Network dashboards
| Information on this page is currently a work in progress; expect frequent near-term updates. |
The Network dashboards provide insight into the network and network-based devices, including routers, switches, firewalls, and IDS devices.
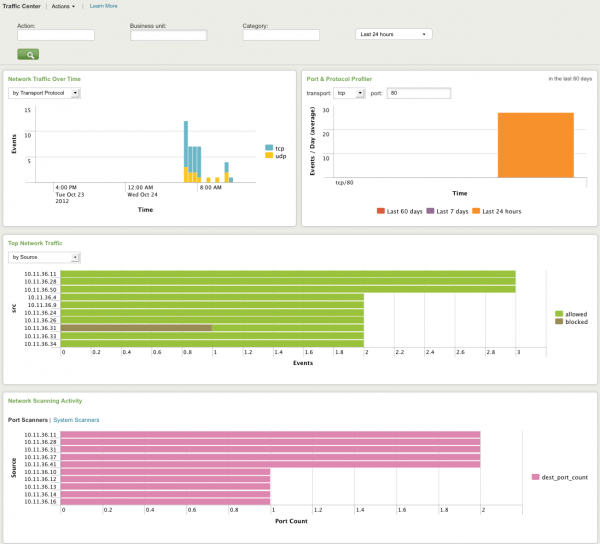
Traffic Center
The Traffic Center dashboard profiles overall network traffic, helps detect trends in type and changes in volume of traffic, and helps to isolate the cause (for example, a particular device or source) of those changes.
Need updated screenshot
Relevant data sources
Relevant data sources include all the traffic on the network, including overall volume, devices or users generating traffic, per-port traffic, and data from vulnerability scanners on the network.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Network_Traffic data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "network" AND "communicate".
Dashboard description
Traffic Center dashboard data is derived from the Network_Traffic data model and accelerated automatically.
To verify that traffic data is present, use this search:
| datamodel Network_Traffic All_Traffic search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Network_Traffic by user
For more information on distributed namespaces, see "Verify that a data model namespace exists" in the troubleshooting section of this manual. See "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that traffic data is indexed in Splunk | tag=network tag=communicate or | datamodel Network_Traffic All_Traffic search |
Returns all traffic data from your device(s) |
| Verify that traffic data is normalized to the Common Information Model properly | | datamodel Network_Traffic All_Traffic search | table action, dvc, transport, src, dest, src_port, dest_port | Returns a list of events and the specific traffic data fields populated from your device(s) |
Additional Information
For more information about using the Traffic Center dashboard, see "Traffic Center dashboard" in the Splunk App for Enterprise Security User Manual.
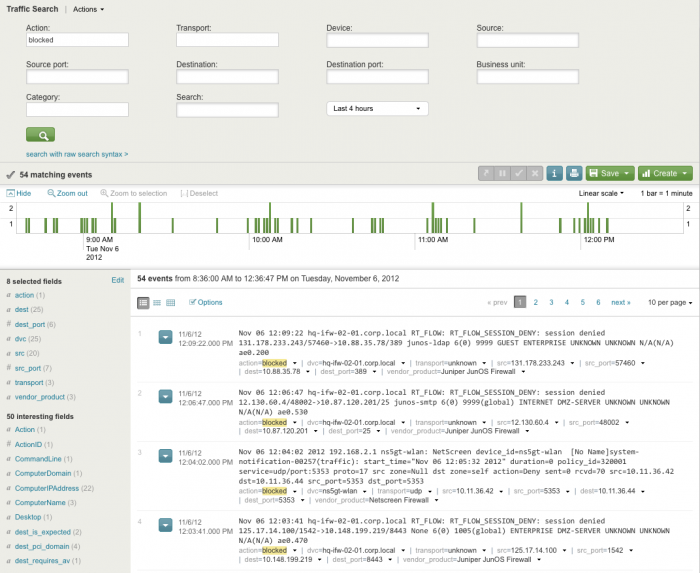
Traffic Search
The Traffic Search dashboard displays an overview of all traffic data, firewall events, and port information.
Need updated screenshot
Use the filters to narrow your search. Click on an item to drill down to the raw data represented.
Relevant data sources
Relevant data sources for the Traffic Search dashboard include data from firewall devices, port data, and log file entries.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Network Traffic data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "network" AND "communicate".
Dashboard description
Traffic Search dashboard data is derived from the Network_Traffic data model and accelerated automatically.
To verify that network data is present, use this search:
| datamodel Network_Traffic All_Traffic search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Network_Traffic by user
For more information on distributed namespaces, see "Verify that a data model namespace exists" in the troubleshooting section of this manual. See "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that traffic data is indexed in Splunk | tag=network tag=communicate or | datamodel Network_Traffic All_Traffic search |
Returns traffic data from your device(s) |
| Verify that traffic data is normalized to the Common Information Model properly | | datamodel Network_Traffic All_Traffic search | table action, dvc, transport, src, dest, src_port, dest_port, vendor, product | Returns a list of events and the specific traffic data fields populated from your device(s) |
Additional Information
For more information about using the Traffic Search dashboard, see "Traffic Search dashboard" in the Splunk App for Enterprise Security User Manual.
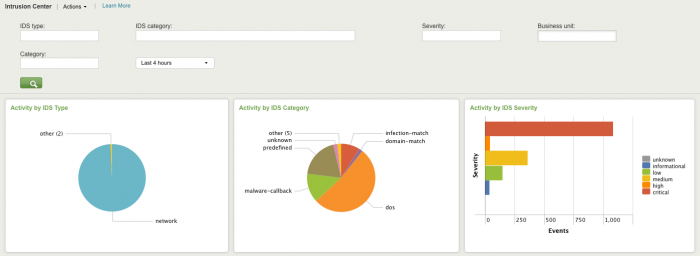
Intrusion Center
The Intrusion Center dashboard provides an overview of all network intrusion events from the Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) on the network that are providing data into Splunk.
Need updated screenshot
Relevant data sources
Relevant data sources for the Intrusion Center dashboard include IDS and IPS data from devices in your network.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Intrusion Detection data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "ids" AND "attack".
Dashboard description
Intrusion Center dashboard data is derived from the Intrusion_Detection data model and accelerated automatically.
To verify that intrusion data is present, use this search:
| datamodel Intrusion_Detection IDS_Attacks search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Intrusion_Detection by user
For more information on distributed namespaces, see "Verify that a data model namespace exists" in the troubleshooting section of this manual. See "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that intrusion center data is indexed in Splunk | tag=ids tag=attack or | datamodel Intrusion_Detection IDS_Attacks search |
Returns intrusion center data from your device(s) |
| Verify that intrusion center data is normalized to the Common Information Model properly | | datamodel Intrusion_Detection IDS_Attacks search | table dvc signature severity, src dest user vendor_product is_network is_wireless is_host is_application | Returns a list of events and the specific intrusion data fields populated from your device(s) |
Additional Information
For more information about using the Intrusion Center dashboard, see "Intrusion Center dashboard" in the Splunk App for Enterprise Security User Manual.
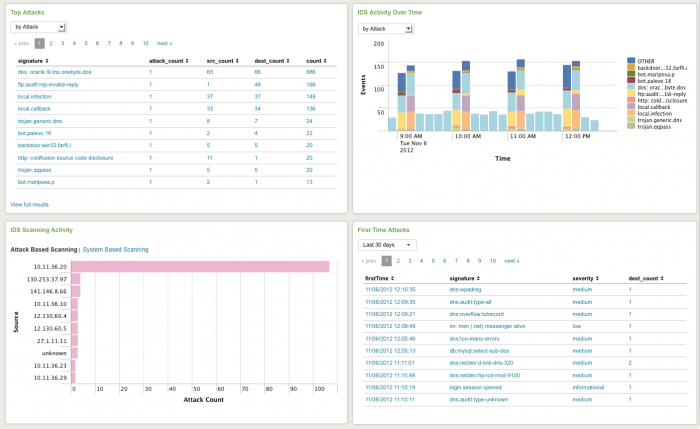
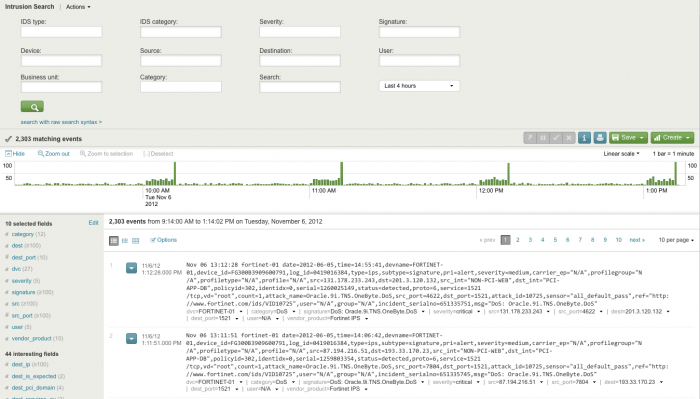
Intrusion Search
The Intrusion Search dashboard helps you to search for IDS-related or IPS-related events such as attacks or unusual activity.
Need updated screenshot
Use the filters at the top of the dashboard to narrow your search. Click on an item to view the raw data.
Relevant data sources
Relevant data sources for the Intrusion Search dashboard include IDS and IPS data from devices in your network and data indexed in Splunk.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Intrusion Detection data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "ids" AND "attack".
Dashboard description
Intrusion Search dashboard data is derived from the Intrusion_Detection data model and accelerated automatically.
To verify that intrusion data is present, use this search:
| datamodel Intrusion_Detection IDS_Attacks search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Intrusion_Detection by user
For more information on distributed namespaces, see "Verify that a data model namespace exists" in the troubleshooting section of this manual. See "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that intrusion search data is indexed in Splunk | tag=ids tag=attack or | datamodel Intrusion_Detection IDS_Attacks search |
Returns local intrusion search data from your device(s) |
| Verify that intrusion search data is normalized to the Common Information Model properly | | datamodel Intrusion_Detection IDS_Attacks search | table dvc signature severity, src dest user vendor_product is_network is_wireless is_host is_application | Returns a list of events and the specific intrusion search data fields populated from your device(s) |
Additional Information
For more information about using the Intrusion Search dashboard, see "Intrusion Search dashboard" in the Splunk App for Enterprise Security User Manual.
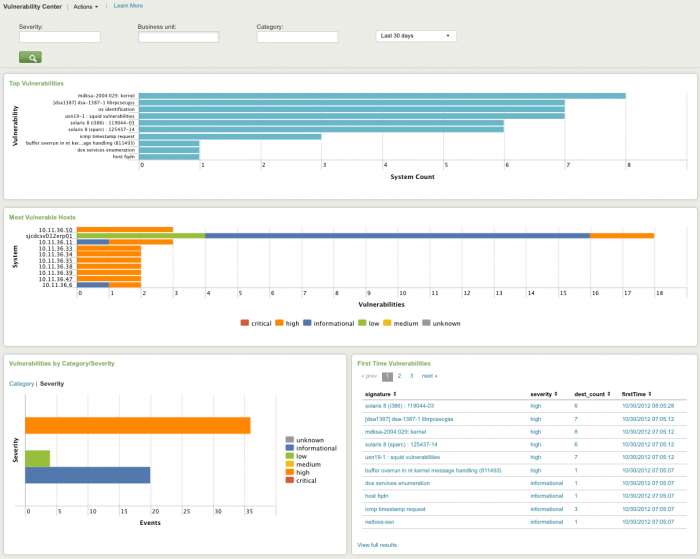
Vulnerability Center
The Vulnerability Center provides an overview of the events detected by vulnerability scanners, which proactively identify issues that may be used to gain unauthorized access to the IT systems.
Need new screenshot
Relevant data sources
Relevant data sources for the Vulnerability Center dashboard include data from any vulnerability management systems in your network, along with host and user data indexed by Splunk.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Vulnerabilities data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "vulnerability" AND "report".
Dashboard description
Vulnerability Center dashboard data is derived from the Vulnerabilites data model and accelerated automatically.
To verify that vulnerability data is present, use this search:
| datamodel Vulnerabilites search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Vulnerabilites by user
For more information on distributed namespaces, see "Verify that a data model namespace exists" in the troubleshooting section of this manual. See "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that vulnerabilty data is indexed in Splunk | tag=vulnerability tag=report or | datamodel Vulnerabilites search |
Returns all vulnerability data from your device(s) |
| Verify that vulnerability data is normalized to the Common Information Model properly | | datamodel Vulnerabilites search | table category severity signature dest | Returns a list of events and the specific vulnerability data fields populated from your device(s) |
Additional Information
For more information about using the Vulnerability Center dashboard, see "Vulnerability Center dashboard" in the Splunk App for Enterprise Security User Manual.
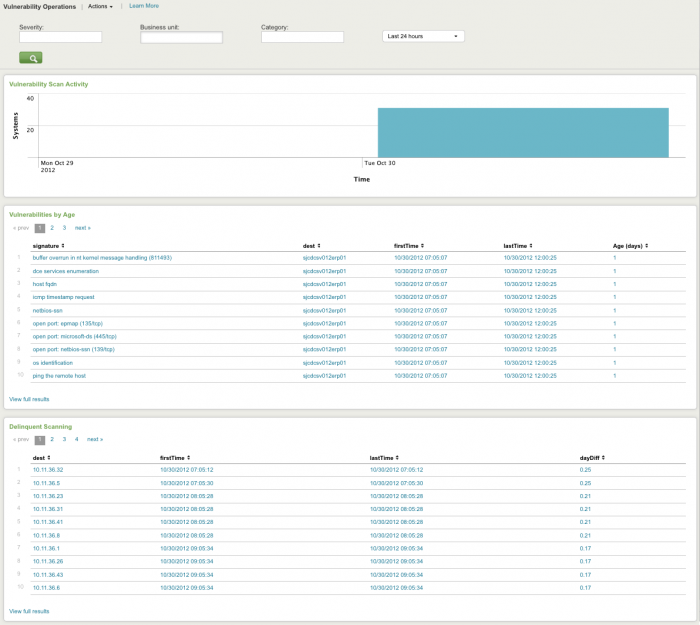
Vulnerability Operations
The Vulnerability Operations dashboard tracks the status and activity of the vulnerability detection products deployed in your environment.
Need new screenshot
Use the fields at the top of the dashboard to narrow your search. Click on an item to drill down to the raw data.
Relevant data sources
Relevant data sources for the Vulnerability Operations dashboard include data from any IDS or IPS tracking device in your network, along with host and user data indexed in Splunk.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Vulnerabilities data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "vulnerability" AND "dvc" AND "report".
Dashboard description
Vulnerability Operations dashboard data is derived from the Vulnerabilities data model and accelerated automatically.
To verify that vulnerability data is present, use this search:
| datamodel Vulnerabilities search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Vulnerabilities by user
For more information on distributed namespaces, see "Verify that a data model namespace exists" in the troubleshooting section of this manual. See "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that access data is indexed in Splunk | tag=vulnerability tag=dvc tag=report or | datamodel Vulnerabilities search |
Returns all vulnerability data from your device(s) |
| Verify that vulnerability data is normalized to the Common Information Model properly | | datamodel Vulnerabilities search | table severity category business_unit time | Returns a list of events and the specific vulnerability data fields populated from your device(s) |
Additional Information
For more information about using the Vulnerability Operations dashboard, see "Vulnerability Operations dashboard" in the Splunk App for Enterprise Security User Manual.
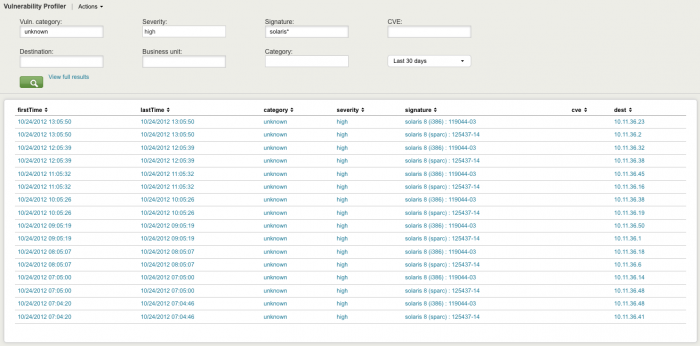
Vulnerability Profiler
The Vulnerability Profiler helps you to search for all vulnerability-related events in your environment.
Need new screenshot
Use the fields to filter results and narrow your search. Click an item to drill down to the raw data.
Relevant data sources
Relevant data sources for the Vulnerability Profiler dashboard include data from any IDS or IPS tracking device in your network, along with host and user data indexed by Splunk.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Vulnerabilities data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "vulnerability".
Dashboard description
Vulnerability Profiler dashboard data is derived from the Vulnerabilities data model and accelerated automatically.
To verify that vulnerability data is present, use this search:
| datamodel Vulnerabilities search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Vulnerabilities by user
For more information on distributed namespaces, see "Verify that a data model namespace exists" in the troubleshooting section of this manual. See "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that access data is indexed in Splunk | tag=vulnerability or | datamodel Vulnerabilities search |
Returns all vulnerability data from your device(s) |
| Verify that vulnerability data is normalized to the Common Information Model properly | | datamodel Vulnerabilities search | table severity category signature cve dest | Returns a list of events and the specific vulnerability data fields populated from your device(s) |
Additional Information
For more information about using the Vulnerability Profiler dashboard, see "Vulnerability Profiler dashboard" in the Splunk App for Enterprise Security User Manual.
| Endpoint dashboards | More Network dashboards |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.0, 3.0.1
 Download manual
Download manual
Feedback submitted, thanks!