Splunk Cloud Platform Experiences
Initial publication: June 8, 2023
Last reviewed: April 25, 2025
Your Splunk Cloud Platform deployment has one of two Experience designations: Classic or Victoria. In the medium term, all customers will move to the Victoria Experience. Refer to the Splunk Cloud Platform Service Description to check region availability for each experience.
Victoria Experience and Classic Experience provide nearly identical capabilities and service limits, with some exceptions.
For information on the differing capabilities and service limits of each Splunk Cloud Platform Experience, see Determine your Splunk Cloud Platform Experience in the Splunk Cloud Platform Admin Manual.
Architecture diagram
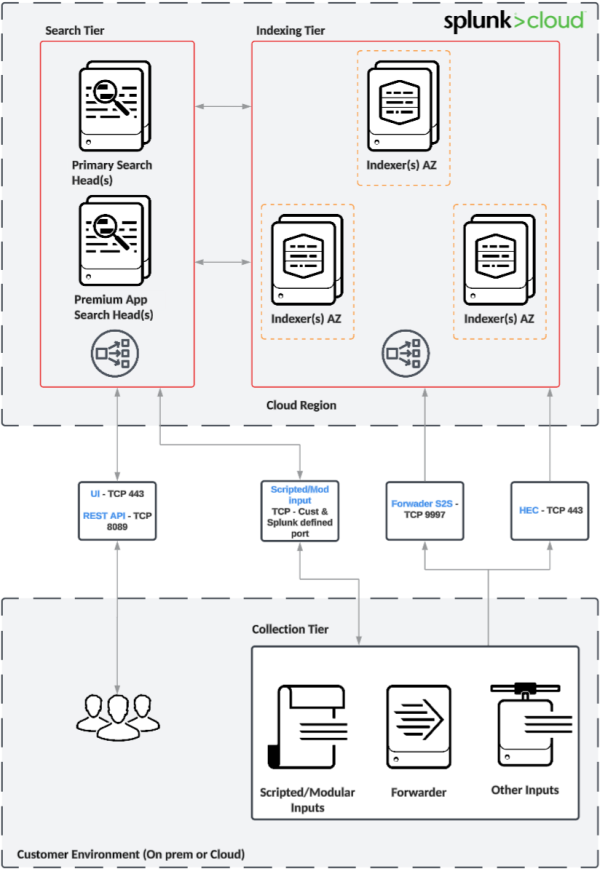
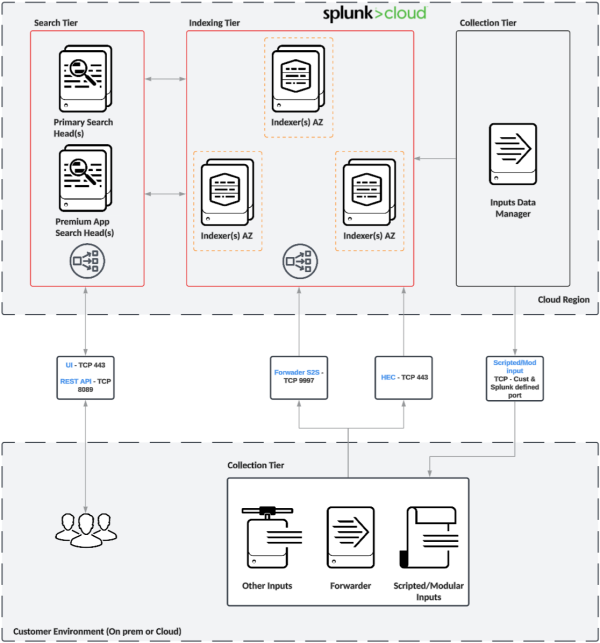
The following diagrams represent the high-level architecture of a Splunk Cloud Platform deployment and show the integration points with your environment.
Splunk Cloud Platform with Victoria Experience
Splunk Cloud Platform with Classic experience
Architecture description and benefits
When you choose Splunk Cloud Platform, all deployments are based on a standardized architecture for all customers in the same region. The Splunk Cloud Platform team builds and operates your dedicated (single-tenant) AWS, Azure, or Google Cloud Platform environment to ensure that the service is compliant and resilient. Victoria experience is not currently available for Google Cloud Platform.
As shown in the architecture diagrams in this document, the standard Splunk Cloud Platform deployment presents the following main components or characteristics:
- Indexers spread across three different availability zones (in a single region) to help ensure high availability.
- Single Search Head (SH) or a Search Head Cluster (SHC), depending on your licensed capacity. SHC instances are also spread across different availability zones and are fronted by a load balancer so users can use a single endpoint for UI access.
- Additional SH for Premium Apps (Enterprise Security (ES) and IT Service Intelligence (ITSI)). SHC is available for ES in Victoria Experience only.
- Data ingestion using Splunk to Splunk (S2S) on the standard TCP port (9997) and using HTTP Event collector (HEC) on port 443.
- Data collection for modular and scripted inputs.
- Configured directly in the Search Head tier for Victoria Experience.
- Configured on Inputs Data Manager (IDM) for Classic Experience.
- Data distribution is accomplished through client and/or server side load balancing where appropriate.
- Access rules are defined in the network layer to allow or deny inbound and outbound connections for both Search Head and Indexer tiers.
- All data in transit is encrypted by default.
When you have access to your Splunk Cloud Platform instance and are ready to start onboarding data, there are still some decisions you need to make to help ensure your environment is secure and performant.
The following sections describe customer-specific configurations that allow you to tailor your environment for your needs. Refer to the section "Splunk Cloud Platform: Shared Responsibility Model" in the Splunk Cloud Platform Service Description for more details.
Networking/Security
- Splunk Cloud Platform endpoints are protected using firewall rules and customers can specify additional access control rules using their IP allow list. See Configure IP allow lists for Splunk Cloud Platform in the Admin Config Service Manual.
- Private connectivity may be implemented to secure your ingest data from traversing over the public internet. See About private connectivity in Securing Splunk Cloud Platform.
Consider the need for encryption at rest.
- Splunk Cloud Platform offers data encryption as a premium service enhancement that customers can purchase. The keys are managed by Splunk. Regulated subscriptions (DoD IL5, FedRAMP moderate, HIPAA, IRAP and PCI) have encryption at rest enabled by default.
- Enterprise Managed Encryption Keys (EMEK) is also available for customers that require to manage their own keys. See Secure data with Enterprise Managed Encryption Keys in Securing Splunk Cloud Platform.
Storage
- The following are the types of storage available in a Splunk Cloud Platform subscription:
- Dynamic Data Active Searchable (DDAS) is used for searching ingested data. DDAS is also commonly known as searchable storage.
- Dynamic Data Active Archive (DDAA) is used as a long term storage and data in DDAA can be restored to DDAS to be searched.
- Dynamic Data Self-Storage (DDSS) may be used to export aged ingested data to support CSP object storage before it is deleted from an index.
Limitations
- For general service limits and constraints, see Service limits and constraints in Splunk Cloud Platform Service Description. For specific limits for Victoria Experience and Classic Experience, see Experience designations in the same document.
- To learn about differences between Splunk Cloud Platform and Splunk Enterprise, see Differences between Splunk Cloud Platform and Splunk Enterprise in Splunk Cloud Platform Service Description.
- Ports for API/Management (8089) and for getting data in (9997 S2S, and 443 HEC) cannot be changed.
- Splunk Cloud Platform does not allow the standard Splunk Enterprise CLI access. Any supported task that requires standard CLI access is performed by the self-service capabilities of Splunk (either using the Splunk Web interface or ACS) or by filing a service ticket.
- Splunk Cloud Platform does not manage or monitor your customer-managed Splunk software components such as Deployment Servers or Universal Forwarders.
| Getting AWS data into the Splunk platform | Splunk Cloud Platform IL5 |
This documentation applies to the following versions of Splunk® Validated Architectures: current
 Download manual
Download manual
Feedback submitted, thanks!