Investigate Splunk UBA entities using Watchlists
You can use Watchlists in Splunk UBA to group entities together for additional analysis or investigation. For example, you discover a small group of individuals associated with a high number of flight risk and data exfiltration anomalies. You can group these users together in a Watchlist so that further anomalies and threats associated with these users are scored appropriately.
It is important to maintain Watchlists to avoid extraneous or irrelevant information. For example, the executive staff may be considered high-risk users as frequent targets of espionage and other malicious behavior, and you can place them on a Watchlist to monitor the activity on their accounts more closely. However, changes in the executive staff, such as an employee being promoted to the executive staff or a current executive leaving the company, must be reflected in the Watchlists. Users and other entities must be individually and manually added to or removed from Watchlists to avoid having outdated information.
Splunk UBA includes several default Watchlists aligned with typical use cases and processes in a security operations center. For example, the default Watchlists provided by Splunk UBA for anomalies conform to the following scenario:
- An anomaly is investigated.
- If it not a legitimate anomaly, put it on the False Positive Watchlist.
- If the anomaly requires further analysis, put it on the Anomaly Watchlist.
- From the Anomaly Watchlist, move certain anomalies to the Important Watchlist for immediate action.
- Once an anomaly is evaluated, put it on the Reviewed Watchlist.
You can create your own Watchlists in Splunk UBA or use any of the included Watchlists. You can assign multiple Watchlists of the same type to any single entity. For example, a user can be on more than one user Watchlists. Adding an entity to a Watchlist in Splunk UBA does not affect any scoring except for the Departing Users, High Risk Users, New Users, and Privileged Users Watchlists. These user Watchlists are considered high risk by default and some threat models use this as a factor in determining the user's score.
Use anomaly action rules to affect the scoring of entities in any Watchlist. You can create a rule for anomalies to automatically be added to a Watchlist when specific conditions are met. Anomaly action rules can also consume other Watchlists such as user Watchlists as a condition. For example, you can write an anomaly action rule to add an anomaly to a Watchlist when there are malware anomalies involving a user on the High Risk user Watchlist.
The following table summarizes the entities that can be placed on a Watchlist, how each entity is added to a Watchlist, and the default watchlists that are included with Splunk UBA:
| Entity | How to add to a Watchlist |
|---|---|
| Anomalies | Use one of the following methods to add anomalies to a Watchlist:
The following anomaly Watchlists are provided by Splunk UBA:
|
| Applications | Add apps one at a time from the Apps Review page. One Watchlist named App Watchlist is provided by Splunk UBA. |
| Devices | Add devices one at a time from the Devices Review or Device Details page. One Watchlist named Device Watchlist is provided by Splunk UBA. |
| Domains | Add domains to a Watchlist by starting with threat details, then viewing any domain page such as Domain Facts, Domain Threats, or Domain Anomalies. One Watchlist named Domain Watchlist is provided by Splunk UBA. |
| Threats | Add threats one at a time from the Threats Review or Threat Details page. The following threat Watchlists are provided by Splunk UBA:
|
| Users | Add users one at a time from the Users Review or User Details page. The following user Watchlists are provided by Splunk UBA:
Splunk UBA considers the Watchlists marked by an asterisk (*) as high risk by default. Being in one of these Watchlists is a factor for some threat models when generating user scores. |
From the Anomalies Table or Anomalies Dashboard pages, you can filter the anomalies you want to see by specifying any combination of Watchlists. For example, you can create a filter to view only anomalies that belong to both a specific anomaly Watchlist and also a domain watchlist.
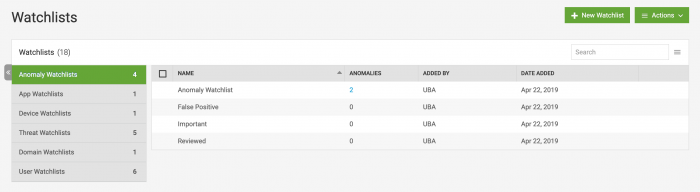
View a summary of the Watchlists in Splunk UBA
You can view a summary of the Watchlists in your Splunk UBA deployment by selecting Manage > Watchlists.
- Create a new Watchlist by selecting the Watchlist type, then clicking New Watchlist. For example, to create a new user watchlist, select User Watchlists and click New Watchlist.
- Delete a Watchlist by selecting the Watchlist you want to delete, then selecting Action > Delete. Splunk UBA's default high-risk user watchlists cannot be deleted.
- Edit the name or description of a Watchlist by hovering over theWatchlist name, then clicking the edit (
 ) icon.
) icon.
To view the contents of a Watchlist, click on the number of entities shown in the table. In this example, we see the number 2 in the Anomalies column for the Anomaly Watchlist. Click on the number 2 to view all of the anomalies in the Anomaly Watchlist.
Example: Use a Watchlist to investigate a group of users for suspected data exfiltration
This example covers the following steps:
- Identify a group of users who are suspected of moving data outside the company and place them on a Watchlist.
- Create a new anomaly action rule so that if any additional anomalies are generated against these users, put the anomaly into an anomaly Watchlist for immediate processing.
Create a new user Watchlist
Perform the following tasks to create a new user Watchlist:
- In Splunk UBA, select Manage > Watchlists.
- In the list of Watchlist types, select User Watchlists.
- Click New Watchlist.
- In the New User Watchlist window, enter the Watchlist name Data Exfiltration.
- Click OK.
Filter users to add to the Watchlist
Next, filter a group of users to add to the new Watchlist.
- In Splunk UBA, select Users on the home page or select Explore > Users.
- Select Add Filter, scroll down and select Anomaly Categories, then select Exfiltration.
- We only want to consider users in the top half of the risk percentile. Select Add Filter, scroll down to and select Anomaly Risk Percentile, then configure the value to be
>= 50.
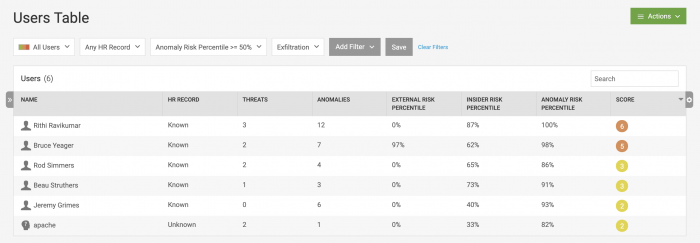
After applying the filters to the users in the system, there are six users who match.
Add each user to the Watchlist
Add each user to the Data Exfiltration Watchlist:
- Click on the first user in the table.
- On the User Facts page, click Watchlists and select Data Exfiltration to add the user to the Data Exfiltration Watchlist.
- Click back in your browser to return to the user table.
- Repeat this procedure until all users are added to the Watchlist.
- On the user table, click the small gear icon on the right side of the table. In the Add/Remove Columns window, scroll down and select User Watchlists.
- Click OK.
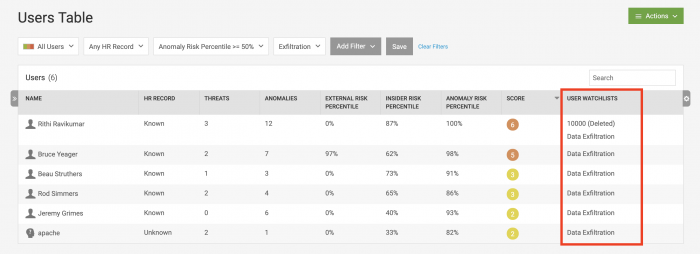
The user table now shows a Watchlists column, with the names of the Watchlists that each user belongs to.
The 10000 (Deleted) notation for the first user means that he was placed on a different Watchlist, but the Watchlist was deleted.
Create an anomaly action rule involving the users in the User Watchlist
Now, create an Anomaly Action Rule so that when additional exfiltration anomalies are generated against these users, the anomalies are placed into the Important Anomaly Watchlist provided by Splunk UBA for immediate attention.
- In Splunk UBA, click Anomalies from the home page or select Explore > Anomalies.
- Click the anomaly rules icon.
- Click New Anomaly Action Rule.
- On the Rule Action page:
- Select Add Anomalies to Watchlist and select Important from the drop-down list in the Rule Action section.
- Select Apply to Future Anomalies in the Rule Scope section.
- Click Next.
- On the Anomaly Filter page:
- In the Anomalies section, select Anomaly Categories then select Exfiltration.
- Int he User section, select User Watchlists, then select Data Exfiltration.
- Click Next.
- On the Rule Properties page, specify Data Exfiltration as the rule name.
- Click OK.
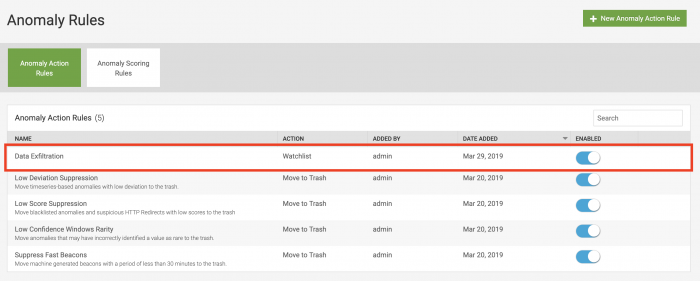
The new rule can be see at the top of the Anomaly Rules page.
Example: VirusTotal Watchlist
Running the VirusTotal script included with Splunk UBA creates a Watchlist containing external IP addresses and domains in Splunk UBA that match VirusTotal.
See, Configure the VirusTotal script to see VirusTotal anomalies in Splunk UBA.
| Create a custom dashboard | Identify data exfiltration by a suspicious user or device |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.1.0, 5.1.0.1
 Download manual
Download manual
Feedback submitted, thanks!