Set up Log Observer Connect for Splunk Cloud Platform 🔗
Set up Log Observer Connect by integrating Log Observer with Splunk Cloud Platform. If you are in a Splunk Enterprise environment and want to set up Log Observer Connect, see Set up Log Observer Connect for Splunk Enterprise.
When you set up Log Observer Connect, your logs remain in your Splunk Cloud Platform instance and are accessible only to Log Observer Connect. Log Observer Connect does not store or index your logs data. There is no additional charge for Log Observer Connect.
Note
You can collect data using both the Splunk Distribution of the OpenTelemetry Collector and the Universal Forwarder without submitting any duplicated telemetry data. See Use the Splunk Universal Forwarder with the Collector to learn how.
Region and version availability 🔗
Splunk Log Observer Connect is available in the AWS regions us0, us1, eu0, eu1, eu2, jp0, and au0, and in the GCP region us2. Splunk Log Observer Connect is compatible with Splunk Enterprise versions 9.0.1 and higher, and Splunk Cloud Platform versions 9.0.2209 and higher. Log Observer Connect is not available for Splunk Cloud Platform trials.
You cannot access logs from a GovCloud environment through Log Observer Connect. However, you can use global data links to link from Log Observer Connect to your GovCloud environment where you can access your logs. For more information on global data links, see Link metadata to related resources using global data links.
Prerequisites 🔗
To configure the Splunk Cloud service account user in the following section you must have the sc_admin role.
Ensure the following configuration in your Splunk Cloud instance:
Token authentication is enabled for your Log Observer Connect service account in your Splunk Cloud Platform instance. See Securing Splunk Cloud Platform: Enable or disable token authentication token to learn how.
Allow these IPs for Search Head API in IP allow list settings. See https://docs.splunk.com/Documentation/SplunkCloud/9.1.2312/Admin/ConfigureIPAllowList.
us0:
34.199.200.84,52.20.177.252,52.201.67.203,54.89.1.85us1:
44.230.152.35,44.231.27.66,44.225.234.52,44.230.82.104eu0:
108.128.26.145,34.250.243.212,54.171.237.247eu1:
3.73.240.7,18.196.129.64,3.126.181.171eu2:
13.41.86.83,52.56.124.93,35.177.204.133jp0:
35.78.47.79,35.77.252.198,35.75.200.181au0:
13.54.193.47,13.55.9.109,54.153.190.59us2 (for GCP):
35.247.113.38/32,35.247.32.72/32,35.247.86.219/32
Set up Log Observer Connect 🔗
To set up Log Observer Connect for Splunk Cloud Platform without help from the Support team, follow these steps:
Splunk Observability Cloud 🔗
In Splunk Observability Cloud, do the following:
Go to Settings then Log Observer Connect and select Add new connection. If you don’t see Log Observer Connect in Settings, you are not an administrator in Splunk Observability Cloud. Contact your organization’s Splunk Observability Cloud administrator to perform this integration.
Select Splunk Cloud Platform. Next, log in to Splunk Cloud Platform as an administrator and follow the instructions in the next section.
Splunk Cloud Platform 🔗
To configure the Splunk Cloud service account user in the following section you must have the sc_admin role.
In Splunk Cloud Platform, follow the instructions in the guided setup for the integration to do the following:
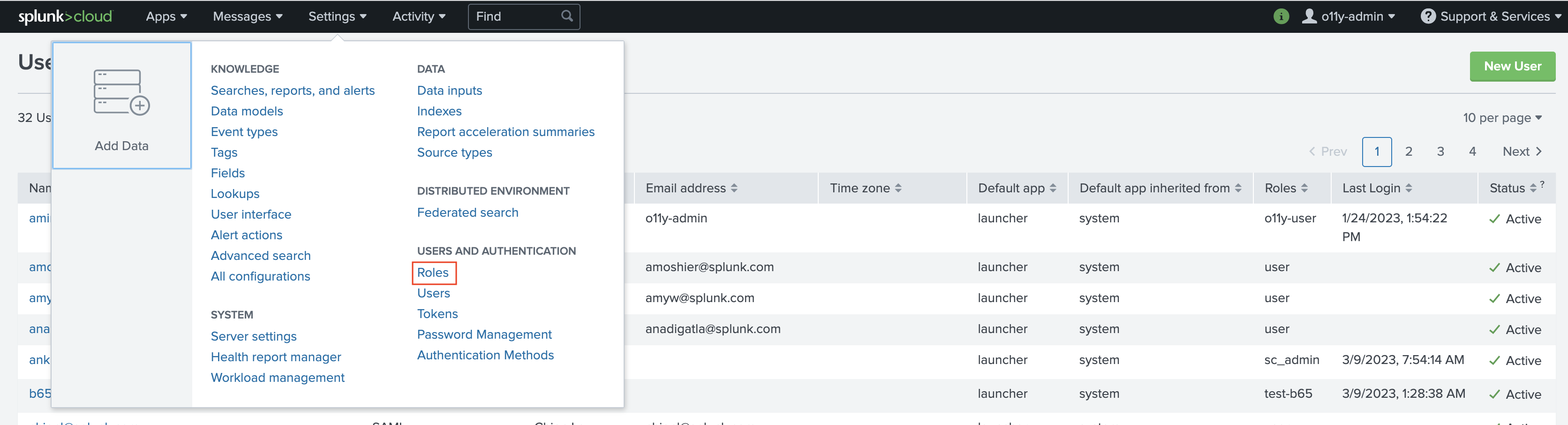
To configure a role in Splunk Cloud Platform for the Log Observer Connect service account, select Settings then select Roles.
Select the role from which you want the Log Observer Connect service account to inherit capabilities. The Log Observer Connect service account is a role that can access the specific Splunk Cloud Platform indexes that you want your users to search in Log Observer Connect. Typically, admins select the Splunk Cloud Platform user role as the base role for a Log Observer Connect service account.
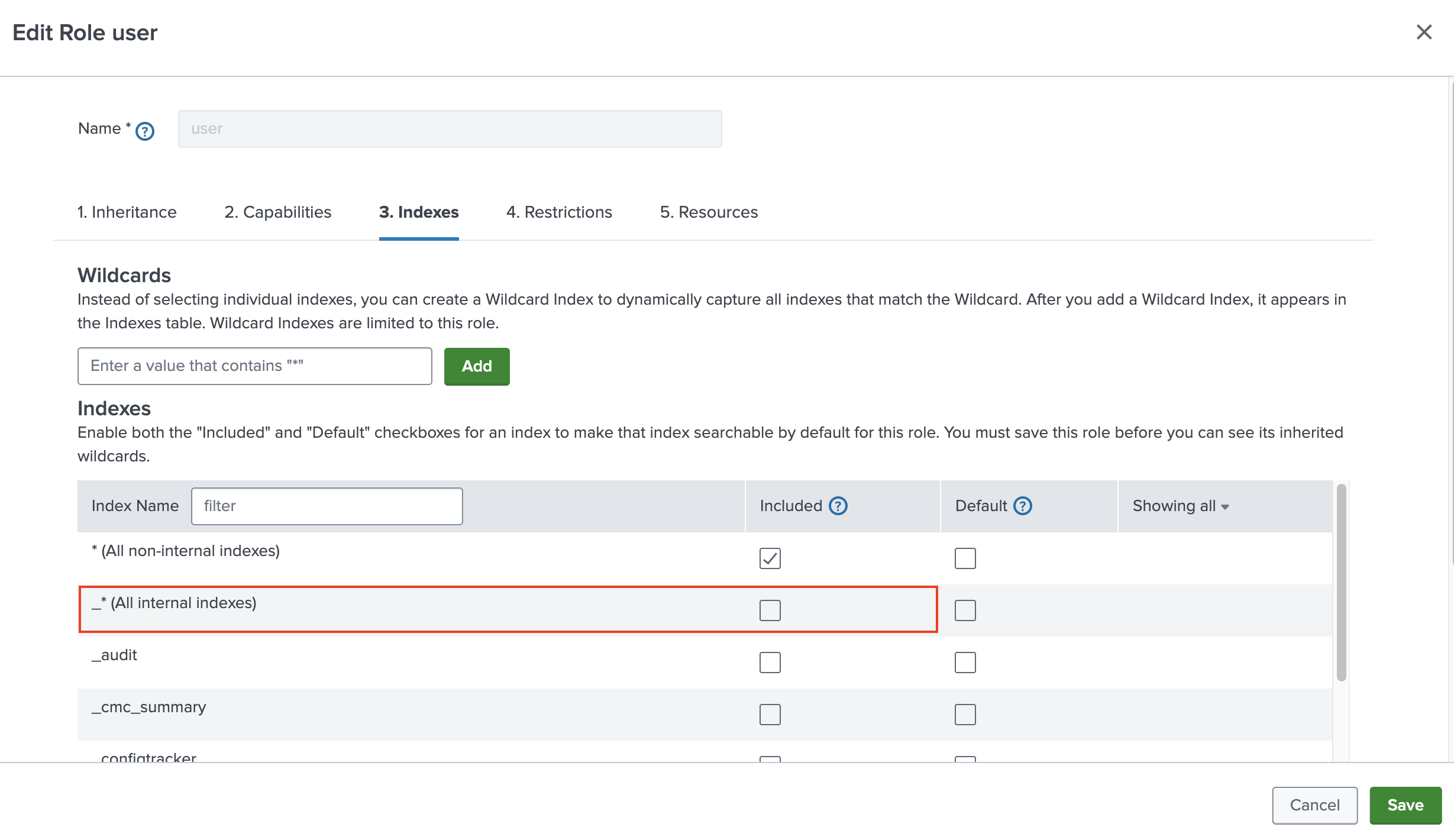
On the Indexes tab in the Included column, deselect *(All internal indexes) and select the indexes that you want users to query in Log Observer Connect.
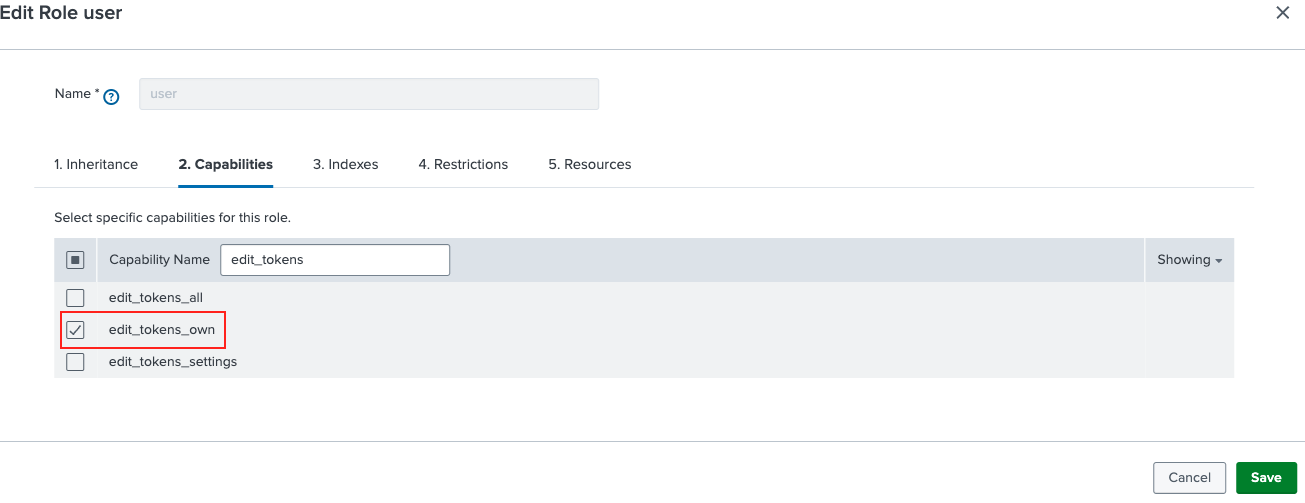
On the Capabilities tab, ensure that
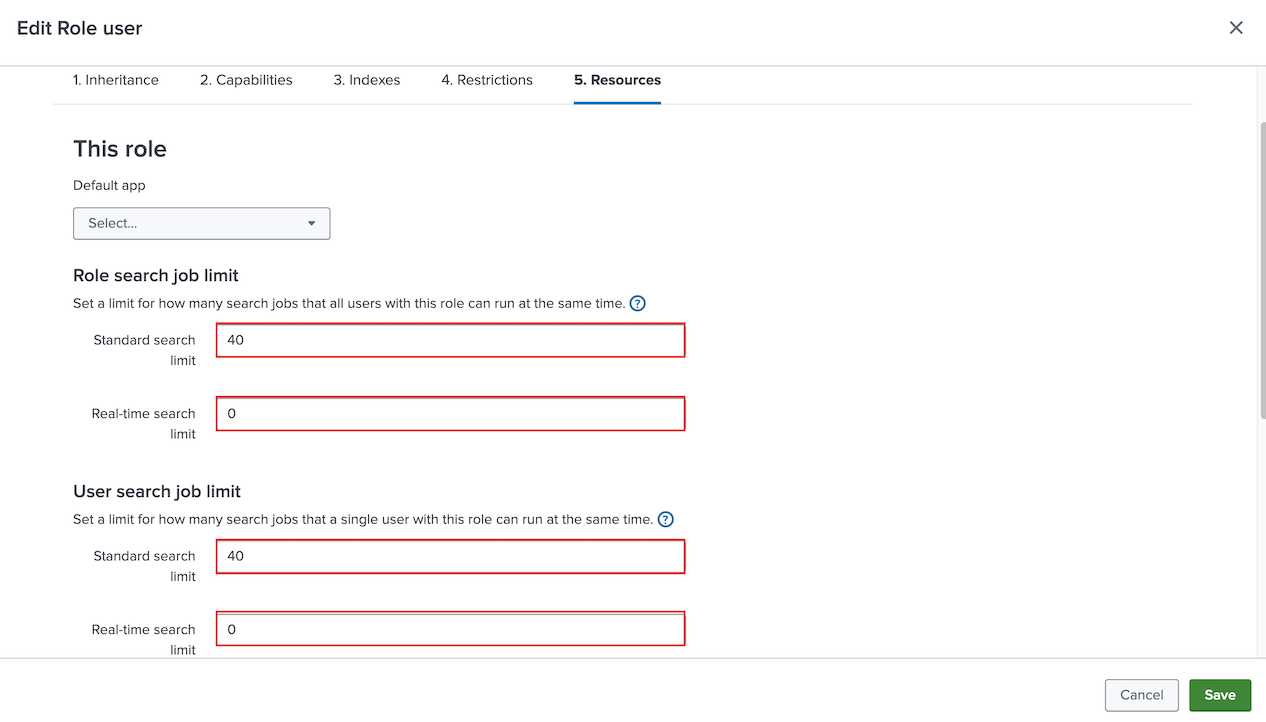
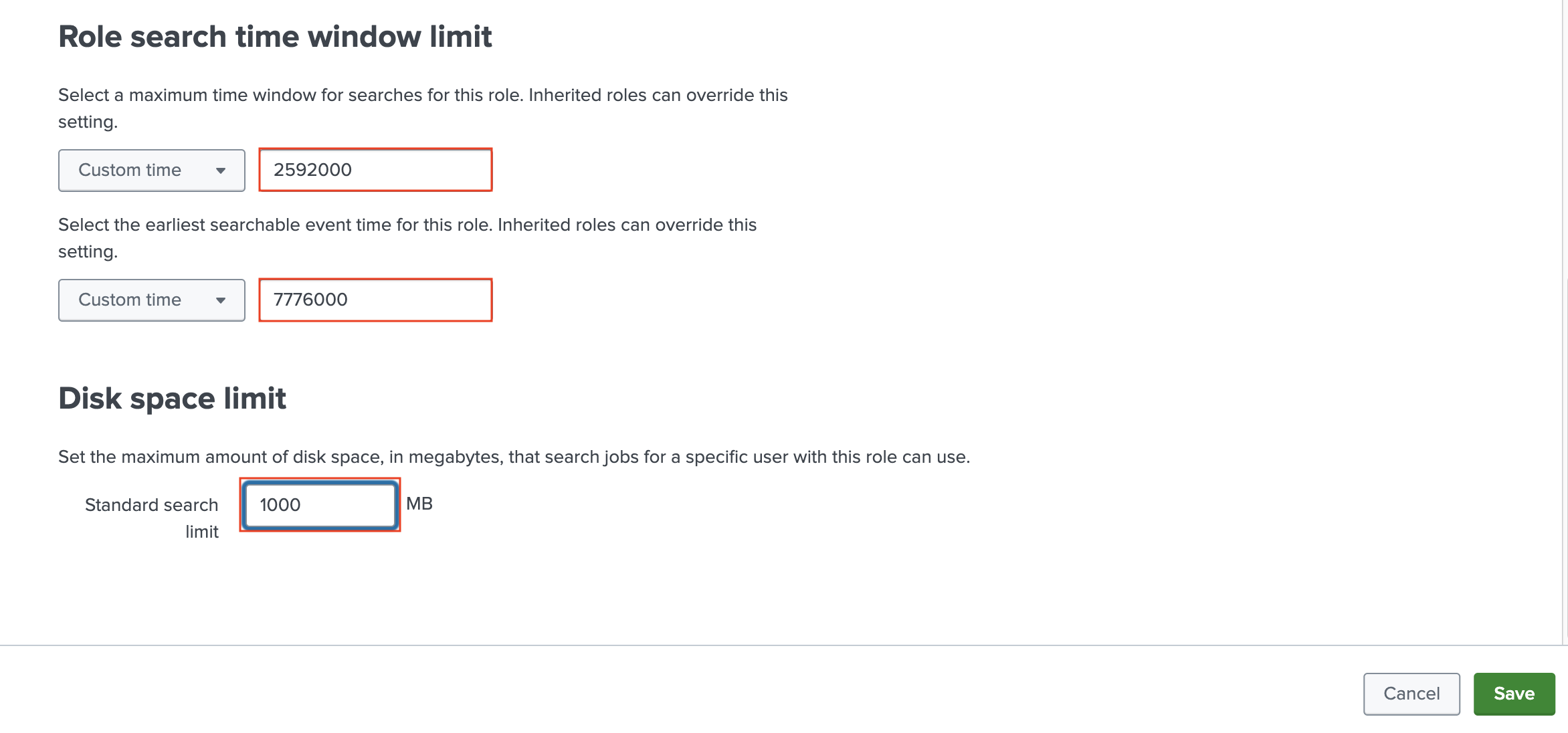
edit_tokens_ownandsearchare selected. Also, ensure thatindexes_list_allis not selected.On the Resources tab, enter a Standard search limit of 40 for both Role search job limit and User search job limit. Enter 0 for Real-time search limit for both role and user search job limits.
The limit of 40 assumes that you have 10 Log Observer Connect users. To determine your ideal Standard search limit, multiply the number of Log Observer Connect users you have by 4. For example, if you have 20 Log Observer users, enter a Standard search limit of 80 for both Role search job limit and User search job limit.
Now, in the Role search time window limit section of the Resources tab, select Custom time and enter 2592000 seconds (30 days) for the maximum time window for searches for this role. Do not use commas when entering numbers. For the earliest searchable event time for this role, select Custom time and enter 7776000 seconds (90 days). In the Disk space limit section enter a Standard search limit of 1000 MB. Select Save.
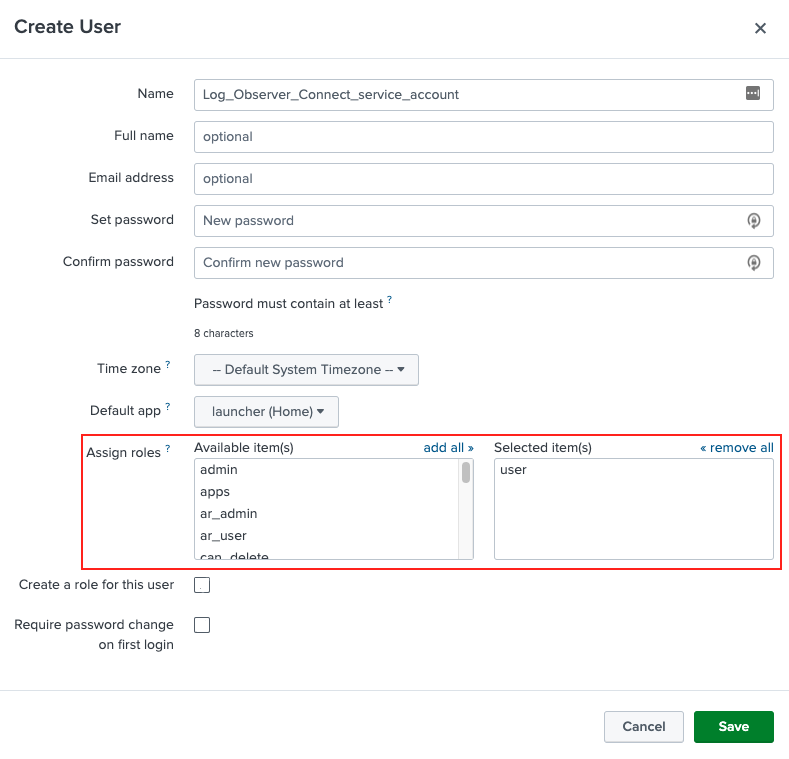
Next, in Splunk Cloud Platform, go to Settings then Users and create the user for the Log Observer Connect service account. In the Assign roles section, assign to the user the role you created in the preceeding steps for the Log Observer Connect service account.
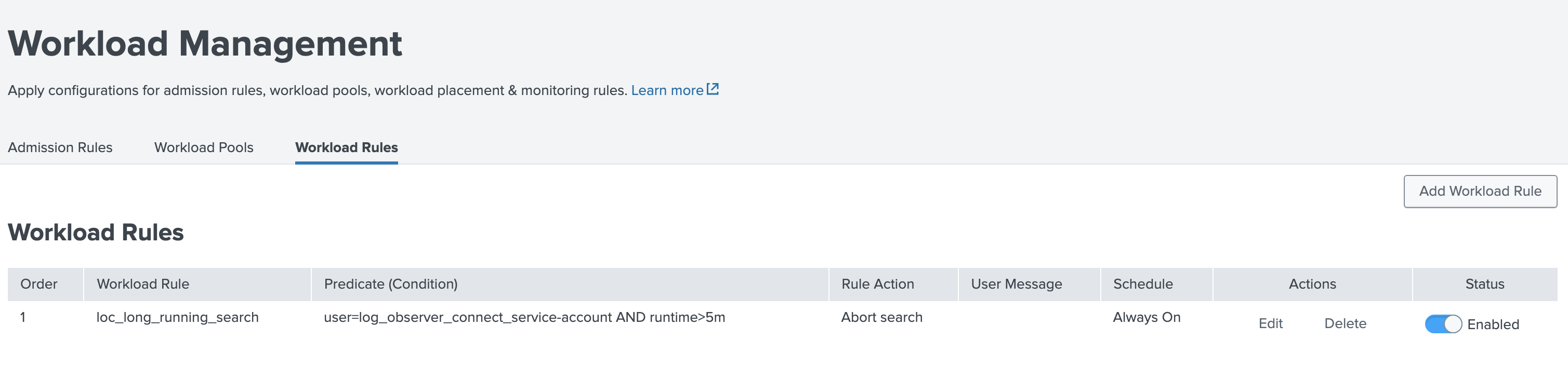
Add a Workload Rule in Splunk Cloud Platform to limit Log Observer Connect searches to 5 minutes. This limit maintains a responsive experience for Log Observer users and reduces the chances that Log Observer Connect searches are queued. Follow the guidance in Create a Workload Rule in Splunk Web and configure the rule as follows:
Predicate: user=[your_Log_Observer_Connect_service-account_name] AND runtime>5m Schedule: Always on Action: Abort search
After creating the Workload Rule, it appears in Workload Management on the Workload Rules tab as follows:
Secure a connection to your Splunk Cloud Platform instance in Splunk Observability Cloud. See Prerequisites for more information on the IPs to allow.
To get help from Splunk Support, Submit a support ticket.
To do it yourself, add your public IPv4 address to your Splunk Cloud Platform allow list by following instructions in Add subnets to IP allow lists .
Go back to the Log Observer Connect guided setup and select Next. Enter the following:
Connection name (Be sure to give each connection a unique name.)
Service account username
Password
Splunk platform URL
https://<stackname>.splunkcloud.com:8089
Remove your IPv4 address from the IP allowlist that you added in step 9. If you are in a GCP environment, do not remove the additional GCP IP addresses that you added in step 8. Select Next.
On the Configure permissions page of the guided setup, select the Splunk Observability Cloud users who you want to give access to this connection and the associated Splunk Cloud Platform indexes.
Select Save and activate.
Note
Manage concurrent search limits using your current strategy in Splunk Cloud Platform. All searches initiated by Log Observer Connect users go through the service account you create in Splunk Cloud Platform. For each active Log Observer Connect user, four back-end searches occur when a user performs a search in Log Observer Connect. For example, if there are three users accessing Log Observer Connect at the same time, the service account for Log Observer Connect initiates approximately 12 searches in Splunk Cloud Platform.
Submit a support ticket 🔗
If you were not able to independently secure a connection to your Splunk Cloud Platform instance in step 9 in the previous section, you may submit a support ticket from your Splunk Cloud Platform instance to do this on your behalf. Submit a ticket to Splunk Support to configure your Splunk Cloud Platform instance’s IP allow list. Configuring your allow list properly opens your Splunk Cloud Platform instance management port to Log Observer Connect, which can then search your Splunk Cloud Platform instance log data. After Splunk Support prepares your Splunk Cloud Platform instance, you can securely create a connection to Log Observer Connect.
To submit a support ticket, follow these steps:
Find the following:
Your Splunk Observability Cloud organization name and region. To see this information in Splunk Observability Cloud, go to Settings, then select your profile name.
Your Splunk Cloud Platform instance name, the URL prefix of your Splunk Cloud Platform deployment, which is formatted as such: [Your_instance_name].splunkcloud.com.
Log in to your Splunk Cloud Platform instance and select Support.
Select Support Portal from the drop-down list to submit a case ticket.
In the description of your ticket, paste the following and enter the relevant values for your organization:
OrgID: <enter-orgid> Realm: <enter-realm> Instance Name: <instance-name> Request: Please securely open our Splunk Cloud Platform instance management port (8089) and add the IP addresses of the above realm to our allow list so that we can enable Log Observer Connect.
Troubleshooting 🔗
See Troubleshoot Log Observer Connect setup to learn how to solve common issues with Log Observer Connect.