Create field aliases 🔗
An alias is an alternate name that you assign to a field, allowing you to use that name to search for events that contain that field. An alias is added to the event alongside the original field name to make it easier to find the data you want and to connect your data sources through Related Content suggestions.
Field Aliasing occurs at search time, not index time, so it does not transform your data. Field Aliasing does not rename or remove the original field name. When you alias a field, you can search for it by its original name or by any of its aliases.
Prerequisites 🔗
To create field aliases, you must have an administrator or power user role in Splunk Observability Cloud.
When to use Field Aliasing 🔗
Use Field Aliasing when the following situations are true:
You use Log Observer Connect to get logs data, and do not have access to Log Observer Pipeline Management.
You do not want to use any indexing capacity by creating additional log processing rules.
You want to retain your original field names, so you do not want to create a log processing rule, which transforms your data at index time.
You want the new alias to affect every log message, even those that came in from a time before you created the alias.
You want to display a field separately at the top of the log details flyout
Field Aliasing examples 🔗
Displaying a field separately in the log details flyout 🔗
For convenience, your team can choose to always display a particular field separately at the top of the log details flyout. To display the field of your choice separately, alias the desired field to the message field. The log details flyout in Log Observer always displays the message field at the top. When you alias another field to the message field, it appears in the standalone section called MESSAGE at the top of the log details flyout.
For example, say your team most frequently uses the summary field. Add an alias for the summary field called message. The summary field still exists but is also known as message and appears in the MESSAGE section of the log details flyout on the right side of the screen.
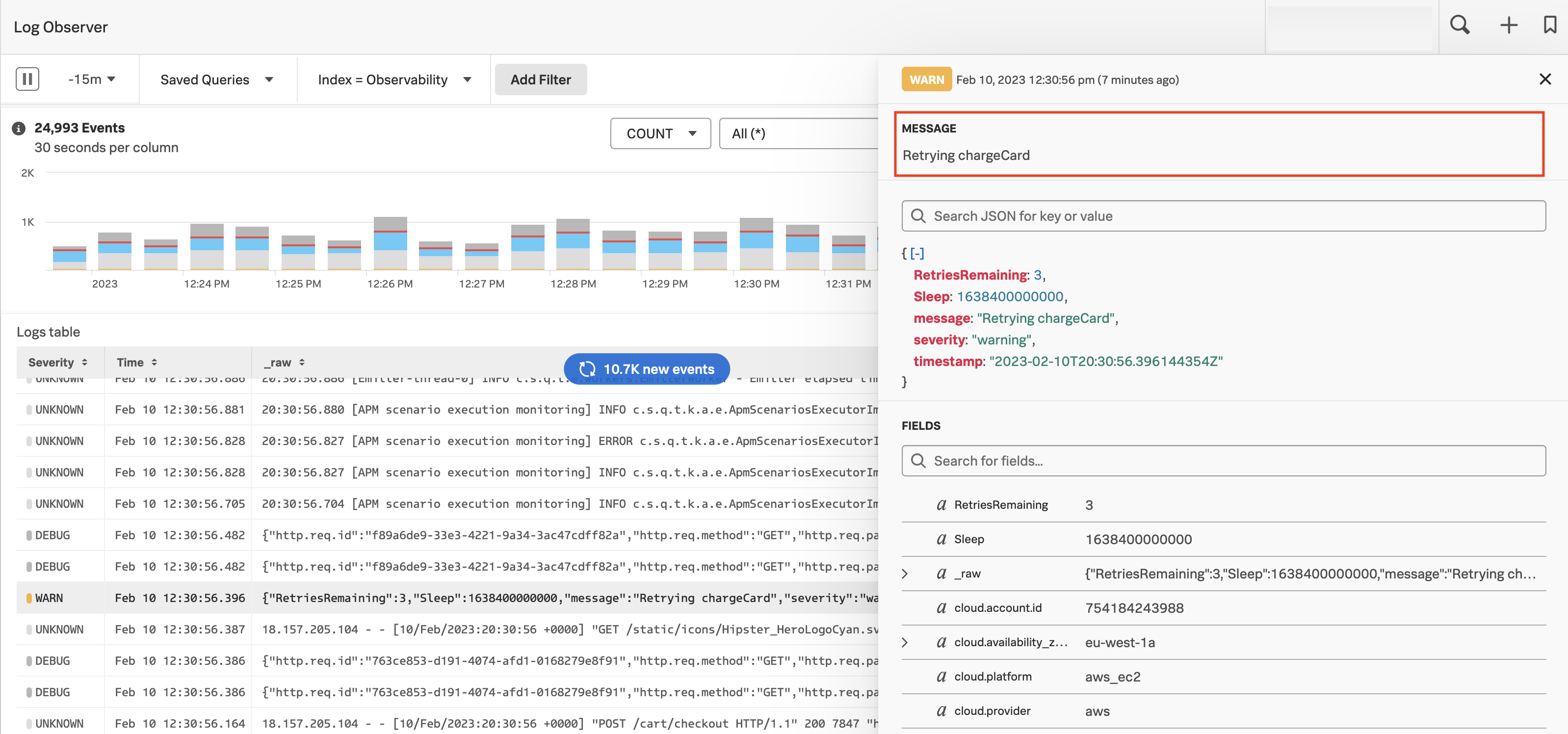
Normalizing field names 🔗
One data source might have a field called http_referrer. This field might be misspelled in your source data as http_referer. Use field aliases to capture the misspelled field in your original source data and map it to the expected field name without modifying your logging code.
You may have two data sources that call the same field by somewhat different names. For example, one data source might have a field called EventID while another data source might have a field called EventRecordID. You can tell by the values that these fields represent the same thing. You can create a field alias that maps EventID to EventRecordID to aggregate all logs with either of those field names to the field EventRecordID for analysis in Log Observer.
Create a new field alias 🔗
To create a new field alias, follow these steps:
In Splunk Observability Cloud navigation menu, go to Settings > Log Field Aliasing and click Add a new alias.
In Original field name, enter the name of the field you want to create an alias for. Start typing then select the field name you want from the drop-down list of all available fields.
In Alias, enter the new name that you want this field to have in addition to its original name. A list of other existing field names appears in the drop-down list. Click Save and Activate.
Click Save and Activate.
Your new field alias appears in Your aliases and defaults to active. It is now applied to your search-time queries. To deactivate the alias, find the field in Your aliases and click the toggle next to Active.
Deactivate or delete a field alias 🔗
You can deactivate or delete a field alias if you do not want the alias to be applied to your search-time queries. You cannot edit a field alias. Instead, you must delete it and create a new one.
To deactivate or delete a field alias, do the following:
Go to Settings > Log Field Aliasing.
Find the alias you want to deactivate or delete in the Your aliases list.
To deactivate the alias, click the toggle next to Active in the STATUS column. To delete the alias, click the trash icon in the row for that alias.