.1, 5.2.0, 5.2.1, 5.3.0, 5.4.0, 5.4.1, 5.4.1.1, 5.4.2, 5.4.3
 Download manual
Download manual
Feedback submitted, thanks!