Use custom search commands for the Splunk Add-on for BMC Remedy
The Splunk Add-on for BMC Remedy includes four custom generating search commands:
remedyincidentcreate remedyincidentupdateremedyincidentcreaterest remedyincidentupdaterestBefore you can use these commands, set up the Splunk Add-on for BMC Remedy and update the required fields in the remedy_fields.conf file to match the required fields in your Remedy installation.
Use the remedyincidentcreate custom generating search command
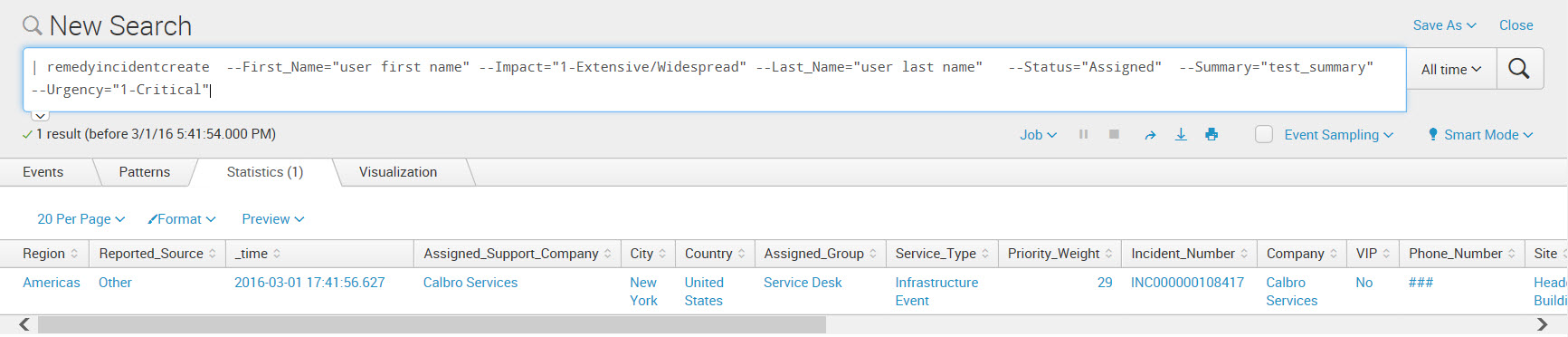
The remedyincidentcreate custom generating search command creates an incident in your Remedy system.
When you execute the command successfully, the Splunk platform displays a table with information about the incident, as in the example below.
The required arguments are listed in the [create_incident] stanza of the remedy_fields.conf file. See Specify required fields for incidents for information.
Because Remedy is highly customizable, when you run an incident create or update command from the Splunk platform, some fields in your Remedy incident may be populated based on form definitions and business rules set up in your Remedy system rather than the arguments supplied with the command.
To add any custom fields for '''creating''' incidents with the BMC Remedy ITSM setup, you must pass it as an argument in the | remedyincidentcreate command. Make sure that fields are configured in your BMC environment and are present in WSDL.
Run | remedyincidentcreate --help to show the usage of this command. Arguments in brackets are not required.
Example remedyincidentcreate command that creates a new incident in Remedy
The search below creates a new incident in Remedy.
| remedyincidentcreate --First_Name="Mary" --Last_Name="Mann" --Impact="1-Extensive/Widespread" --Status="Assigned" --Summary="test_summary" --Urgency="1-Critical" --Custom_Test_Field="test field"
Use the remedyincidentupdate custom generating search command
The remedyincidentupdate custom search command updates existing incidents created from the Splunk platform. When you execute the command, the Splunk platform displays a table with information about the event.
You can't use this command to update incidents created in Remedy, only those created from the Splunk platform.
Run | remedyincidentupdate --help to view the usage. Arguments in brackets are not required.
The required arguments are listed in the [update_incident] stanza of the remedy_fields.conf file. See Specify required fields for incidents for information.
Because Remedy is highly customizable, when you run an incident create or update command from the Splunk platform, some fields in your Remedy incident may be populated based on form definitions and business rules set up in your Remedy system rather than the arguments supplied with the command.
To add any custom fields for '''updating''' incidents as per the BMC Remedy ITSM setup, you must pass it as an argument in the | remedyincidentupdate command. Make sure fields are configured in BMC environment and must be present in WSDL.
Example remedyincidentupdate command that updates an incident in Remedy
The search below updates a Remedy incident created from the Splunk platform.
| remedyincidentupdate --Incident_Number="INC000000107859" --Status="Assigned" --Summary="updated --Custom_Test_Field="test field updated"
Use the remedyincidentcreaterest custom generating search command
The remedyincidentcreaterest custom generating search command creates an incident in your Remedy system.
When you execute the command successfully, Splunk displays a table with information about the incident.
The required arguments are listed in the [create_incident_rest] stanza of the remedy_fields.conf file. See Specify required fields for incidents for information.
Because Remedy is highly customizable, when you run an incident create or update command from the Splunk platform, some fields in your Remedy incident may be populated based on form definitions and business rules set up in your Remedy system rather than the arguments supplied with the command.
To use the custom fields in these commands, you have to pass || separated key-value pairs of custom fields and values as part of --custom_fields argument in the command. All the parameters which are passed in the --custom_fields are needed to be configured first in the BMC Remedy instance. Parameters passed in custom fields must be present in BMC Remedy incident form.
There is a restriction on which fields can be provided directly. The fields which can be provided directly can be found here. In addition to the fields mentioned in the list, others need to be provided in the custom fields parameter.
Run | remedyincidentcreaterest --help to show the usage of this command. Arguments in brackets are not required.
Example remedyincidentcreaterest command that creates a new incident in Remedy
The search below creates a new incident in Remedy.
| remedyincidentcreaterest --account "Account_1" --First_Name "Michael" --Last_Name "Faraday" --Status "Assigned" --Impact "1-Extensive/Widespread" --Urgency "1-Critical" --Service_Type "User Service Restoration" --"Reported Source" "Direct Input" --Description "Hello1" --custom_fields "customfield1=value1||customfield2=value2"
Make sure you pass in the --account parameter, and with the value as the name of the account configured on the Rest Account page.
Use the remedyincidentupdaterest custom generating search command
The remedyincidentupdaterest custom generating search command updates an incident in your Remedy system.
When you execute the command successfully, the Splunk platform displays a table with information about the incident.
The required arguments are listed in the [update_incident_rest] stanza of the remedy_fields.conf file. See Specify required fields for incidents for information.
Because Remedy is highly customizable, when you run an incident create or update command from the Splunk platform, some fields in your Remedy incident may be populated based on form definitions and business rules set up in your Remedy system rather than the arguments supplied with the command.
To use the custom fields in these commands, you have to pass || separated key-value pairs of custom fields and values as part of --custom_fields argument in the command. All the parameters which are passed in the --custom_fields are needed to be configured first in the BMC Remedy instance. Parameters passed in custom fields must be present in BMC Remedy incident form.
There is a restriction on which fields can be provided directly. The fields which can be provided directly can be found here. In addition to the fields mentioned in the list, others need to be provided in the custom fields parameter.
Run | remedyincidentupdaterest --help to show the usage of this command. Arguments in brackets are not required.
Example remedyincidentupdaterest command that updates an incident in Remedy
The search below updates an incident in Remedy.
| remedyincidentupdaterest --"Incident Number" "INC000000014106" --account "Account_01" --Status "Assigned" --"Reported Source" "Direct Input" --Description "Hello9999" --custom_fields "customfield1=value1||customfield2=value2"
Make sure you pass in the --account parameter, and with the value as the name of the account configured on the Rest Account page.
| Overview of the commands available with the Splunk Add-on for BMC Remedy | Use custom streaming commands for the Splunk Add-on for BMC Remedy |
This documentation applies to the following versions of Splunk® Supported Add-ons: released
 Download manual
Download manual
Feedback submitted, thanks!