Matching conditions for the Rule Engine 🔗
Matching conditions determine when a rule is applied. You can choose any field that exists within the payload of an alert and match on a specific value for that field using a direct match, wildcard matching, or by using a regular expression.
By default, the Rules Engine only uses wildcard matching. If you want to turn on regular expressions, contact Splunk On-Call support.
Requirements 🔗
This integration is compatible with the following versions of Splunk On-Call:
Enterprise
All users have the ability to reach out to Splunk On-Call support at any time with questions.
Live Chat: If you are logged into your Splunk On-Call instance, you will have the ability to Live Chat with the Splunk On-Call Support team.
Field names 🔗
When viewing an incident in the timeline, field names are on the left and values are on the right:
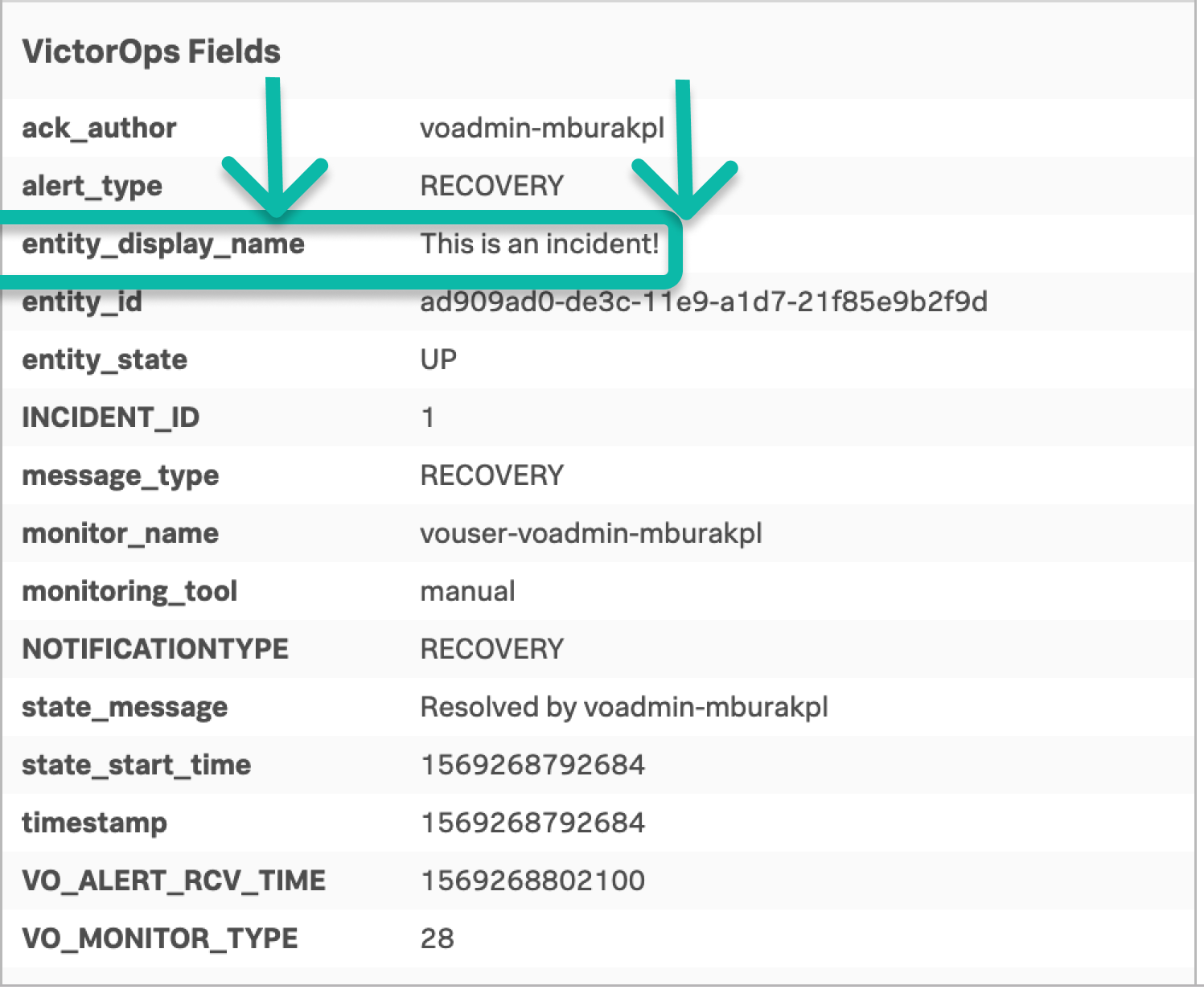
In the previous example, the field of interest is the entity_display_name field and the value that matters is the phrase This is an incident!. The matching condition is the following:

Wildcard matching 🔗
Rules can match an alert field value using a simplified wildcard syntax to match some or all of the string. The asterisk character (*) matches 0 or more characters and you can use it anywhere in the match pattern.
Wildcard examples 🔗
Phrase |
Matches |
Does Not Match |
|---|---|---|
|
|
|
|
|
|
|
|
|
Matching with regular expressions 🔗
Regular expressions are characters that define search patterns. To set a rule to use regular expressions, change the menu option to . If you don’t see the option, contact support to turn on the advanced configuration.
Note
Regular expression rules are subject to timeout and automatic deactivation in the event the crafted expression poses a risk to the stability of your Splunk On-Call instance.
The following limitation apply:
Compatible with Java regular expressions.
Expressions are currently limited to 128 characters.
Add
(?si)to the beginning of your regular expression to match multiline input in a non-case-sensitive way.As the previous technique matches the entire input string, you might need to add
.*at the beginning and at the end of your regular expression.
Regular expression examples 🔗
Phrase |
Matches |
Does Not Match |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
Boolean logic 🔗
You can use disjunction logic (OR) by replicating a rule with a different matching condition.
A set of sequential rules, when ordered correctly, can achieve basic AND logic in the Rules Engine. As with scope limiting rules, the first rule must create a new field which can be acted upon by a subsequent rule.
AND logic example 🔗
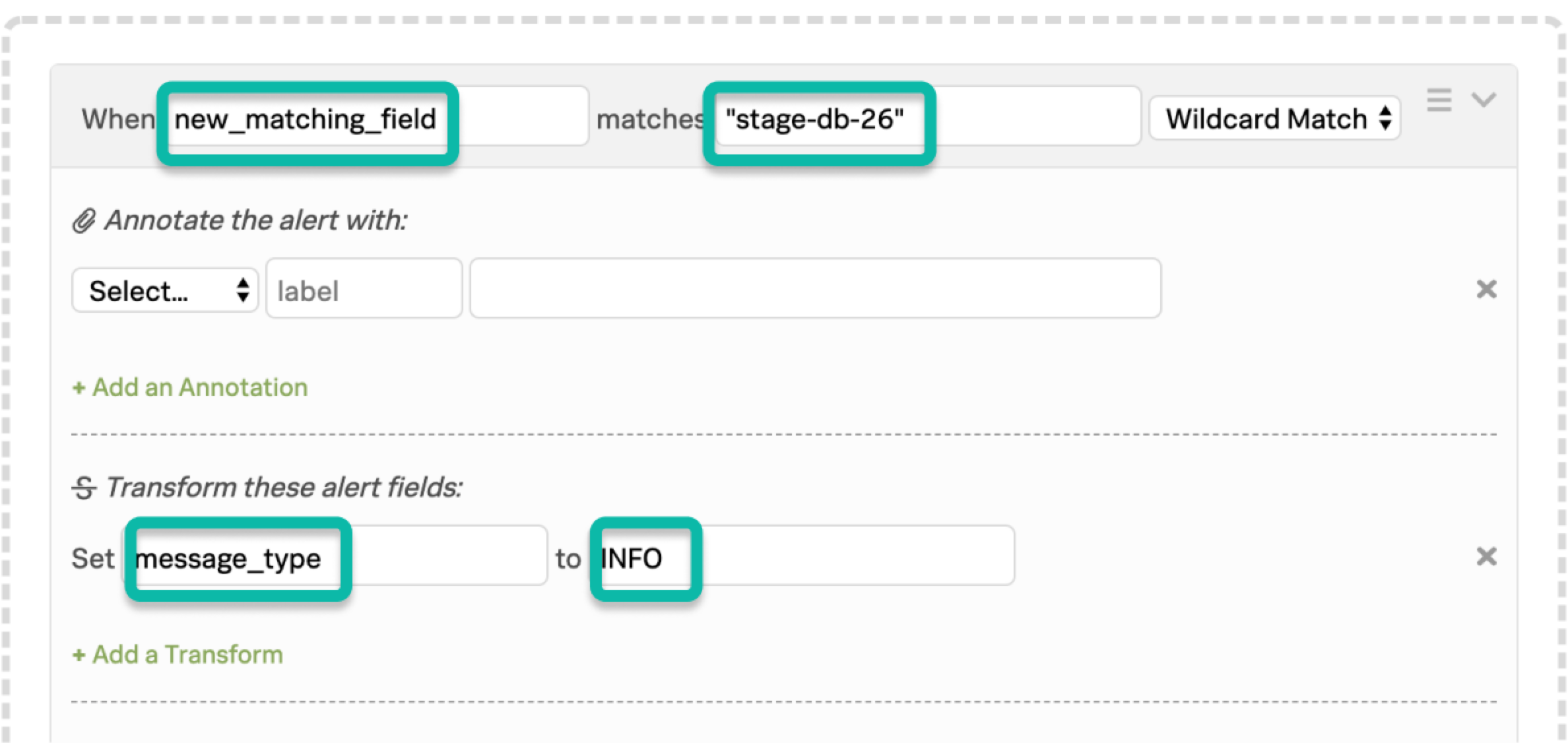
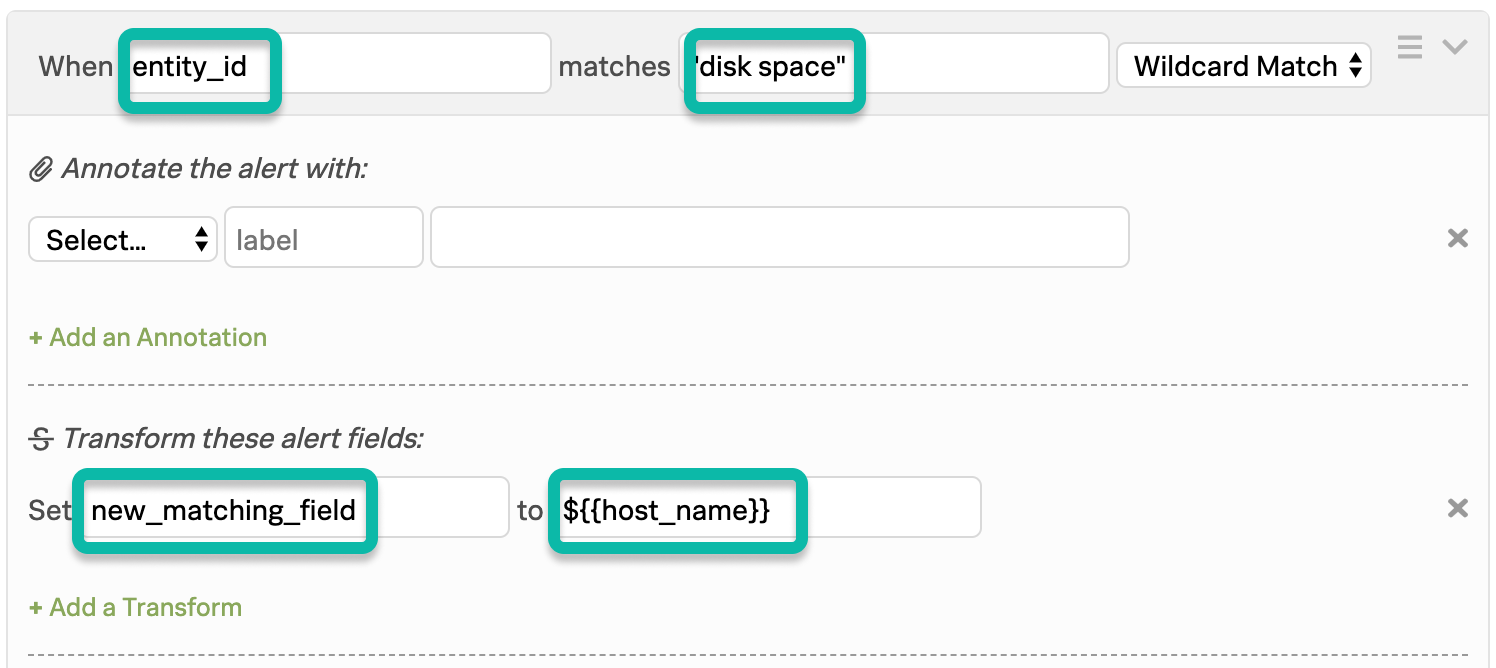
In the following example, you want to capture disk space from the entity_id field, as well as the name stage-db-26 from the host_name field to convert these alerts to INFO events only when both conditions are met.
The matching condition for the first rule catches the first desired phrase and use variable expansion to import the value of the second field into a newly declared field.
The matching condition for the second rule, which you must position below the first rule, checks the newly declared field for the value stage-db-26 and takes the appropriate action.