Notable event suppression
In some cases, you may want to prevent certain types of notable events from appearing on the Incident Review dashboard or contributing to alert thresholds. To do this, you need to create a search that finds those notable events and suppresses them.
Create a notable event suppression
To create a suppression:
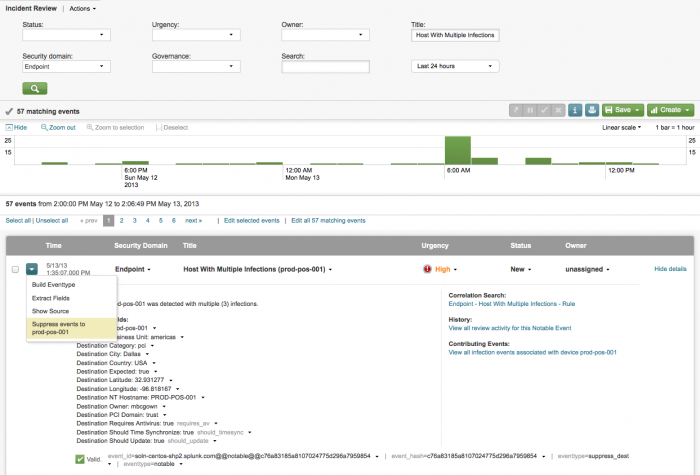
1. Find the notable event that you want to suppress in the Incident Review (or other search dashboard).
2. From the drop-down menu next to the notable event, select "Suppress events to ..." This opens the edit panel.
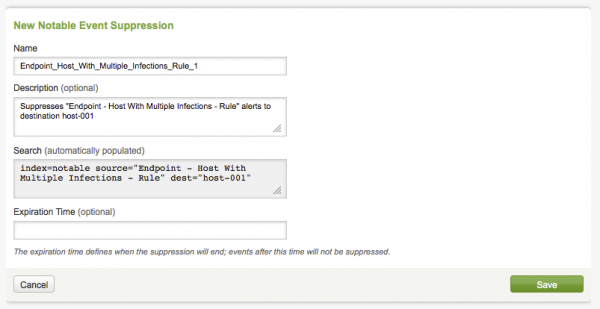
Review the contents of the fields. Add an expiration time if you want.
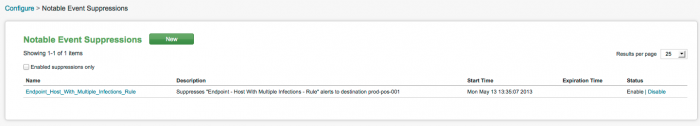
3. Click Save. The new notable event suppression is listed on the
Notable events from this search to this host will now be suppressed. Click on Notable Event Suppressions on the Configuration panel to review the status of events on the Notable Event Suppression panel.
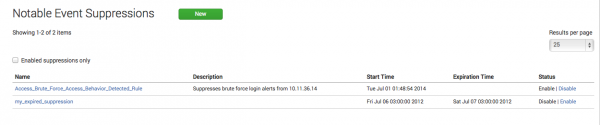
Suppressed notable events
When a notable event is suppressed, it suppresses events that are already in the notable index that you do not want to appear on the dashboards.
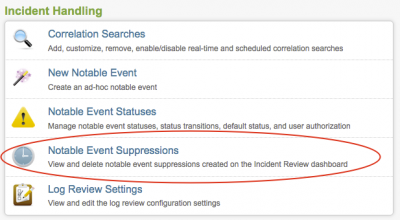
To view, modify, or delete notable event suppressions, use Notable Event Suppressions
Go to Configure > Notable Event Suppressions.
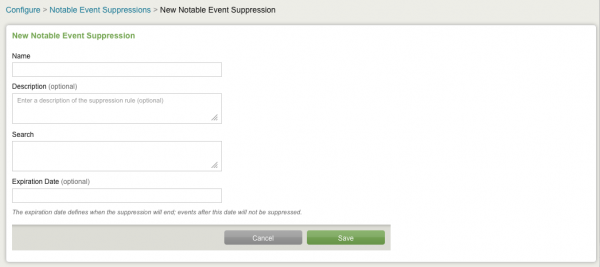
Manually create a notable event suppression
To create a notable event suppression from the Configure panel:
1. Go to Configure > Notable Event Suppressions
2. Click on New to create a new notable event suppression.
3. Add information to the fields and click Save.
See "Create a notable event suppression" for information about how to create a notable event suppression from a notable event in a search panel.
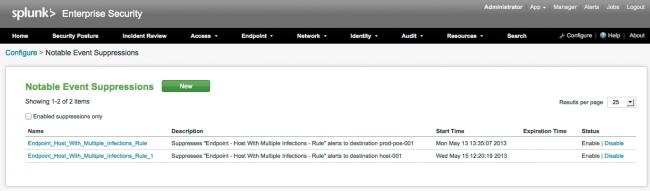
Edit notable events suppressions
To edit an individual notable event suppression:
1. Go to Configure > Notable Event Suppressions.
2. Click the name of the event to edit.
3. In the editor, make the desired changes.
4. Click Save.
To disable (or enable) an individual notable event suppression:
1. Click on the label next to the event name to enable or disable individual notable event suppressions.
2. Click Save.
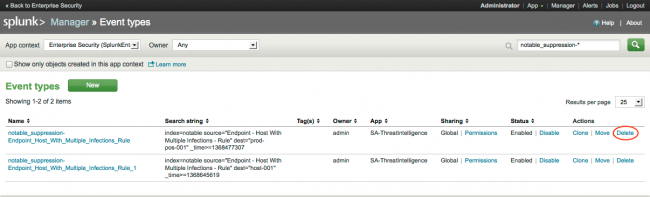
Remove a notable event suppression
To remove an individual notable event suppression:
1. Choose Settings > Event types.
2. Search for the the suppression event you want to remove (notable_suppression-<suppression_name>).
3. Click Delete next to the suppression name.
4. Click Save.
Suppress notable events from new correlation searches
If you create a new correlation search in the Splunk App for Enterprise Security, follow these steps so that you will to be able to suppress notable events from that search.
Step 1: Determine what fields to suppress on
First, determine what fields to use for suppression. You can suppress on combination of fields. For example, if you suppress on the destination and app fields, the suppression only applies to notable events for the given correlation search, if the search matches both dest and app fields.
View the available workflow actions by viewing the suppression workflow actions in $SPLUNK_HOME/etc/apps/SplunkEntepriseSecuritySuite/default/workflow_actions.conf. You also can view these in Settings > Fields > Workflow actions by searching for those that start with "suppress_" and exist in the SplunkEnterpriseSecuritySuite context. The fields used for suppresssion are indicated by the naming convention. The workflow action "suppress_dest:signature" allows suppression on the dest and signature fields.
Note: Suppressions will suppress all events that have matching values in all of the fields.
Step 2: Create an eventtype
Create an eventtypes.conf entry that matches an eventtype in your suppression entry. Name the stanza so that it will be easy to remember the of the suppression usage. We recommend a naming convention of "suppress_rule_<correlation search name>" to make it easy to find eventtypes used for suppressing correlation searches.
Set the search to look for a source field that matches your correlation search. Place this eventtype in the SplunkEnterpriseSecuritySuite app. Below is an example of an eventtypes.conf entry for suppressing a rule named "Network - Change in Critical App - Rule":
search = source="Network - Change in Critical App - Rule"
Step 3: Associate the eventtype with a workflow action
Next, associate the eventtype to a workflow action that will add a menu item for suppressing the notable event. To do this, edit the workflow action and add the additional eventtype. This can be done in Settings > Fields > Workflow actions. Note that the eventtypes are comma separated.
Step 4: Create a new workflow (optional)
If you want to filter on a unique combination of fields that are not currently included in a workflow, you need to create a new workflow action. To do this you will need to create a URL. The URL needs to point to the suppression editor and needs to include the following fields:
- search: search argument that matches the events that ought to be suppressed
- description: the description that will be assigned to the suppression
- name: the default name for the suppression
The URL consists of the following along with the above fields added as GET arguments:
Use the format from the WorkflowMaker file appendix in this manual to create the URL. Save it as workflowMaker.html to create this URL.
Create the workflow action in workflowactions.conf. Start with the following:
display_location = event_menu
eventtypes = suppress_rule_change_in_critical_app
fields = source,src
label = Suppress this event from $src$
link.method = get
link.target = blank
link.uri = /app/SplunkEnterpriseSecuritySuite
/notable_suppression_new?search=index%3Dnotable%20src
%3D%22$src$%22%20source%3D%22$source$%22&
wz&description=Suppresses%20brute%20force%20login%20alerts%20from%20$src$
&start_time=$_time$&name=$source$
type = link
Set the name of the stanza to something meaningful, beginning with "suppress".
Now add the following fields:
- display_location: should be set to event_menu
- eventtypes: set to the eventtype created above
- fields: include source as well the other fields to suppress on
- label: set this to a human readable label
(this will be display as the text in the context menu on the Incident Review dashboard) - link.method and link.target: should be "get" and "blank" respectively
- link.uri: set to the URI of the suppression editor with the search, description, and name fields included
The completed stanza can look like something like:
display_location = event_menu
eventtypes = suppress_rule_change_in_critical_app
fields = source,src
label = Suppress this event from $src$
link.method = get
link.target = blank
link.uri = /app/SplunkEnterpriseSecuritySuit/notable_suppression_new?search=index%3Dnotable%20src%3D%22$src$%22%20source%3D%22$source$%22wz&description=Suppresses%20brute%20force%20login%20alerts%20from%20$src$&start_time=$_time$&name=$source$
type = link
Audit suppression activity
The Notable Event suppression activity is shown in the Suppression Audit dashboard.
To audit suppression activity go to Audit > Suppression Audit.
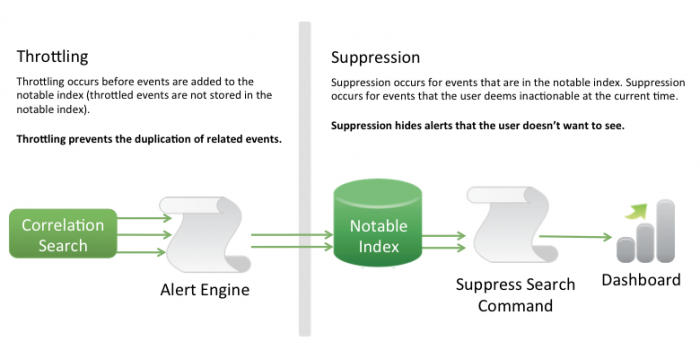
Throttling
Throttling occurs before events are added to the notable event index. This means that throttled events are not added to the notable index.
Throttling prevents the duplication of related events.
Suppression
Suppression is applied to events that are already in the notable index. Suppression is used for events on which you cannot currently act and do not want to appear in dashboards.
Suppression hides alerts that you don't want to see.
| Notable event statuses | Configure log review settings |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.0, 3.0.1
 Download manual
Download manual
Feedback submitted, thanks!