Notable event statuses
Notable event statuses are used to manage workflow of notable events in Splunk for Enterprise Security.
Default status
By default a notable event in the Incident Review dashboard is assigned a status of New and Unassigned. The initial urgency is determined when the notable event is generated.
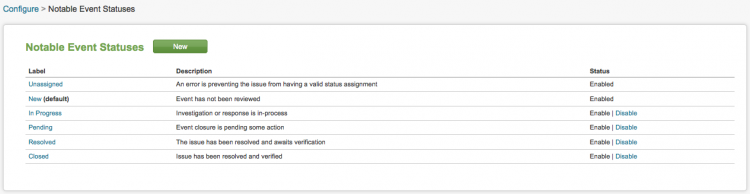
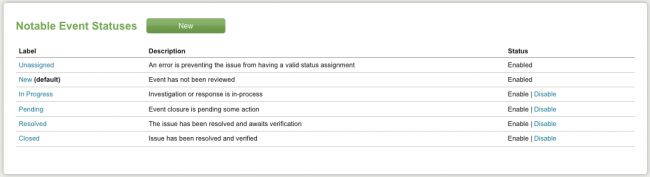
Notable event status options are:
- Unassigned - the event has not been assigned
- New (default) - the event has not yet been reviewed
- In Progress - investigation or response is in progress
- Pending - event closure is pending some action
- Resolved - the issue is resolved and awaits verification
- Closed - the issue has been resolved and verified
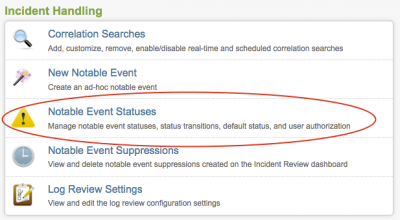
Click New to add a status option. Click on a status label to edit that status. The notable event status editor is displayed.
From this panel you can change the status of the notable event, enable or disable it, or modify status transitions.
Owner options for notable events are:
- Unassigned (default)
- Admin
- Esadmin
- Esanalyst
- Splunk-system-role
Modify status
Notable event status can be modified from the Incident Review dashboard.
To modify an event status:
- Click Finalize (
 ) to finalize any real-time searches that may be running.
) to finalize any real-time searches that may be running. - Select an event and check the box next to it.
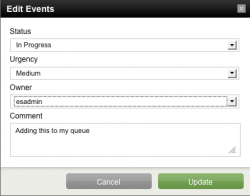
- Click Edit selected events to open the Edit Event panel.
From here you can change status of the event, assign it to an Enterprise Security Admin (esadmin), and add a comment.
You can also reassign the urgency of a notable event. Urgency levels for notable events are:
- Low
- Medium
- Informational
- High
- Critical
Security Analysts may be required to enter comments when reviewing notable events to improve the quality of records. In most Security Information and Event Management (SIEM) configurations, comments are always mandatory for changing the characteristics of a security event. This saves tracking down the person to understand why they did what they did, and creates a more complete audit record.
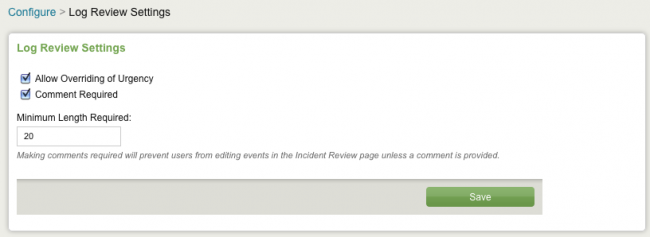
Mandatory commenting is an optional feature. By default is it turned off. To enable mandatory commenting, go to Configure > Log Review Settings. Select "Comment Required" and specify a minimum comment length.
Note: The option to "Allow Overriding of Urgency" can be disabled from this same panel, by deselecting it (Configure > Log Review Settings).
If the modified event is not displayed when the Incident Review dashboard refreshes, check to see that the filters at the top of the dashboard are not removing the modified events (for example, search for "New" when the event is changed to "In Progress".
See "How to edit events in the Incident Review Dashboard" in the Enterprise Security User Manual for more information about editing notable events.
Edit Notable Event Status
The default Notable Event statuses can be edited or a new status can be added. Before editing or adding any status, it is important to plan out the status workflow to be used in the enterprise.
The workflow can then be implemented using the Notable Event Statuses editor to manage notable event statuses, status transitions, default status, and user authorization.
To implement this new workflow, use the Notable Event Status panel. Go to Configure > Notable Event Statuses.
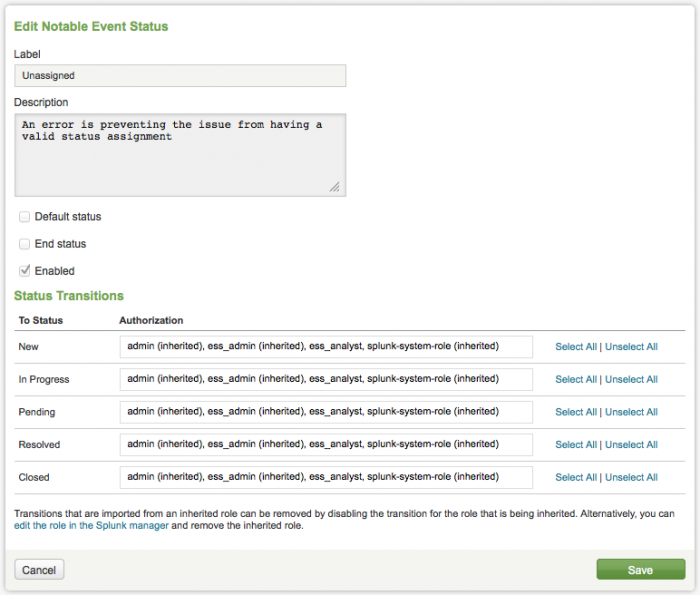
Change the assignment of a notable event by clicking on a label. Individual events can be enabled or disabled.
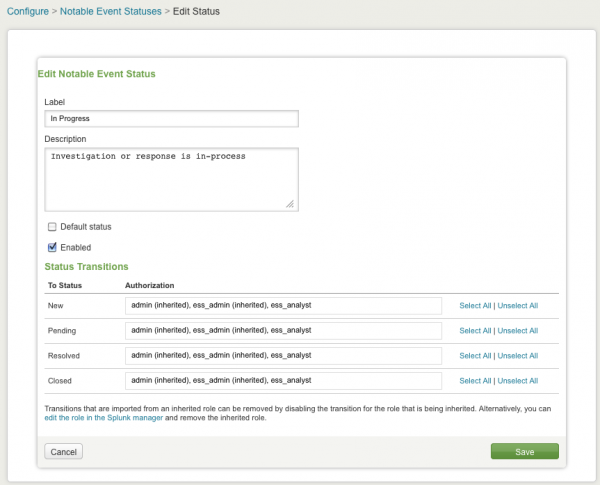
The Edit Notable Event Status panel shows the label, the description, the status, and the status transitions for a particular event. Use this panel to edit these items. Click Save to implement changes.
Status transitions
The Splunk App for Enterprise Security provides a default set of workflow status transitions.
Status transitions:
- New - transitions to In Progress when event is being investigated or reviewed
- In Progress - transitions to Pending when closure is pending some action
- Pending - transitions to Resolved when event is resolved but not verified
- Resolved - transitions to Closed after verification
- Closed - the issue has been resolved and verified
Some of these statuses can be disabled from the Edit Notable Event Status panel. Go to Configure > Notable Event Statuses. To disable a status,click Disable.
Incident workflow
The default incident workflow is for an event to be changed from Unassigned to Assigned (to an esanalyst?) and the status changed from New to In Progress. From there the Enterprise Security analyst would troubleshoot the issue. If there is some action that needs to be taken, the status might be changed to Pending, or it might go straight to Resolved.
To move from Resolved to Closed the event must be verified by another party (admin).
Important: Layout your workflow process and the status types needed for your workflow configuration before entering any status information the into Splunk App for Enterprise Security.
You can disable a workflow status type in the Splunk App for Enterprise Security, but you cannot delete a status once it has been entered. Contact Splunk Professional Services if you have questions.
User authorization
Authorization for each status transition can be assigned to specific user roles. For example, perhaps an esadmin can close an issue, while an esanalyst can assign an event and change its status from New to In Progress.
See "Configure user roles" in this document for more information about user roles and their permissions.
| New notable event | Notable event suppression |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.0, 3.0.1
 Download manual
Download manual
Feedback submitted, thanks!