Configure Active Directory Federation Services Single Sign-On for Splunk On-Call 🔗
Requirements 🔗
This integration is compatible with the following versions of Splunk On-Call:
Full-Stack
To enable single sign-on (SSO) for your organization, you will need to provide an updated metadata file and your IDP. If you are interested in setting up SSO, please contact Splunk On-Call Support.
Our standard SSO setup uses SAML 2.0 protocol. As long as your IDP can use SAML 2.0 protocol, it can integrate with Splunk On-Call. The exact steps differ depending on which IDP you use, but the process typically involves exporting a .XML metadata file and sending it to our Support team. Once you have sent the .xml file, a Splunk On-Call support specialist will complete the setup on the back-end and respond with confirmation.
If your IDP does not have SAML capability, please contact Splunk On-Call Support to explore what alternative options may be available. For details on how to contact Splunk On-Call Support, see Contact Splunk On-Call Support.
Configure SSO for Active Directory Federation Services (ADFS) 🔗
To configure SSO for Splunk On-Call using ADFS complete the following steps.
Once you have sent over your Metadata file and the Splunk On-Call Support team has completed the configuration, you will receive an updated metadata file to complete the configuration on your side.
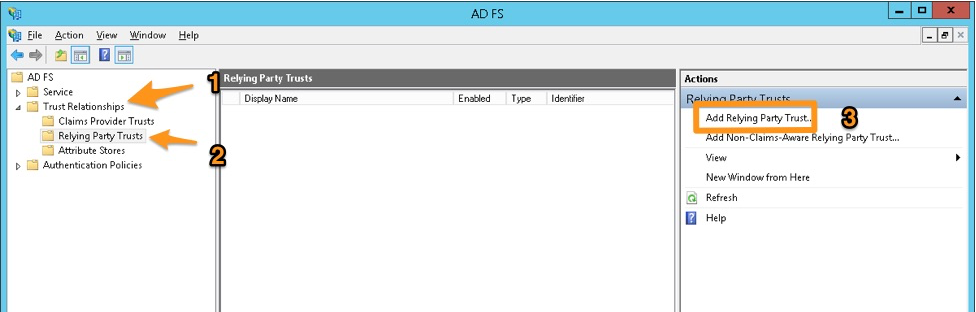
In the ADFS Management console, navigate to Trust Relationships, then Relying Party Trusts and select Add Relying Party Trust in the pane.
Select Start in the Add Relying Party Trust Wizard.
Select Import data about the relying party trust from a file and browse to the metadata.xml provided by Splunk On-Call Support. Select Next.
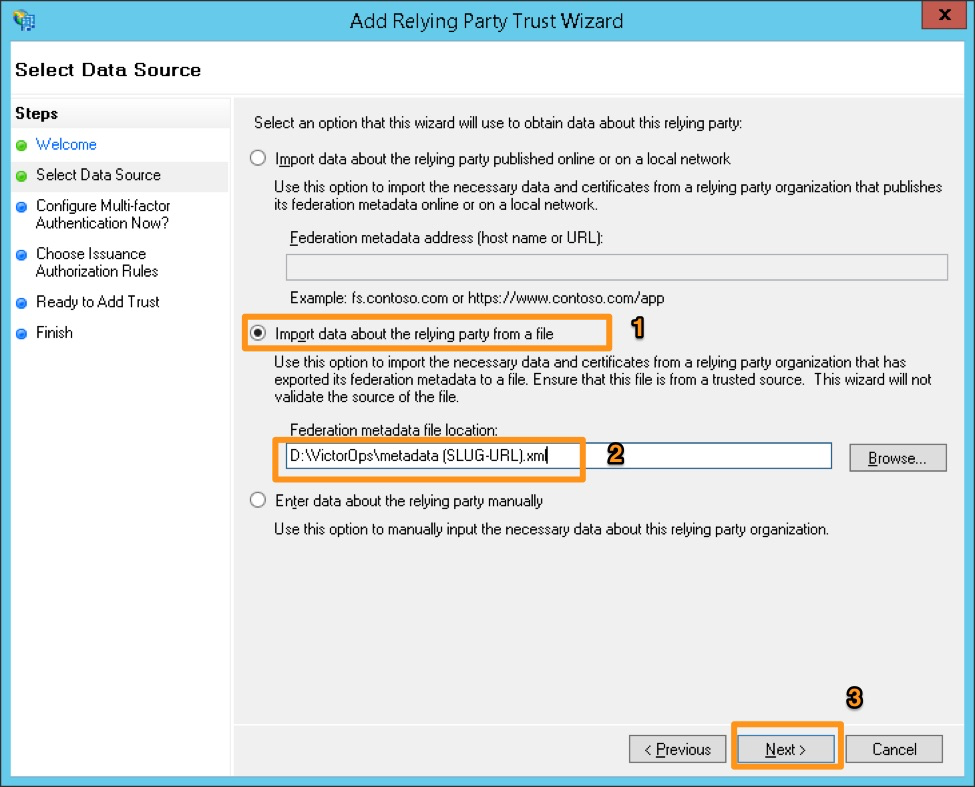
Provide a display name and any notes, and then select Next.
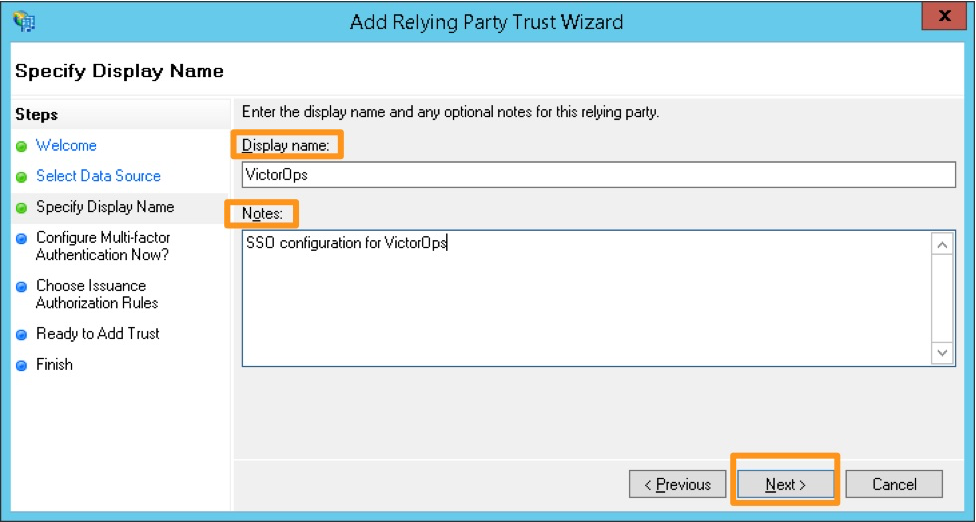
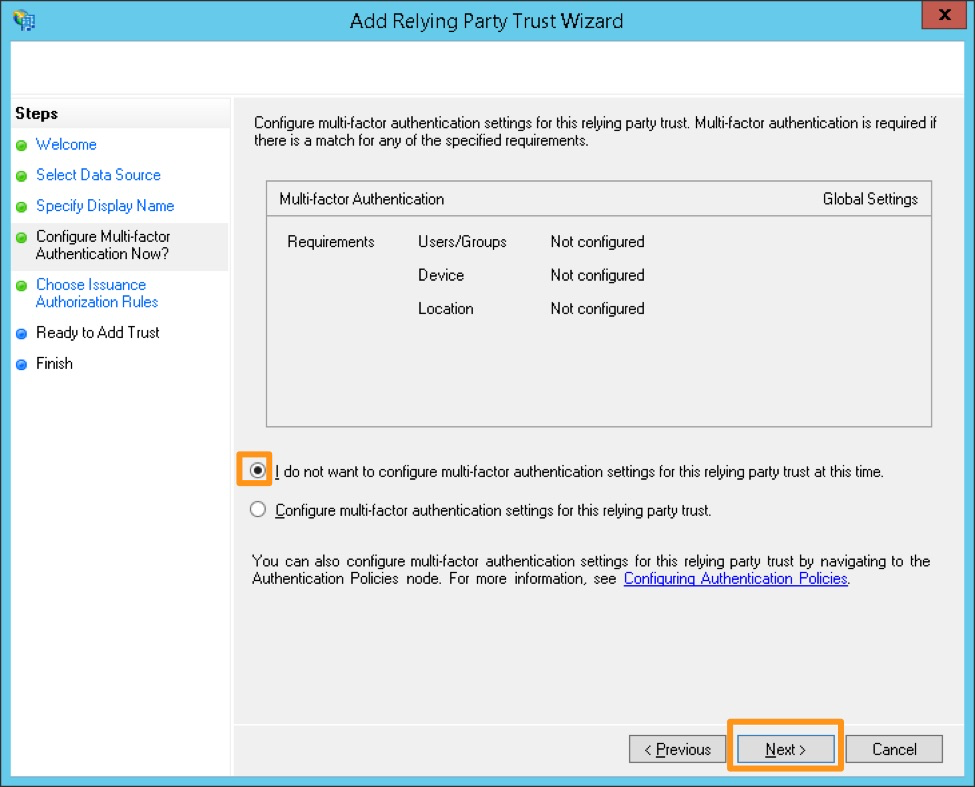
#. Select I do not want to configure multi-factor authentication settings for this relying party trust at this time, and then select Next.
#. (Optionally) Configure multi-factor authentication. This is not necessary for functionality, but may be required for your organization’s security compliance. This step can also be performed later if you need to verify the SAML integration with Splunk On-Call is functioning before bringing the configuration up to compliance.
#. (Optionally) Select Select Deny all users access to this relying party and configure access rules as needed by your organization after completing this configuration.
Review the configuration and select Next if it is accurate. You will not be able to go back from the next screen and will have to manually update the configuration later if there are any changes required.
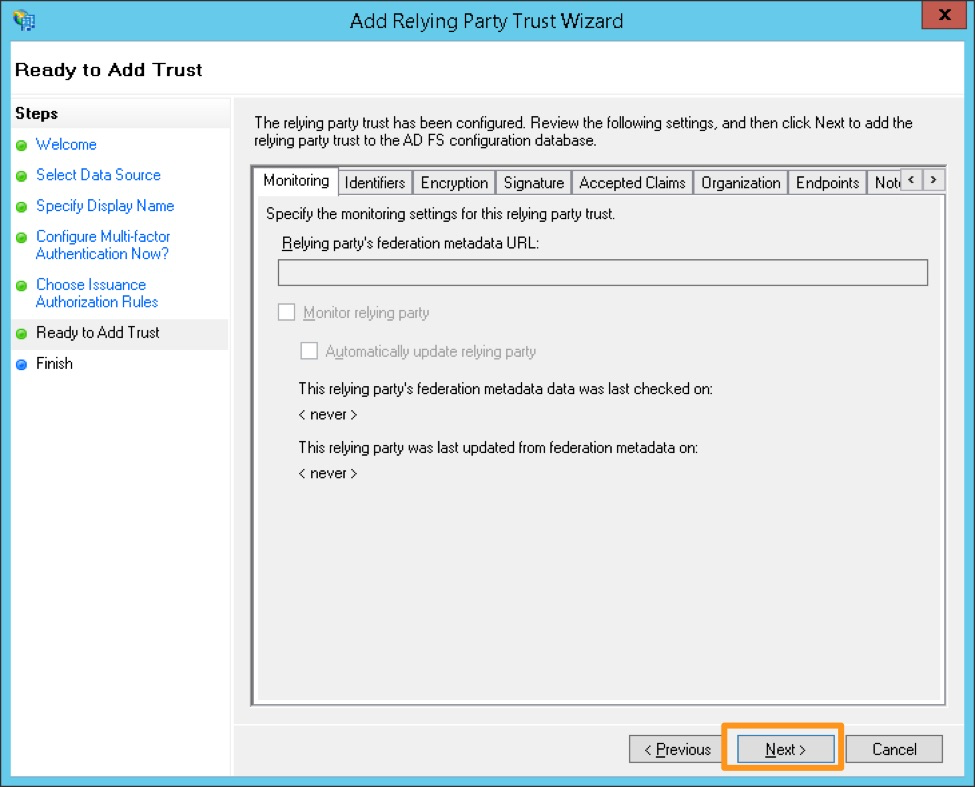
Ensure you select the Open the Edit Claim Rules dialog checkbox, then select Close.
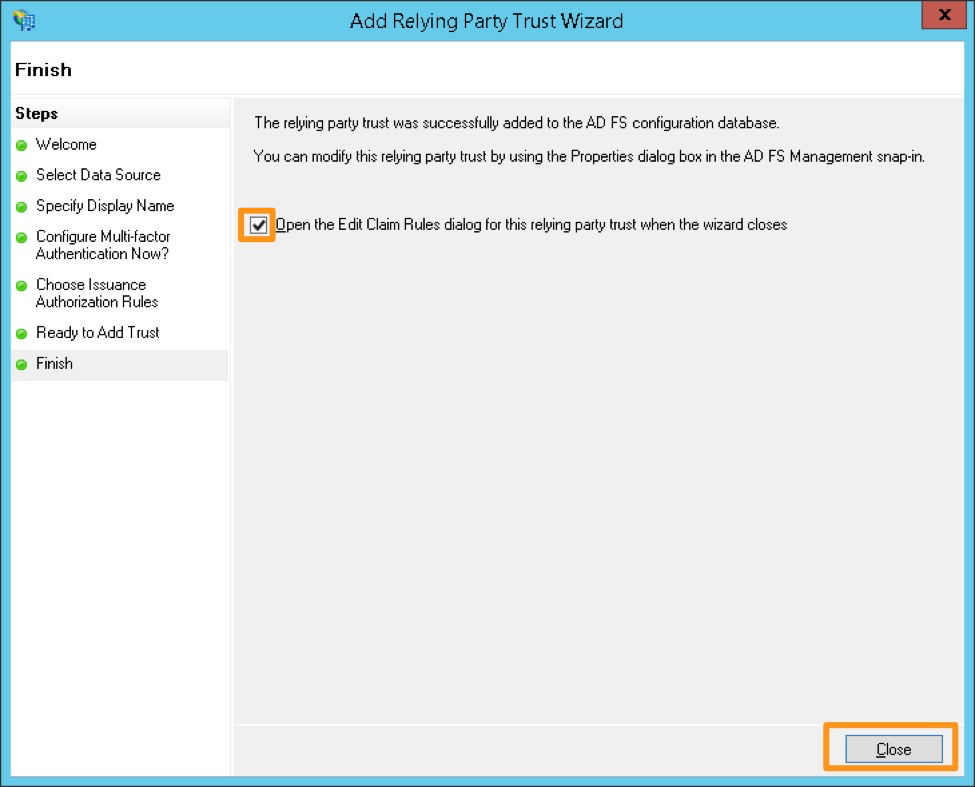
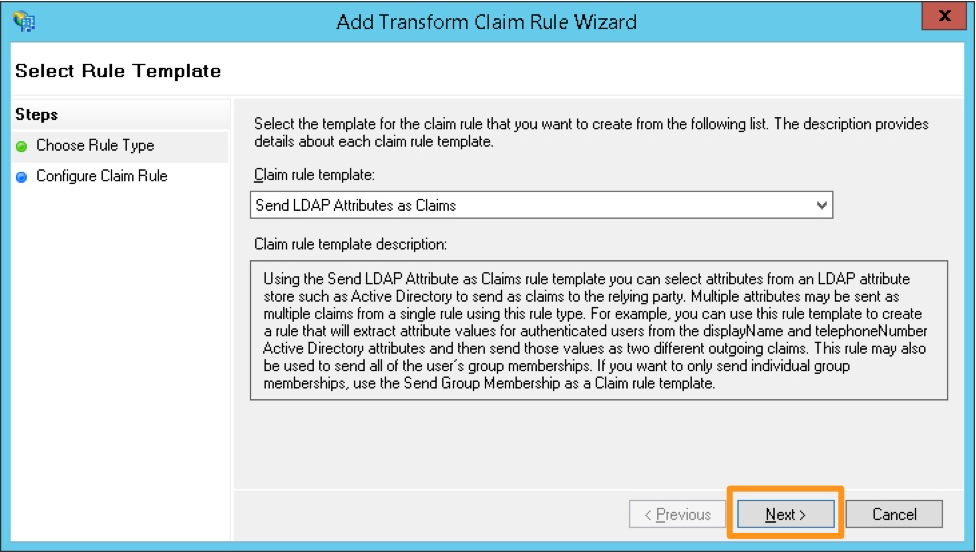
Select Add Rule.
Select the claim rule template Send LDAP Attributes as Claims.
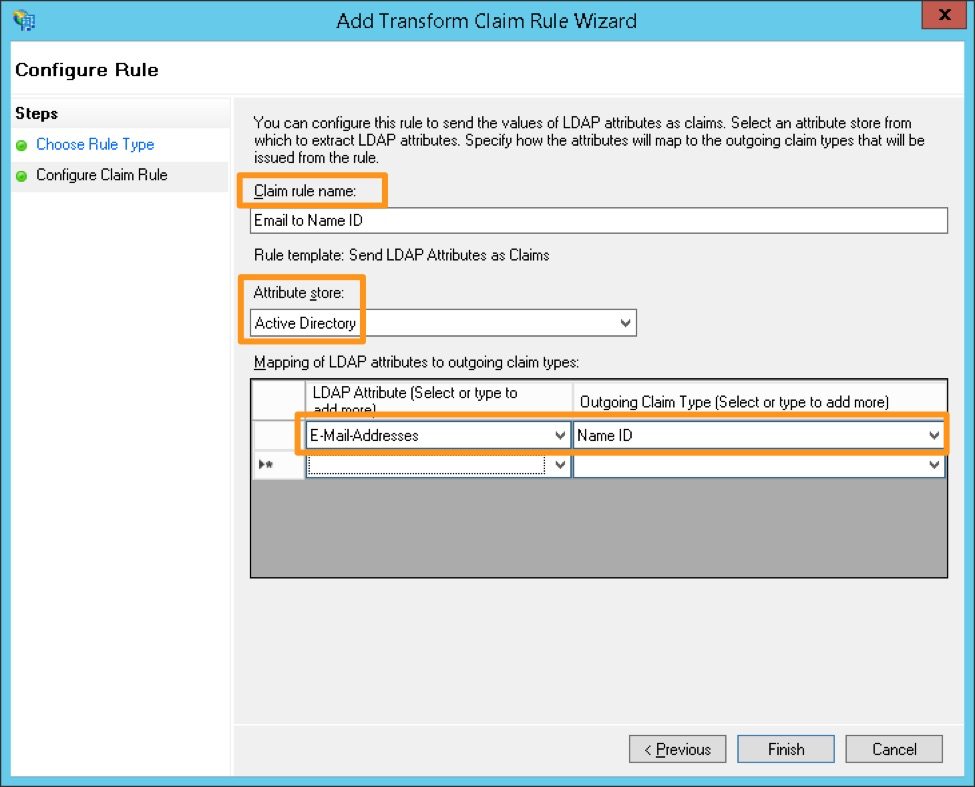
#. Create a name for the rule and select Active Directory as the Attribute store. Under the LDAP Attribute, select E-Mail-Addresses and map it to the Outgoing Claim Type of Name ID, then select Finish.
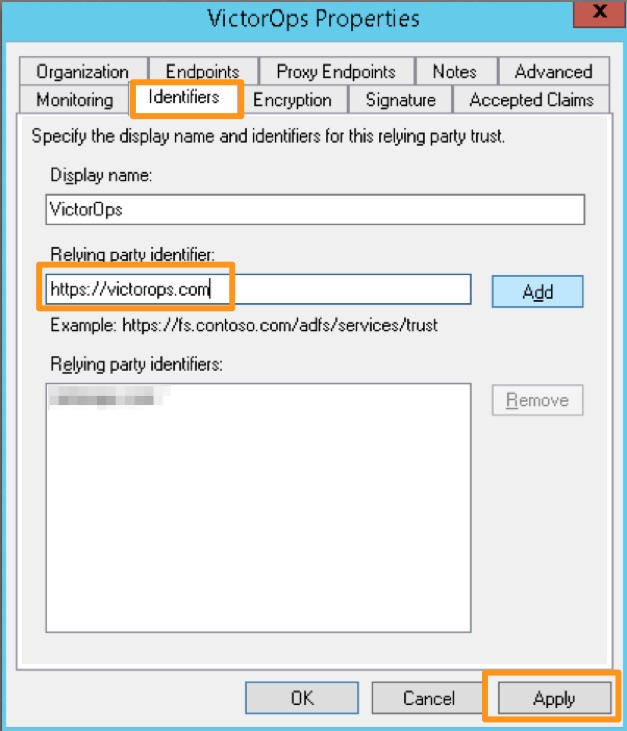
#. Open the Relying Party Trust you just configured for Splunk On-Call by right-clicking the entry and selecting Properties. On the Identifers tab, add https://victorops.com as a Relying party identifier, then select Apply.