Private Connectivity using AWS PrivateLink 🔗
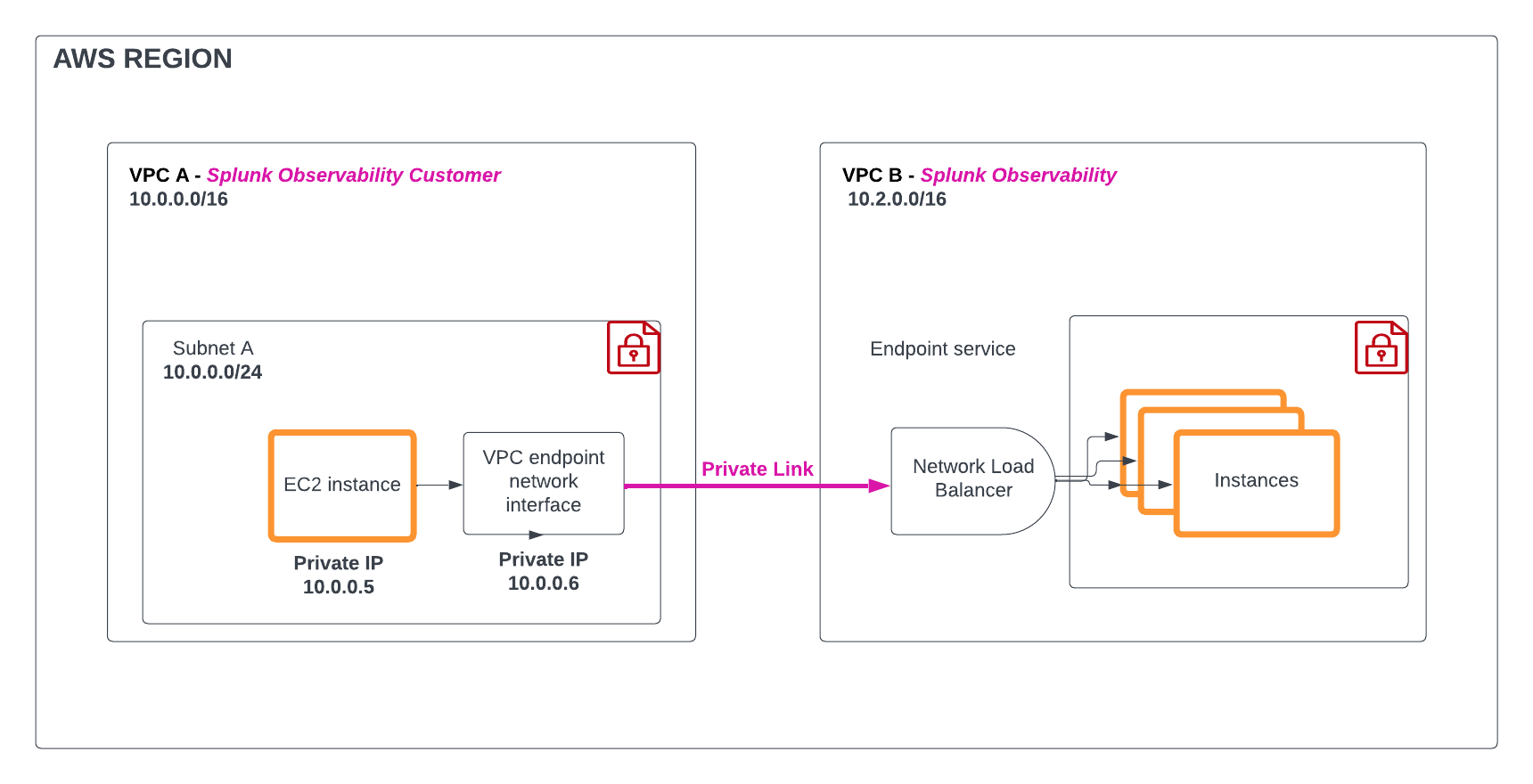
You can use Amazon Web Services (AWS) PrivateLink to secure your metric and traces traffic from your AWS environment to your Splunk Observability Cloud environment without exposing it to the internet.
AWS PrivateLink connects your Virtual Private Cloud (VPC) to your AWS services, treating them as if they were in your VPC. You can create and use VPC endpoints to securely access AWS services and control the specific API endpoints and sites. To learn more, see the AWS PrivateLink documentation at What is AWS PrivateLink? .
Note
To send logs to Splunk Observability Cloud, use Splunk Log Observer Connect.
To send logs securely, use Private connectivity in Splunk Cloud Platform .
The following diagram shows an overview of how AWS PrivateLink for Splunk Observability Cloud works:
Prerequisites 🔗
To connect Splunk Observability Cloud to AWS using AWS PrivateLink, you need the following:
An active AWS account
A basic understanding of VPC concepts and networking principles
AWS PrivateLink types of endpoint 🔗
You can use any of these endpoints with AWS PrivateLink:
Ingest endpoint. Use the Ingest endpoint to send data points directly from your applications to Splunk Observability Cloud. Data sent using the Ingest API is handled in the same manner as data gathered by Splunk Observability Cloud through other methods, such as integrations with AWS cloud services.
API endpoint. Use the API endpoint to allow applications to communicate with each other by sending and receiving data. These endpoints serve as the points of interaction with different components like charts, dashboards, dashboard groups…
Stream endpoint. Use the Stream endpoint for continuous, real-time transmission of observability data such as logs, metrics, or traces. This endpoint is key for monitoring and analyzing system performance, identifying issues quickly, and maintaining overall system health.
AWS PrivateLink availability and service name 🔗
See the following tables for the AWS PrivateLink endpoint URLs and service names for each AWS region.
AWS PrivateLink endpoint URLs 🔗
Splunk Observability Cloud realm |
AWS region |
Ingest endpoint URL |
API endpoint URL |
Backfill endpoint URL |
Stream endpoint URL |
|---|---|---|---|---|---|
jp0 |
AWS AP Tokyo (ap-northeast-1) |
Coming soon |
|||
au0 |
AWS AP Sydney (ap-southeast-2) |
Coming soon |
|||
eu1 |
AWS EU Frankfurt (eu-central-1) |
Coming soon |
|||
eu0 |
AWS EU Dublin (eu-west-1) |
Coming soon |
|||
eu2 |
AWS EU London (eu-west-2) |
Coming soon |
|||
us0 |
AWS US East Virginia (us-east-1) |
Coming soon |
|||
us1 |
AWS US West Oregon (us-west-2) |
Coming soon |
AWS PrivateLink service names 🔗
Splunk Observability Cloud realm |
AWS region |
Ingest endpoint service name |
API endpoint service name |
Backfill endpoint service name |
Stream endpoint service name |
|---|---|---|---|---|---|
jp0 |
AWS AP Tokyo (ap-northeast-1) |
com.amazonaws.vpce.ap-northeast-1.vpce-svc-086c8167a74323e5a |
com.amazonaws.vpce.ap-northeast-1.vpce-svc-06e1951072fcabaaa |
Coming soon |
com.amazonaws.vpce.ap-northeast-1.vpce-svc-0aebd0dfe769cc20b |
au0 |
AWS AP Sydney (ap-southeast-2) |
com.amazonaws.vpce.ap-southeast-2.vpce-svc-01e4e31c294754b6e |
com.amazonaws.vpce.ap-southeast-2.vpce-svc-0d1d69a0b1bf003cd |
Coming soon |
com.amazonaws.vpce.ap-southeast-2.vpce-svc-006a9808c3bf97fc1 |
eu1 |
AWS EU Frankfurt (eu-central-1) |
com.amazonaws.vpce.eu-central-1.vpce-svc-0163ebbf011db95fa |
com.amazonaws.vpce.eu-central-1.vpce-svc-063722bf4a2e858a3 |
Coming soon |
com.amazonaws.vpce.eu-central-1.vpce-svc-022080c55adaeac78 |
eu0 |
AWS EU Dublin (eu-west-1) |
com.amazonaws.vpce.eu-west-1.vpce-svc-01c194b2265ecb86e |
com.amazonaws.vpce.eu-west-1.vpce-svc-07b08296ff84e17a0 |
Coming soon |
com.amazonaws.vpce.eu-west-1.vpce-svc-0d036df6dbc6ddadb |
eu2 |
AWS EU London (eu-west-2) |
com.amazonaws.vpce.eu-west-2.vpce-svc-0f7427a7b9ef925b0 |
com.amazonaws.vpce.eu-west-2.vpce-svc-0719f35de75c08514 |
Coming soon |
com.amazonaws.vpce.eu-west-2.vpce-svc-0bc5b13127f2916ce |
us0 |
AWS US East Virginia (us-east-1) |
com.amazonaws.vpce.us-east-1.vpce-svc-0336437d577075951 |
com.amazonaws.vpce.us-east-1.vpce-svc-089b68950f5be1c22 |
Coming soon |
com.amazonaws.vpce.us-east-1.vpce-svc-0c7d803ea7ebe3157 |
us1 |
AWS US West Oregon (us-west-2) |
com.amazonaws.vpce.us-west-2.vpce-svc-06376c4a9be288ee9 |
com.amazonaws.vpce.us-west-2.vpce-svc-0da2bbb45fa4c3a6b |
Coming soon |
com.amazonaws.vpce.us-west-2.vpce-svc-0d78b8dec1a837389 |
Configure your AWS PrivateLink VPC endpoints 🔗
Follow these steps to create, use, and manage your AWS PrivateLink VPC endpoint:
Step 1: Request to add your AWS Account ID to the allow list 🔗
Reach out to Splunk Customer Support with the following information to include your AWS Account ID to the allow list:
AWS Account ID
AWS region
Endpoint type
Ingest
API
Stream
Review the ways you can contact Splunk Customer Support at Splunk Observability Cloud support.
Step 2: Verify AWS Account ID is added to allow list 🔗
Caution
Wait for Splunk Customer Support’s confirmation that your AWS Account ID was added to the allow list before performing these steps. Support might take up to 24 hours.
To verify your AWS Account ID has been allowed, follow these steps:
Log in to the AWS Management Console, and open the Amazon VPC service in the specific region where you intend to set up AWS PrivateLink.
On the left navigation pane, select Endpoints.
Select Endpoint, and then Other endpoint services.
Enter and verify the service name based on the AWS region where you’re configuring the VPC endpoint. Identify the appropriate service name using the AWS PrivateLink service names table.
If you see the “Service name verified” message, proceed with Step 3: Create a VPC endpoint.
If you see the “Service name could not be verified” error message, your account ID is not yet allowed for the given service name. Reach out to Splunk Customer Support to check the status of your request from Step 1: Request to add your AWS Account ID to the allow list.
Step 3: Create a VPC endpoint 🔗
To create a VPC endpoint, follow these steps:
Log in to the AWS Management Console, and open Amazon VPC service within the specific region where you intend to set up AWS PrivateLink. If you have a VPC peering configuration, keep in mind the destination region of VPC peering.
On the left navigation pane, select Endpoints.
Select Create Endpoint, and then Other endpoint services.
Enter and verify the service name based on the AWS region where you’re configuring the VPC endpoint. Identify the appropriate service name using the AWS PrivateLink service names table.
Select the VPC in which you want to create the endpoint.
Select the subnet or subnets within the VPC where the endpoint will reside. Make sure to select the subnets from the appropriate availability zones.
Set the IP address type to
IPv4.Specify the security group controlling traffic for the endpoint. Set the outbound rule to HTTPS protocol and the
443port.
Review the configuration details and select Create Endpoint.
Before proceeding to Step 4: Modify the endpoint to activate a Private DNS Name, confirm with Splunk Customer Support that you created the endpoint, that the service name has been verified, and that Support has activated the endpoint urls.
Step 4: Modify the endpoint to activate a Private DNS Name 🔗
To modify the endpoint to activate a Private DNS Name, follow these steps:
Log in to the AWS Management Console.
Navigate to the Amazon VPC service in the region where you have created the VPC endpoint.
On the left navigation pane, select Endpoints.
Select the VPC endpoint you want to modify.
Select Actions, and then Modify Endpoint.
Turn on the private DNS names under the Modify private DNS name settings.
After the process is completed, select Save Changes.
You can now start using the AWS PrivateLink URL mentioned in the AWS PrivateLink endpoint URLs table.
Delete a VPC endpoint 🔗
You can list, modify, tag, or delete your VPC endpoints.
To delete an endpoint, follow these steps:
Log in to the AWS Management Console and open the Amazon VPC service.
On the left navigation pane, select Endpoints.
Select the VPC endpoint you want to delete.
Confirm the deletion when prompted.
Advanced configuration 🔗
Use AWS PrivateLink with the Collector 🔗
To use AWS PrivateLink URLs in your Collector instance, update the necessary variables in your Collector configuration to point to the given endpoint type:
Endpoint type |
Endpoint URL |
Example |
|---|---|---|
Metric ingest endpoint |
|
|
Traces ingest endpoint |
|
|
API endpoint URL |
|
|
See all PrivateLink URLs at AWS PrivateLink endpoint URLs.
For information about the Collector’s environment variables see Environment variables.
Use AWS PrivateLink with VPC peering 🔗
Examine a scenario where the workloads that you’re monitoring with Splunk Observability Cloud are in the AWS ap-south-1 region, and your Splunk Observability Cloud account is in us-east-1. You want to use PrivateLink to ingest observability data, but PrivateLink only works within one AWS region.
In this scenario, carry out the following steps:
Ensure that you have a VPC set up in the destination region, in this example
us-east-1. If you don’t have a VPC in that region, create a new one.Use AWS VPC peering to peer the
ap-south-1and theus-east-1VPCs together.Activate AWS PrivateLink in the
us-east-1VPC.
Learn more about VPC Peering in the AWS documentation at Two VPCs peered together .
Report an issue 🔗
Before you create an issue or open a Splunk Customer Support request, gather the following information:
What happened and the impact of the issue.
All the steps you followed until the issue appeared.
What you expected as the outcome.
Your attempts to solve the issue, including workarounds.
The operating system, runtime or compiler version, libraries, frameworks, and application servers of your environment, including your instrumentation settings.
Debug logs and other logs that might help troubleshoot the issue.
To get help, see Splunk Observability Cloud support.