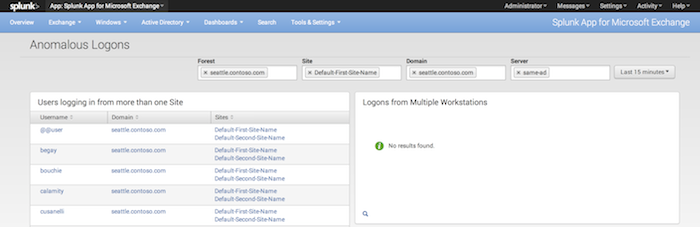
AD Anomalous Logons
The Anomalous Logons page contains information about questionable user activity on your network. It also shows the more sinister attempts to access restricted network resources. Specific statistics displayed here include:
- Users logging on from more than one AD site
- Users logging on from more than one workstation
- Attempts to log on to disabled or expired accounts
How to use this page
- Use the Forest', "Site, Domain, and Server fields to limit results to the forest(s), site(s), domain(s), and user(s) that you want to see.
- To filter using these fields:
- Select a field with your mouse.
- Then, begin typing in the name of an element in the appropriate field. For example, type in the name of a forest in the Forest field. The Splunk App for Microsoft Exchange displays entries for forests it has collected data for. It also updates the page to contain only relevant information that matches the specified forest.
- This method works identically for sites, domains, and users.
- Use the time range picker to limit results to the range of time that you want the app to display.
| Failed Logons | Computer Audit |
This documentation applies to the following versions of Splunk® App for Microsoft Exchange (EOL): 3.4.0
 Download manual
Download manual
Feedback submitted, thanks!