Troubleshoot AWS-managed Metric Streams 🔗
See the following topics when experiencing AWS-managed Metric Streams related issues.
Note
See also Troubleshoot your AWS integration and Troubleshoot Splunk-managed Metric Streams.
I’ve enabled AWS-managed Metric Streams in my AWS integration but I do not see any metrics streaming in 🔗
Log in to your AWS console and review the following:
Check the Metric Stream integration settings 🔗
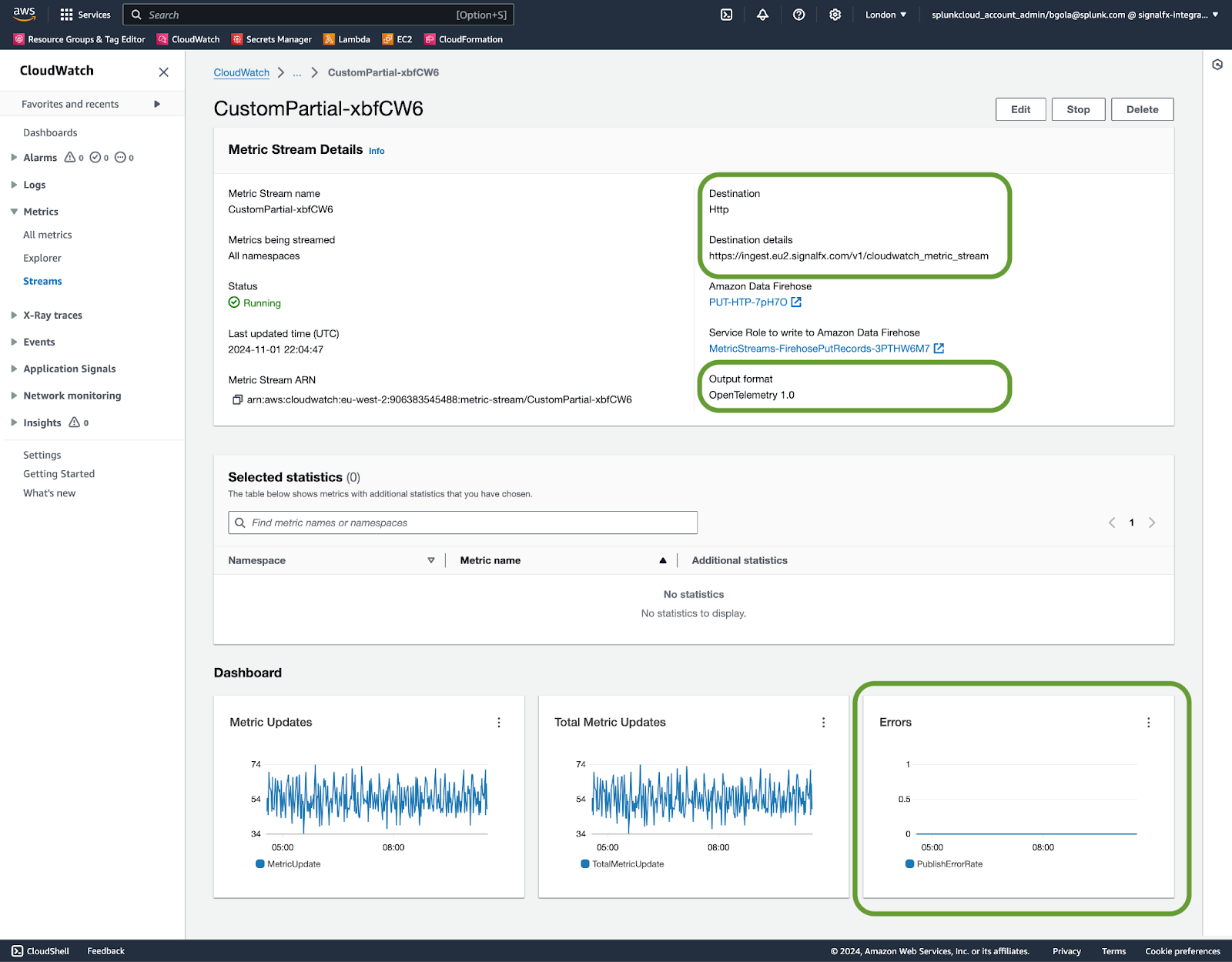
In your CloudWatch console check the following:
The Errors chart must show zero errors.
The destination and output format must look similar to what is visible on the screenshot below. Note that your destination URL might use a different realm, for example https://ingest.us0.signalfx.com/v1/cloudwatch_metric_stream.
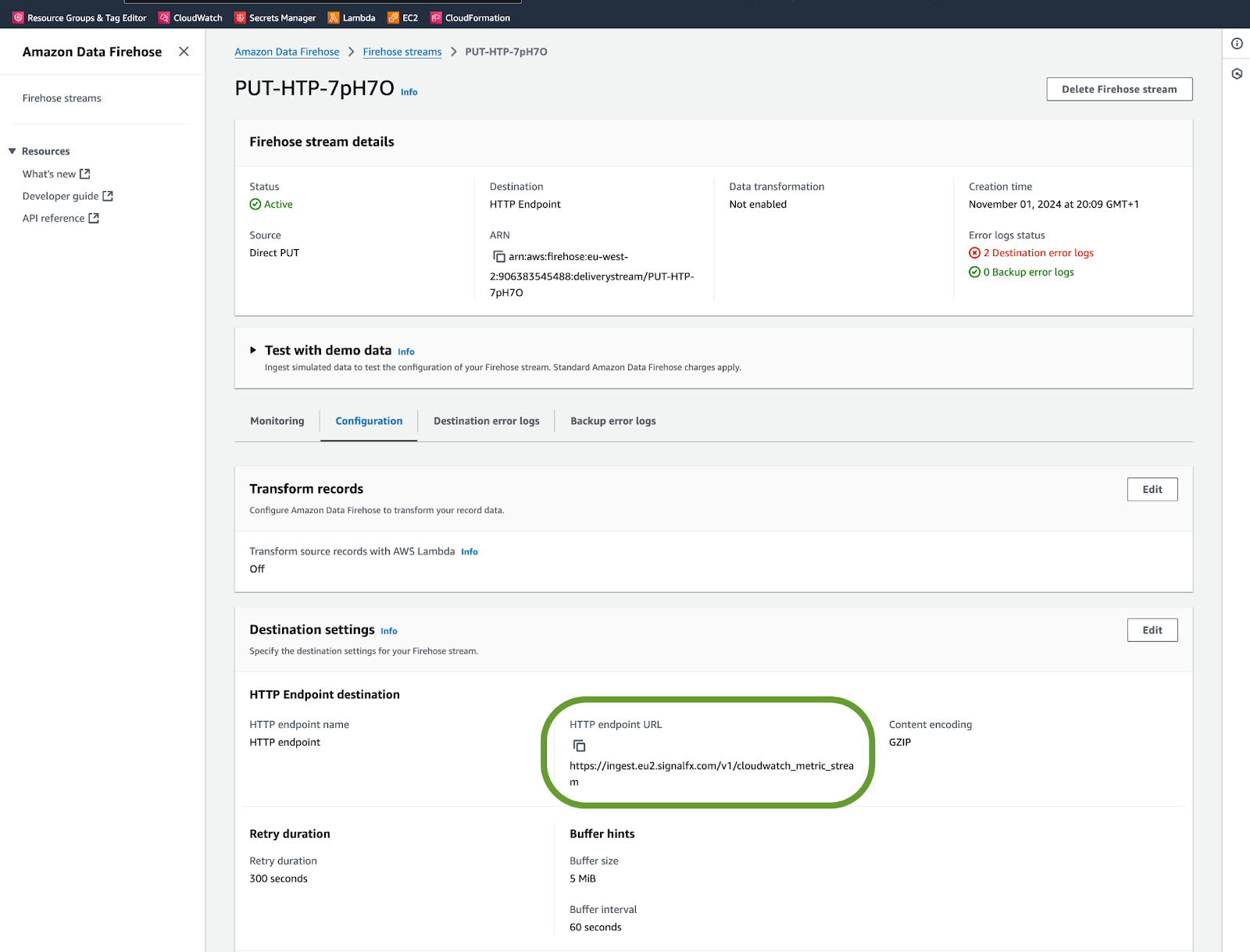
Check the associated Firehose stream configuration 🔗
Go to your AWS console and check your Firehose stream configuration:
Check the associated Firehose stream metrics 🔗
Make sure that:
Incoming records must have non-zero values.
Note that if there’s a low volume of traffic going through the stream, the value of
IncomingRecords (per second average)can be significantly lower thanRecordsPerSecondLimit, and therefore it might look like there are no incoming records.
HTTP endpoint delivery success must be 100%.
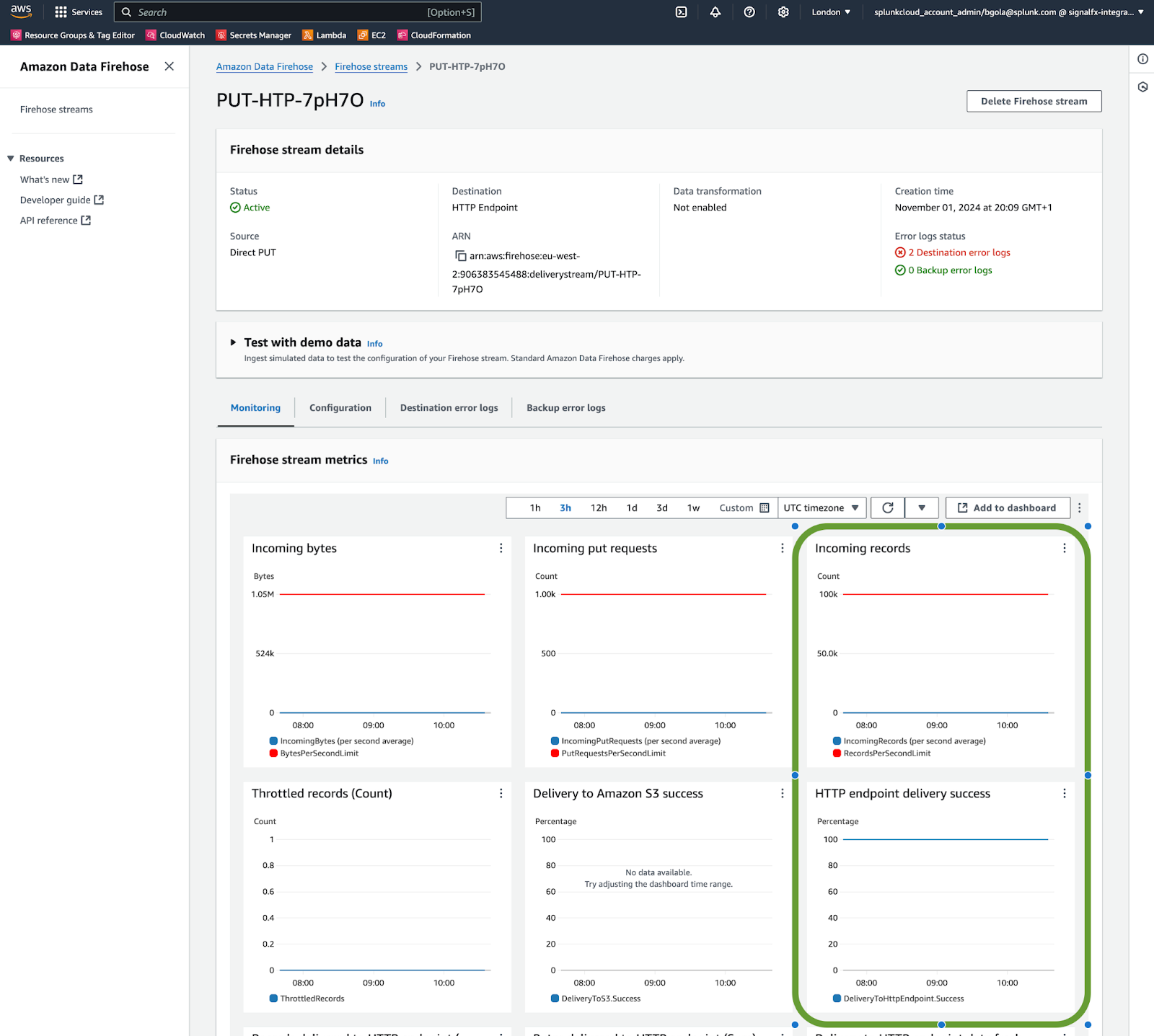
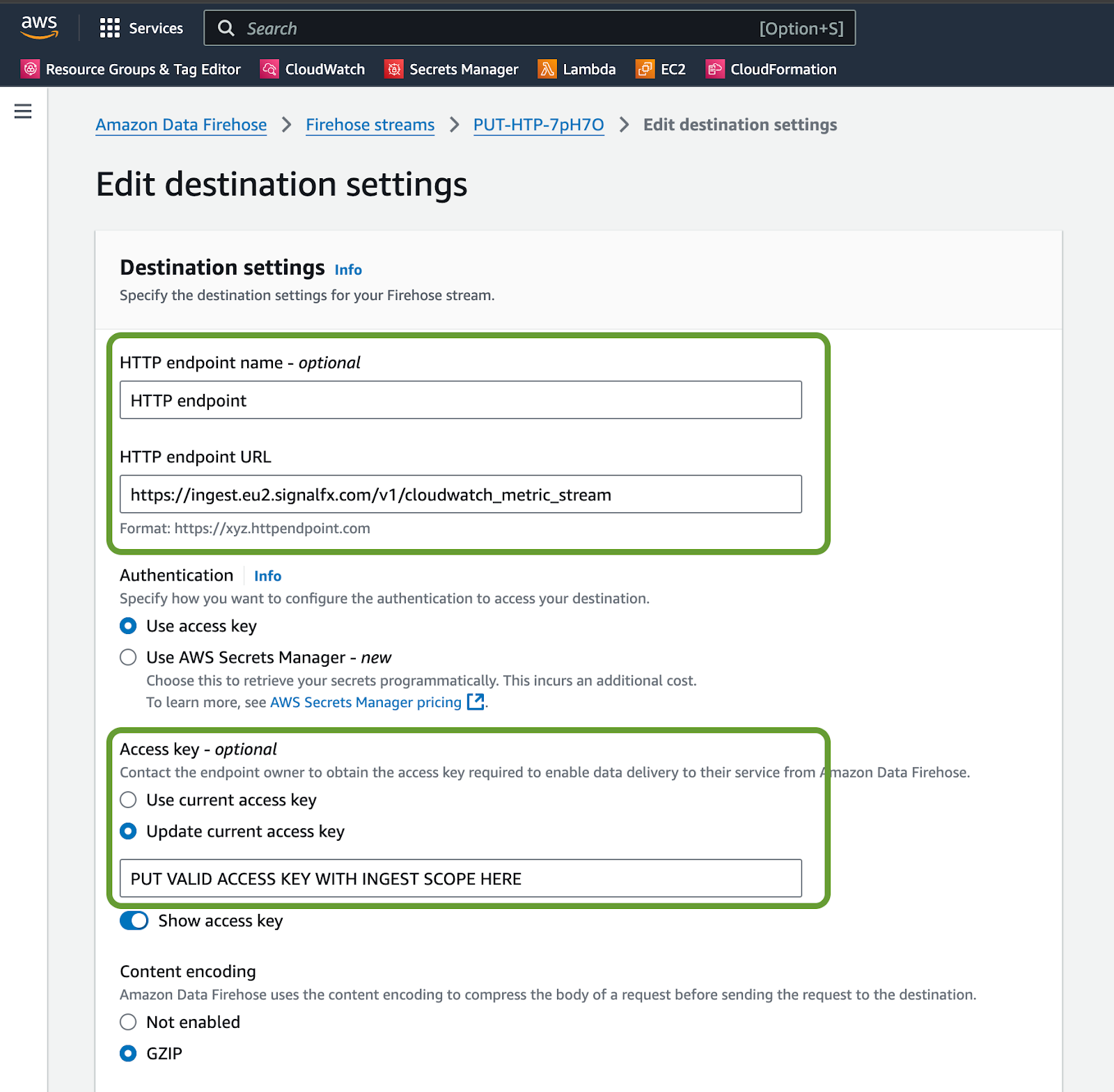
If there are any errors visible on the HTTP endpoint delivery success chart, update the Firehose stream destination settings to ensure that the HTTP endpoint is correct and use a new access token with INGEST scope.
Note that your destination URL might use a different realm, for example https://ingest.us0.signalfx.com/v1/cloudwatch_metric_stream.
Review roles and permissions 🔗
Check the following:
Review the AWS role used by the Metric Streams.
Make sure all required permissions are included, and that the CloudWatch metric stream region and the region listed in the AWS policy are the same.
To find the AWS role used by the Metric Stream, go to the Stream overview page under the Service Role to write to Amazon Data Firehose label.
This is a sample AWS policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"firehose:PutRecord",
"firehose:PutRecordBatch"
],
"Resource": [
"arn:aws:firehose:eu-west-2:906383545488:deliverystream/PUT-HTP-7pH7O"
]
}
]
}
These are the trust relationships:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "streams.metrics.cloudwatch.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}