Deep dive: Using ML to identify network traffic anomalies
The goal of this deep dive is to identify periods of time when there is unusual data transfer traffic on your network. Spotting outliers in data transfer traffic data can help identify a multitude of issues ranging from the benign, to performance impacting misconfigurations, to data exfiltration from a malicious actor.
Data sources
You can use the following data sources in this deep dive:
pan:trafficcisco:asaNetFlow
This deep dive uses pan:traffic logs.
Algorithms
For best results, use the DensityFunction algorithm.
As an alternative approach, try stats or the DBSCAN algorithm.
Train the model
Before you begin training the model, do the following things:
- Change the index and source type for your environment if needed.
- You must pick a search window that has enough data to be representative of your environment. Search over 30 days at a minimum for this analytic. The more data the better.
Enter the following search into the search bar of the app you where want the analytic in production:
index=botsv2 sourcetype=pan:traffic | eval src_dest_pair=src."|".dest | bin _time span=5m | stats sum(bytes_in) as bytes_in sum(bytes_out) as bytes_out by _time src_dest_pair | eval HourOfDay=strftime(_time,"%H") | fit DensityFunction bytes_in by HourOfDay as outlier_bytes_in into bytes_in_outlier_detection_model | fit DensityFunction bytes_out by HourOfDay as outlier_bytes_out into bytes_out_outlier_detection_model
This search counts the bytes in and out per source and destination combination over 5 minute time intervals, enriches the data with the hour of day, and then trains two anomaly detection models: one to detect unusual bytes in by the hour of day, and another to detect unusual bytes out by the hour of day.
After you have run this search and are confident that it is generating results, save it as a report. Schedule the report to periodically retrain the models. As a best practice, retrain the models every week. Schedule model training for a time when your Splunk platform instance has low utilization.
Model training with MLTK can use a high volume of resources.
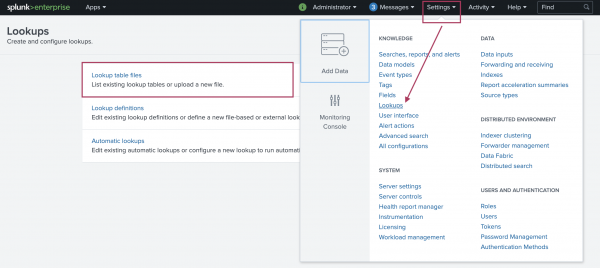
After training the model you can select Settings in the top menu bar, then select Lookups, then select Lookup table files. and search for your trained model.
Make sure that the permissions for the model are correct. By default, models are private to the user who has trained them, but since you have used the app: prefix in your search, the model is visible to all users who have access to the app the model was trained in.
Apply the model
Now that you have set up the model training cycle and have an accessible model, you can start applying the model to data as it is coming into the Splunk platform. Use the following search to apply the model to data:
index=botsv2 sourcetype=pan:traffic | eval src_dest_pair=src."|".dest | bin _time span=5m | stats sum(bytes_in) as bytes_in sum(bytes_out) as bytes_out by _time src_dest_pair | eval HourOfDay=strftime(_time,"%H") | apply bytes_in_outlier_detection_model | apply bytes_out_outlier_detection_model
This search can be used to populate a dashboard panel or can be used to generate an alert.
When looking to flag outliers as alerts, you can append the following to the search:
| eval anomaly_score=outlier_bytes_in+outlier_bytes_out | where anomaly_score>0
This addition filters your results to only show those that have been identified as outliers. An anomaly_score of 2 means that both the bytes in and bytes out count appear unusual, whereas an anomaly_score of 1 means that either the bytes in or bytes out count is out of the expected range.
This search can then be saved as an alert that should trigger when the number of results is greater than 0, which can be run on a scheduled basis such as hourly.
Tune the model
When training and applying your model, you might find that the number of outliers being identified is not proportionate to the data: that the model is either flagging too many or too few outliers. The DensityFunction algorithm has a number of parameters that can be tuned to your data, creating a more manageable set of alerts.
The DensityFunction algorithm has a threshold option that is set at 0.01 by default, which means it will identify the least likely 1% of the data as an outlier. This threshold can be configured as the apply stage, so it can be increased or decreased depending on the tolerance for outliers, as shown in the following search:
index=botsv2 sourcetype=pan:traffic | eval src_dest_pair=src."|".dest | bin _time span=5m | stats sum(bytes_in) as bytes_in sum(bytes_out) as bytes_out by _time src_dest_pair | eval HourOfDay=strftime(_time,"%H") | apply bytes_in_outlier_detection_model threshold=0.005 | apply bytes_out_outlier_detection_model threshold=0.005 | eval anomaly_score=outlier_bytes_in+outlier_bytes_out | where anomaly_score>0
Additional fields can also be extracted and used during the fit and apply stages. For example, if your data has hourly and daily variance, such as significantly more anomalies during working hours on a weekday, you can include the hour of the day and the day of the week in the by clause to more finely tune your model to your data, as shown in the following search:
index=botsv2 sourcetype=pan:traffic | eval src_dest_pair=src."|".dest | bin _time span=5m | stats sum(bytes_in) as bytes_in sum(bytes_out) as bytes_out by _time src_dest_pair | eval HourOfDay=strftime(_time,"%H"), DayOfWeek=strftime(_time,"%a") | fit DensityFunction bytes_in by "HourOfDay,DayOfWeek" as outlier_bytes_in into bytes_in_outlier_detection_model | fit DensityFunction bytes_out by "HourOfDay,DayOfWeek" as outlier_bytes_out into bytes_out_outlier_detection_model
Make sure that all additional fields that are used for training your model are also included in your model apply search.
Learn more
For help using this deep dive, see Troubleshooting the deep dives.
See the following customer use cases from the Splunk .conf archives:
See the following Splunk blog posts on outlier detection:
- Cyclical Statistical Forecasts and Anomalies - Part 1
- Cyclical Statistical Forecasts and Anomalies - Part 4
- Cyclical Statistical Forecasts and Anomalies - Part 5
- Building Machine Learning Models with DensityFunction
- Anomalies Are Like a Gallon of Neapolitan Ice Cream - Part 1
- Anomalies Are Like a Gallon of Neapolitan Ice Cream - Part 2
| Deep dive: Using ML to detect outliers in server response time | Deep dive: Create a data ingest anomaly detection dashboard using ML-SPL commands |
This documentation applies to the following versions of Splunk® Machine Learning Toolkit: 4.5.0, 5.0.0, 5.1.0, 5.2.0, 5.2.1, 5.2.2, 5.3.0, 5.3.1, 5.3.3, 5.4.0, 5.4.1, 5.4.2, 5.5.0, 5.6.0, 5.6.1
 Download manual
Download manual
Feedback submitted, thanks!