Splunk Cloud Platform IL5
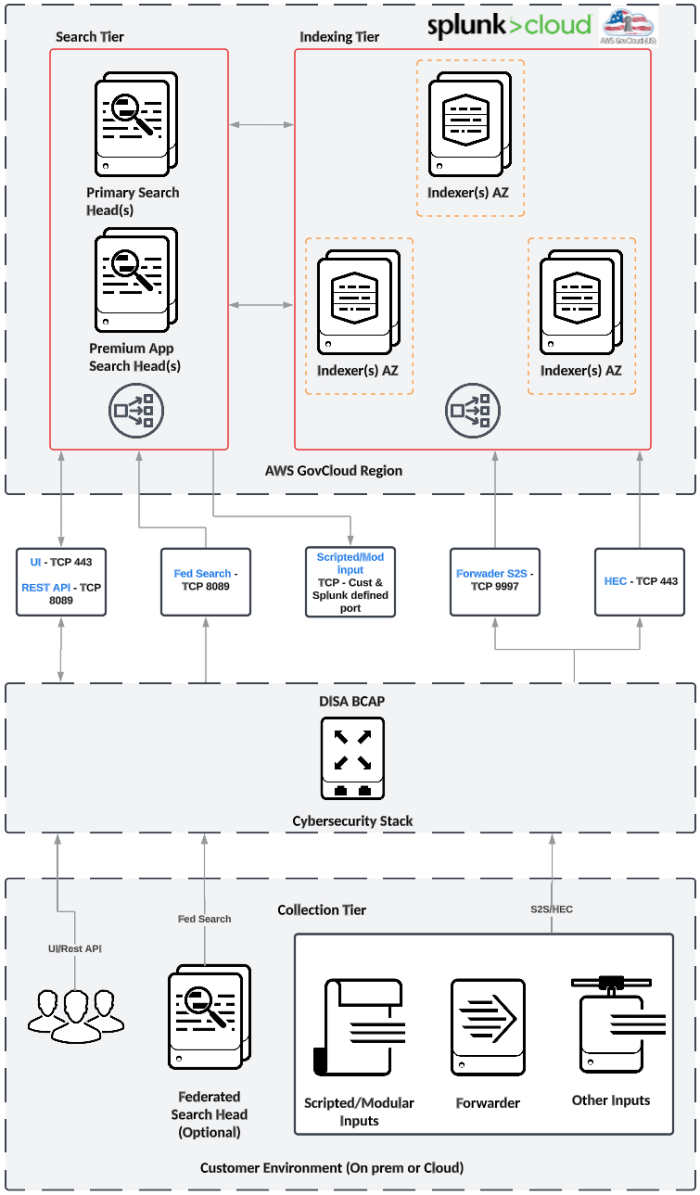
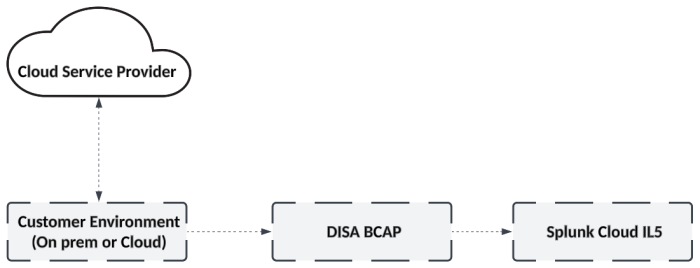
The following diagram represents the high-level architecture of a Splunk Cloud Platform IL5 deployment and shows the
integration points between the Splunk Cloud Platform IL5 environment, DISA, and the customer's environment:
Experience designation
Splunk Cloud Platform IL5 environments are deployed in the Classic Experience.
For information on the differing capabilities and service limits of each Splunk Cloud Platform Experience, see Differences between Classic Experience in Splunk Cloud Platform Admin Manual and Victoria Experience and Experience designations in Splunk Cloud Platform Service Description.
Limitations
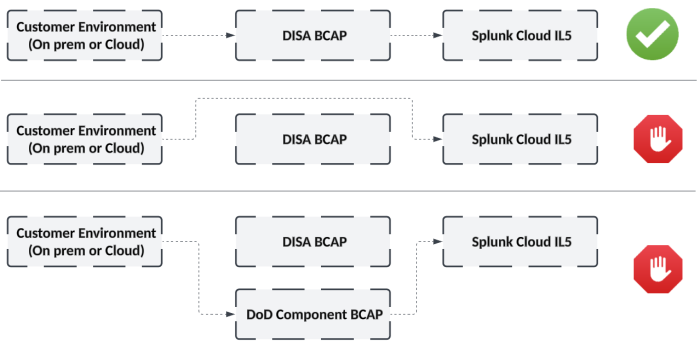
DISA BCAP routing required
Splunk's P-ATO was issued based on the architecture sending all customer traffic through the DISA BCAP. DoD components other than DISA are able to establish BCAPs, but the Splunk IL5 Platform requires use of DISA's BCAP specifically. Other component BCAPs are not able to route directly to the Splunk Cloud Platform IL5 service.
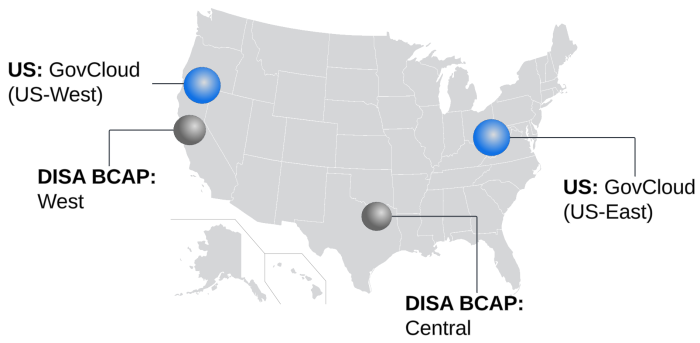
IL5 routing considerations
Splunk Cloud Platform IL5 environments are deployed in AWS GovCloud East or West based on customer selection. An important consideration with regard to region selection and routing is that traffic will always route from a customer's environment across NIPRNet and to one of the DISA BCAPs before reaching the Splunk Cloud Platform IL5 environment. The BCAPs currently used by DISA are located in Central and West.
Customer environment initiated connections
Connections between the customer's environment(s) and Splunk Cloud Platform IL5 must be initiated from the customer environment. Customers are not able to initiate connection from their Splunk Cloud Platform IL5 environment back to their customer environment.
This one-way traffic presents limitations for Splunk functionality that requires or is optimally implemented when traffic can originate from their Splunk Cloud Platform environment to communicate with resources in the customer's infrastructure. Examples of impacted functionality include but are not limited to the following:
- Alert actions
- Enterprise Security (ES) Adaptive Responses
- User Behavior Analytics (UBA)
- Scripted Inputs
- LDAP and SAML Authentication
- Federated Search from Splunk Cloud Platform to Splunk Enterprise
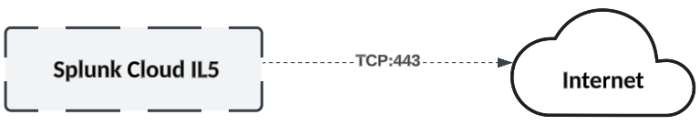
Internet based resources
Splunk Cloud Platform IL5 platform has limited outbound connectivity to the Internet on port 443. Outbound Internet connections support platform features such as access to Splunkbase for application installation and updates and updates for Threat Intelligence feeds. Data collection from Internet based sources may be possible in some cases via add-ons installed on the Inputs Data Manager (IDM). However, data collection from Cloud Service Providers and other SaaS vendors through customer managed collection tier infrastructure may be necessary and is recommended.
Customer environment data collection tier
Customers with requirements to collect data from Cloud Service Providers or other SaaS products may collect and forward data from those sources through a collection tier in their customer environment before sending to Splunk Cloud Platform IL5. Collecting and forwarding data from sources though existing customer environments enables customers to use established communication channels to collect and forward data.
Email delivery
Email delivery from Splunk Cloud Platform IL5 is not available. Splunk Cloud Platform uses third party email services to facilitate email delivery, and the third party service used in our commercial and FedRAMP offerings is not available in IL5.
Communication considerations
Splunk Cloud Platform IL5 customers are responsible for managing IP allow lists for their environments. The primary IP allow list management points associated with the solution are at the DISA BCAP and at the Splunk Cloud Platform IL5 itself. Customers may have other network devices as part of their infrastructure that require configuration in order to facilitate connectivity to Splunk Cloud Platform IL5, but those are outside the scope of this guidance.
Data traversing the DISA BCAP is regulated by DISA managed network devices upstream from Splunk management. As part of the initial ATO process with DISA, customers are responsible for documenting approved source and destination IP addresses. Customers are also responsible for maintaining the allow lists for the duration of environment operation.
Downstream of the DISA BCAP, IP allow lists are used to control access at the Splunk Cloud Platform IL5. By default the IP allow lists do not allow any traffic to reach the Splunk Cloud Platform IL5 environment. In Splunk Cloud Platform iL5, administrators manage IP allow lists by submitting support tickets to Splunk. See Determine IP allow list use case in the Splunk Cloud Platform Admin Config Service Manual for a list of features that require IP allow list configuration in Splunk Cloud Platform. Self-service configuration of IP allow lists at the Splunk Cloud Platform IL5 is not supported.
Evaluation of pillars
| Design principles / best practices | Pillars
| |||||
|---|---|---|---|---|---|---|
| Availability | Performance | Scalability | Security | Management | ||
| #1 | IL5 networking | True | True | |||
| Splunk Cloud Platform Experiences | Customer managed centralized SOC architectures |
This documentation applies to the following versions of Splunk® Validated Architectures: current

 Download manual
Download manual
Feedback submitted, thanks!