How to use the phishing triage workflow
You can use the Phishing Triage panel in the Splunk Intelligence Management web app to view, filter, and manage phishing events submitted by users in your organization. By default, these events are submitted into the Phishing Events enclave.
How it works
Phishing triage uses automation to perform the following tasks:
- Extract and enrich indicators from specified intelligence sources
- Normalize scores from those sources into a single normalized indicator score
- Assign a priority event score using the normalized indicator scores
You can then use the Phishing Triage Panel in the Splunk Intelligence Management web app for the following tasks:
- View phishing events that need review
- Filter by Date, Priority Event Score, or Intel Report Status
- Confirm or ignore an intelligence report
Access the Phishing Triage panel
To display the Phishing Triage panel, click the Phishing Triage icon on the Navigation Bar. If you do not see the Phishing Triage icon on your Navigation Bar, contact your Splunk Intelligence Management account representative about activating this feature.
Filter phishing reports
You can use the buttons on the Phishing Triage menu bar to control which intelligence reports are displayed.
Filter options:
- Include Unknown Scores: Events with no correlated Indicators are scored as Unknown, so these are probably of low interest when investigating phishing events.
- Score Filter: Choose to display events that have a specific priority event score.
- Status: Display events that you have confirmed as malicious, ignored as non-malicious, or left unresolved while investigations continue.
- Date: Choose the date range of the events you wish to review.
Viewing a single phishing report
Each event submitted to the Phishing Emails enclave is displayed as a separate card. The card front summarizes the event, including the title (usually the email subject), dates of submission and any updates, and the source Enclave.
- Click on the Priority Event Score to display a count of indicators by normalized indicator scores.
- To view a detailed list of the indicators, click the Grid icon in the upper right of the card. This opens the Breakdown by Source card view where you can see the normalized indicator scores listed by enclave.
If the event has been assigned a status, the grid icon is not displayed.
Opening the event in graph view
To view the full event in a new Splunk Intelligence Management web app window, click the Reports Graph view icon in the upper right. This opens the event in Reports Graph view, where you can use the power of that view to explore details and correlations.
Confirm or Ignore a Report
To confirm that an event is a phishing attack, click the Confirm Risk button in the lower right corner.
To confirm that the event is not malicious, click Ignore in the lower right corner.
Export confirmed indicators
After you have confirmed a series of events as malicious, you can export the indicators in those confirmed events and use them in other tools within your organization.
- Filter by Status to display all confirmed events.
- Click the Download Indicators button to export all the Indicators in .csv format.
Use phishing triage with detection tools
You can connect the Phishing Indicators enclave in the phishing triage intelligence workflow to your detection tools and workflows.
Splunk Enterprise Security
- In the Splunk Intelligence Management support document for Splunk Enterprise Security, go to the Creating Inputs to Splunk ES section and follow the steps to connect the Phishing Indicators enclave to your Splunk Enterprise Security installation.
LogRhythm
- In the Splunk Intelligence Management support document for LogRhythm, follow the steps in "Configuring the TAXII Client" to connect the Phishing Indicators enclave to your LogRhythm installation.
IBM QRadar
- In the Splunk Intelligence Management support document for IBM QRadar, follow the steps to connect the Phishing Indicators enclave to your IBM QRadar installation.
Use phishing triage with orchestration tools
You can use information created by the phishing triage intelligence workflow within your orchestration tools. Obtaining information such as normalized indicator scores or priority event scores can then be wrapped into a playbook that further automates the investigation and management of phishing emails.
This functionality is currently only offered within Demisto.
Phishing triage in Splunk Intelligence Management provides access to the following tasks in Demisto:
- Get phishing submissions
- Get phishing indicators
- Set triage status
Get phishing submissions
Purpose: Fetches emails submitted to the Phishing Triage enclave in Splunk Intelligence Management.
!trustar-get-phishing-submissions
Task input
| Parameter | Description |
|---|---|
| priority_event_score | Score of email submission. |
| from_time | Start of time window (defaults to 24 hours ago) (YYYY-MM-DD HH:MM:SS). |
| to_time | End of time window (defaults to current time) (YYYY-MM-DD HH:MM:SS). |
| status | A list of triage statuses for submissions (UNRESOLVED,CONFIRMED,IGNORED); only email submissions marked with at least one of these statuses will be returned. |
Task output
| Field | Description |
|---|---|
| submissionId | The ID of the phishing email submission. |
| title | The subject of the email submission. |
| priorityEventScore | The score of the email submission. |
| status | The current triage status of the email submission. Accepted status options: "CONFIRMED", "IGNORED", or "UNRESOLVED". |
| context | An array of structures containing original and normalized indicators scores for each indicator in the email submission. |
Sample output
| Field | Value |
|---|---|
| context |
{'indicatorType': 'IP', 'indicatorValue': '119.81.93.82', 'sourceKey': 'virustotal', 'normalizedIndicatorScore': 3, 'originalIndicatorScore': {'name': 'Detections', 'value': '54/65'}},
{'indicatorType': 'IP', 'indicatorValue': '124.160.116.194', 'sourceKey': 'virustotal', 'normalizedSourceScore': -1, 'originalIndicatorScore': {'name': 'null', 'value': 'null'} },
{'indicatorType': 'IP', 'indicatorValue': '185.7.215.175', 'sourceKey': 'virustotal', 'normalizedIndicatorScore': -1, 'originalIndicatorScore': {'name': 'null', 'value': 'null'} }
|
| priorityEventScore | 3 |
| status | phishing/unresolved |
| submissionId | 666fae30-ff2d-4bfd-b1c9-27d7611f430a |
| title | Executive Spear Phish |
Get phishing indicators
Purpose: Fetches the Indicators found in phishing emails submitted to the Phishing Triage enclave.
!trustar-get-phishing-indicators
Task input
| Parameter | Description |
|---|---|
| priority_event_score | Score of email submission |
| normalized_indicator_score | Normalized Indicator Score. |
| from_time | Start of time window (defaults to 24 hours ago) (YYYY-MM-DD HH:MM:SS) |
| to_time | End of time window (defaults to current time) (YYYY-MM-DD HH:MM:SS) |
| status | A list of triage statuses for submissions; only email submissions marked with at least one of these statuses will be returned. Options are 'UNRESOLVED', 'CONFIRMED', 'IGNORED' |
Task output
| Field | Description |
|---|---|
| indicatorType | The type of Indicator. Available types are IP, URL, EMAIL_ADDRESS, MD5, SHA1, SHA256. |
| value | The indicator's value. |
| sourceKey | The intelligence source where the indicator originated. |
| normalizedIndicatorScore | The Normalized Score of the Indicator. |
| originalIndicatorScore | The Original Score provided by the external intelligence source for the indicator. |
Original indicator score
The indicator's score, as provided by the intelligence source.
| Field | Type | Description |
|---|---|---|
| name | String | The name of the score type, e.g. "Risk Score" or "Malicious Confidence" |
| value | String | The value of the score, as directly extracted from the source, e.g. "HIGH" or "78" |
Sample output
| Field | Value |
|---|---|
| indicatorType | IP |
| normalizedIndicatorScore | 3 |
| originalIndicatorScore | {'name': 'Detections', 'value': '54/65'} |
| sourceKey | virustotal |
| value | 119.81.93.82 |
Set phishing triage status
Purpose: Sets the status of a phishing email submission with one or more status tags. By default, every submission is tagged with unresolved status. Status tag options are:
- Confirmed: Emails that have been confirmed as phishing emails.
- Ignored: Emails that after review are determined to not be phishing emails
- Unresolved: the default status for all emails
!trustar-set-triage-status
Task input
| Parameter | Description |
|---|---|
| submission_id | ID of the email submission |
| status | Submission status |
Task Output
(200) No Content
Sample Output
OK
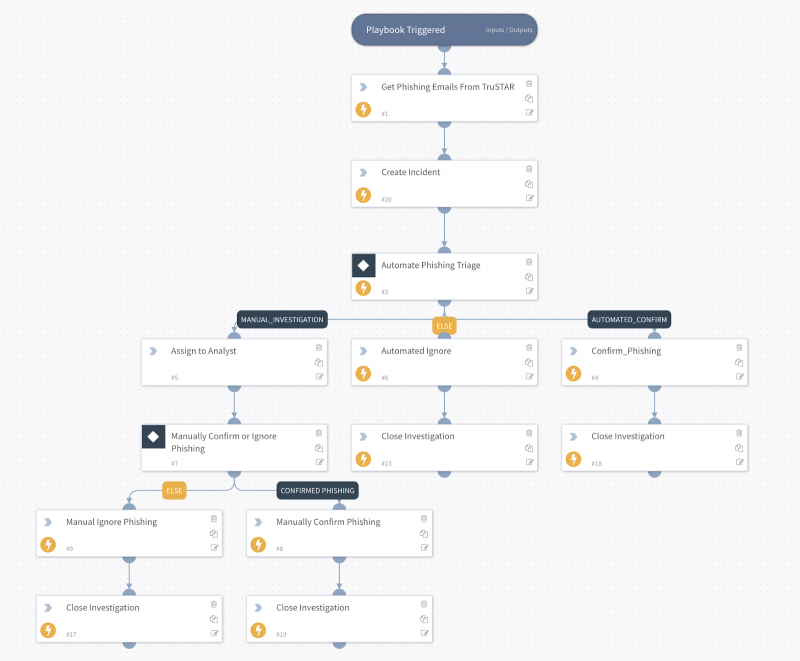
Sample playbook
This sample playbook, combined with Splunk Intelligence Management's ability to automatically move Indicators from confirmed phishing emails to a Phishing Indicator Enclave that is directly connected to a SIEM, provides an end-to-end workflow that reduces your organization's risk exposure from user-reported phishing emails.
As part of the Phishing Triage feature set, the Splunk Intelligence Management team built a sample playbook that performs the following tasks:
- Demisto gets the most recent "unresolved" phishing emails from Splunk Intelligence Management.
- In the playbook, Splunk Intelligence Management implemented a conditional task that triggers the following:
- Priority Event Score = 2 or 3 automatically confirmed as phishing.
- Priority Event Score = 1 assigns a manual task for later review.
- Priority Event score = 0 or -1 is automatically ignored.
- Once the playbook iterates over all collected emails, you would have completed the task of labeling the emails.
| Use the REST API or Python SDK to access scored emails |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
 Download manual
Download manual
Feedback submitted, thanks!